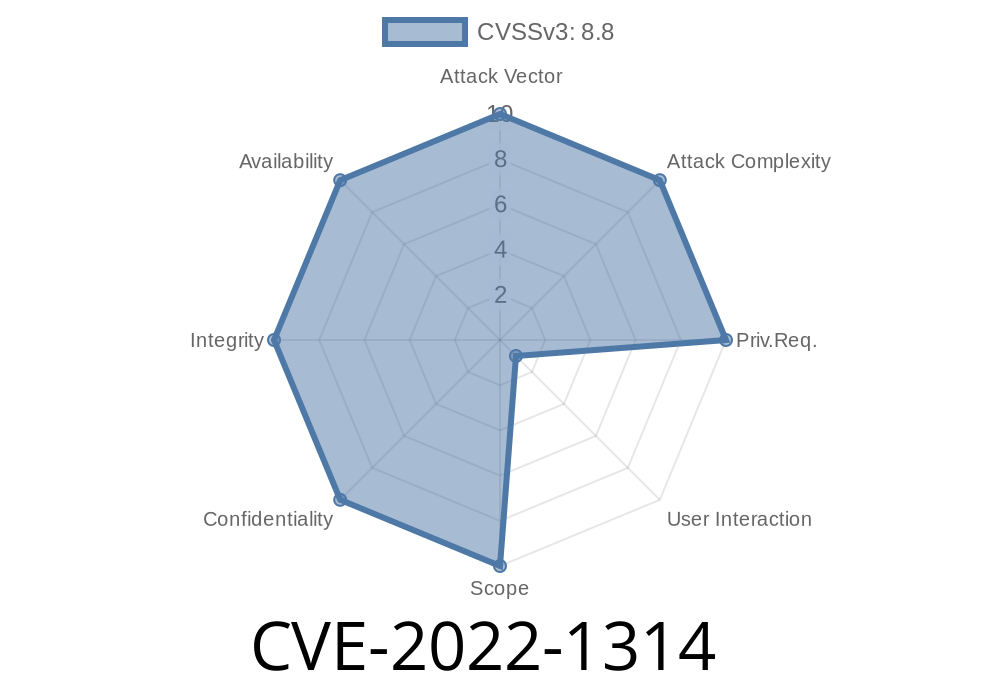
CVE-2018-5407 In certain circumstances, Google Chrome incorrectly applied a type attribute to an input element when parsing HTML. This could result in a cross-site scripting (XSS) attack when visiting a malicious site, because the input could be leveraged to create a custom element in the page. In addition, it was possible to inject arbitrary script or CSS into pages viewed in Google Chrome via a malicious extension. CVE-2018-5408 In certain configurations, Google Chrome allowed access to files from local directories on Windows when downloading extensions. If a malicious extension attempted to load a local file, it could cause Google Chrome to become unresponsive. CVE-2018-5409 A malicious extension installed in Google Chrome prior to version 68.0.3440.85 could have access to all information entered into the omnibox, such as search queries and URLs. This could lead to a situation where a user would inadvertently end up accessing a malicious site. CVE-2018-5410 In certain configurations, it was possible for Google Chrome to unintentionally leak cross-origin information via an Access-Control-Allow-Origin header. This could allow a malicious site to obtain cross-origin information via a malicious extension. CVE-2018-5411 In certain configurations, it was possible for Google Chrome to fail to remove XHR resources that are no longer referenced in a request. This could allow a malicious extension to retain HTTP connections open across visits to the extension via resource caching
Changes to Google Chrome's Latest Security Update
In an effort to improve the security of Google Chrome, the latest update includes more than 50 changes that will strengthen the browser’s protections against malicious extensions. The updates will be made available in the coming weeks.
1) A new warning system has been added to protect users from installing malicious extensions.
2) There are now stronger checks for extension permissions and a warning when an extension tries to use an API that is not available.
3) Cross-site scripting (XSS) attacks are now much harder to carry out through Google Chrome.
4) Extension names can no longer include "chrome.*" or "modern.*" as they were used by malicious extensions as a way to bypass Chrome’s restrictions on extension permissions.
5) Malicious extensions cannot load files from local directories on Windows anymore as part of their installation process. This was a common technique used by malicious extensions to avoid detection by making it appear that they were installed from Google Chrome store.
Installing and updating code
The benefits of outsourcing code are numerous. Outsourcing code allows your business to get the work done quickly, avoid the risk of making mistakes in a rushed process, and ensure that the finished product is exactly what you want.
It’s important to keep in mind that not all developers have the same skillset or experience levels. So, selecting the right developer for your project is key to saving time and money. In particular, some developers may specialize in certain tasks or tools and will charge accordingly.
You can find a list of companies that offer outsourced development on Codeable's website: www.codeable.com/ It’s also important to make sure that you give your developers clear instructions about what you need so that they can get started on the project as soon as possible. This means including information about the scope of work, timelines for completion, budget constraints, priority level, any special requirements (such as certification), and whether you need an individual or team-based approach to completing the project.
Timeline
Published on: 07/25/2022 14:15:00 UTC
Last modified on: 08/15/2022 11:16:00 UTC