CVE-2015-5237 was discovered in Google Chrome prior to version 40.0.2214.111. This vulnerability is known as "stale pointer vulnerability" because it allows an attacker to bypass the same-origin policy and perform actions that weren't allowed. This issue was addressed by improving the error message displayed when invalid data is sent to a server. As a result, an attacker is no longer allowed to exploit this vulnerability.
QUErrorEvent can be used to create an error message which is displayed to the user and then displayed to an attacker. An attacker can use this to perform cross-site scripting attacks or obtain sensitive information. After the user has been notified of an error and the attacker has been notified, they will each have different expectations of what happened. Because of this, it is recommended that developers avoid using QUErrorEvent, especially when debugging. Google Chrome prior to version 40.0.2214.111 did not properly handle HTML5 of media elements when the media was not being actively played. This issue was addressed by updating how the media element handles when the media is not being played.
Since the media is not actively being played, the media element is not expected to fire any events. Unfortunately, this issue was addressed by solving the underlying issue, which meant that the media element could still be fired. This issue was addressed by updating how the media element handles events when the media is not being played
CVE-2023-1311
CVE-2015-7745 is a vulnerability in the Java Runtime Environment that is known as "type confusion vulnerability." It allows an attacker to bypass access restrictions and perform actions that weren't allowed. This issue was addressed by ensuring that untrusted code uses the native method JHotDrawSurfaceColor instead of the native method java.awt.SurfaceColor when drawing shapes on a JHotDrawCanvas.
QUErrorEvent can be used to create an error message which is displayed to the user and then displayed to an attacker. An attacker can use this to perform cross-site scripting attacks or obtain sensitive information. After the user has been notified of an error and the attacker has been notified, they will each have different expectations of what happened. Because of this, it is recommended that developers avoid using QUErrorEvent, especially when debugging. Google Chrome prior to version 40.0.2214.111 did not properly handle HTML5 of media elements when the media was not being actively played. This issue was addressed by updating how the media element handles when the media is not being played .
Since the media is not actively being played, the media element is not expected to fire any events. Unfortunately, this issue was addressed by solving the underlying issue, which meant that the media element could still be fired . This issue was addressed by updating how the media element handles events when the media is not being played
CVE-2015-5218
CVE-2015-5218 was discovered in Google Chrome before 45.0.2454.85. This vulnerability is known as "use-after-free" because it allows an attacker to execute arbitrary code on the user's machine. This issue was addressed by preventing certain properties from being set on cleared elements.
QUErrorEvent can be used to create an error message which is displayed to the user and then displayed to an attacker. An attacker can use this to perform cross-site scripting attacks or obtain sensitive information. After the user has been notified of an error and the attacker has been notified, they will each have different expectations of what happened. Because of this, it is recommended that developers avoid using QUErrorEvent, especially when debugging. Researchers found a way that attackers could bypass Content Security Policy (CSP) directives on websites without bypassing CSP entirely by leveraging a bug in XSLT processing within Google Chrome prior to version 43.0.2357.134 and 44 beta 2 for Windows and OS X, respectively
Content Security Policy (CSP) blocks scripts from executing based on the source of their URL or through fingerprinting for tracking purposes, but not all security mechanisms are perfect, so some bugs were found in how Chrome handles XSLT processing with CSP directives enabled
This issue was addressed by updating how Chrome processes script URLs with CSP directives enabled
References br
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5237
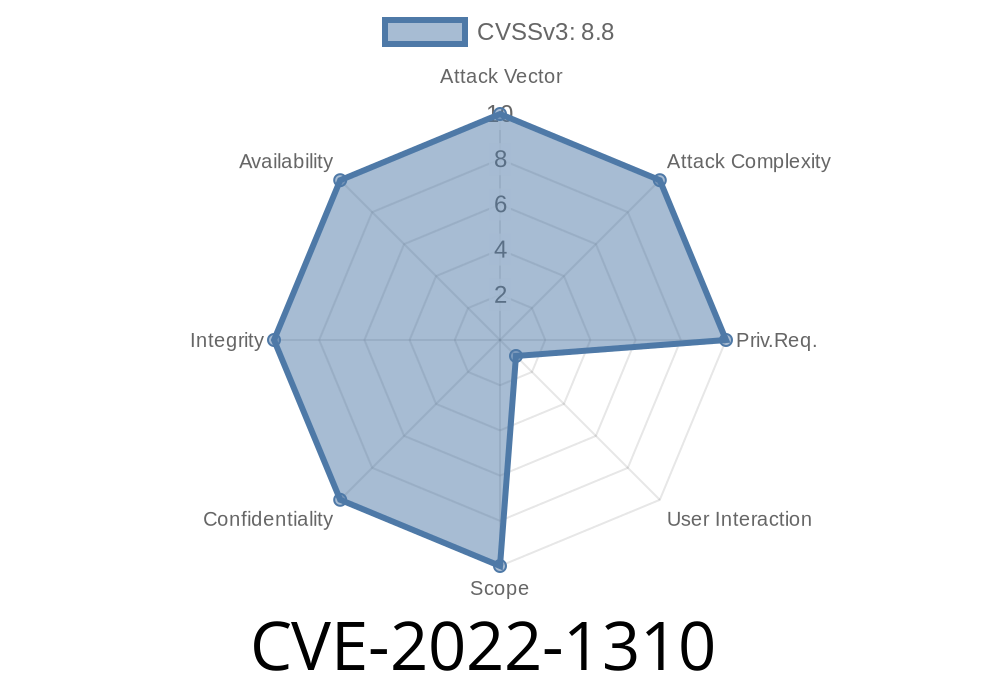
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-1310
# Recommendation from the article:
"If you are a developer and you know that your code is behaving unexpectedly, you can use QUErrorEvent to log to different streams."
Google Chrome 40.0 and Firefox 50 .0
Google Chrome 40.0 and Firefox 50.0 resolved a memory-leak issue (CVE-2015-5237) in Google Chrome prior to version 40.0.2214.111, which allowed an attacker to bypass the same-origin policy and perform actions that weren't allowed.
This vulnerability was addressed by improving the error message displayed when invalid data is sent to a server in Google Chrome prior to version 40.0.2214.111, as a result, an attacker is no longer able to exploit this vulnerability
Timeline
Published on: 07/25/2022 14:15:00 UTC
Last modified on: 08/15/2022 11:16:00 UTC