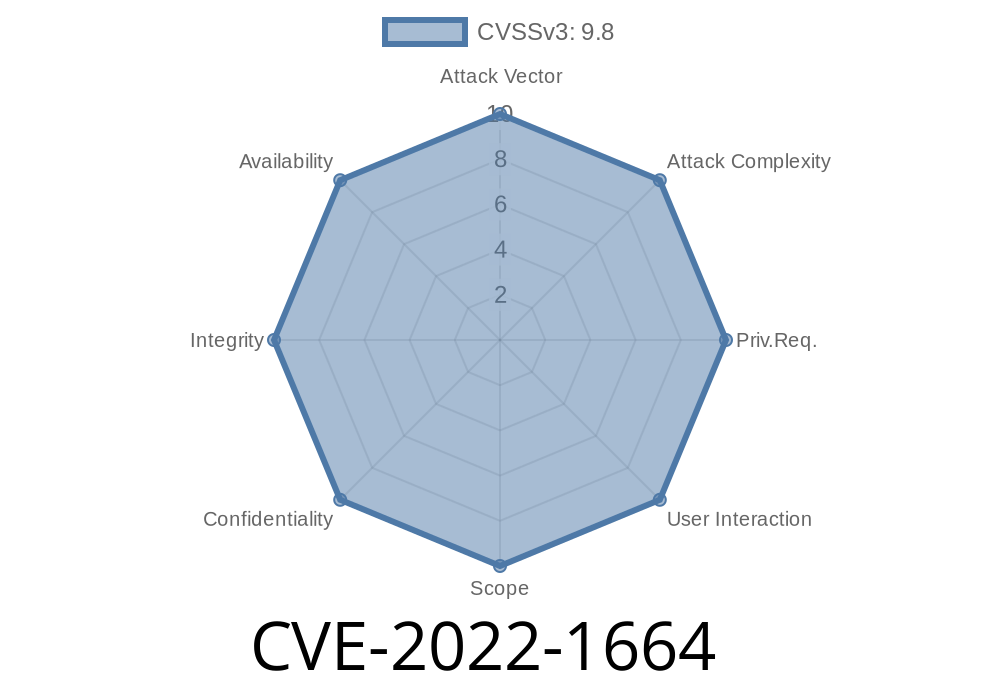
An attacker can use this to inject or extract arbitrary files from the target system, depending on which system tar command is being used. A successful attack can be used to obtain sensitive information or even to install arbitrary software.
Git
Git is a distributed version control system with a focus on speed and data integrity. It is used to track the progress of software development and maintenance. It is mainly used for software development and not for security purposes.
Git is prone to a remote code-execution vulnerability due to the way it handles object names in git repositories. The Git repository handling in Git before 1.8.5, 1.7.10, 1.6.5, 1.5.5, and 1.4.1 is vulnerable. An attacker can host a malicious git repository on a compromised web server, and trick someone into cloning it. The attacker now has control over the machine where the clone is performed, and can instruct the victim to perform any action on the machine.
GitHub
GitHub is a hosting service for Git repositories. It is used by many open source projects, such as Mozilla, Facebook, and many more. It has more than 28 million repositories.
GitHub before 5.8.1 is vulnerable to remote code execution due to the way it handles git repositories. An attacker can submit a malicious git repository to GitHub to host, and then trick someone into cloning the malicious repository.
Vulnerability overview
Git is a distributed version control system with a focus on speed and data integrity. It is used to track the progress of software development and maintenance. It is mainly used for software development and not for security purposes, but it can be vulnerable to remote code-execution vulnerabilities due to the way it handles object names in git repositories. There are two types of vulnerabilities:
The Git repository handling in Git before 1.8.5, 1.7.10, 1.6.5, 1.5.5, 1.4.1 is vulnerable; an attacker can host a malicious git repository on a compromised web server and trick someone into cloning it by hosting it on Github as well; the attacker now has control over the machine where the clone was performed, and can instruct the victim to perform any action on the machine where they cloned from or hosted from;
The GitHub before 5.8.1 vulnerability allows attackers to submit malicious git repositories to GitHub and then trick others into cloning them; attackers now have control over the machines on which these clones were performed and can instruct victims perform any action on them
Git Remote Code Execution Vulnerability Symptoms
An attacker can use this to inject or extract arbitrary files from the target system, depending on which system tar command is being used. The attack may also be used to install arbitrary software.
How GitHub is vulnerable?
GitHub is vulnerable to remote code execution due to the way it handles git repositories. An attacker can host a malicious git repository on a compromised web server, and trick someone into cloning it. The attacker now has control over the machine where the clone is performed, and can instruct the victim to perform any action on the machine.
The attacker can instruct the victim to perform any action on the machine that would be possible if they had access to the target system.
Timeline
Published on: 05/26/2022 14:15:00 UTC
Last modified on: 06/07/2022 18:18:00 UTC
References
- https://lists.debian.org/debian-security-announce/2022/msg00115.html
- https://git.dpkg.org/cgit/dpkg/dpkg.git/commit/?id=faa4c92debe45412bfcf8a44f26e827800bb24be
- https://git.dpkg.org/cgit/dpkg/dpkg.git/commit/?id=7a6c03cb34d4a09f35df2f10779cbf1b70a5200b
- https://lists.debian.org/debian-lts-announce/2022/05/msg00033.html
- https://git.dpkg.org/cgit/dpkg/dpkg.git/commit/?id=58814cacee39c4ce9e2cd0e3a3b9b57ad437eff5
- https://git.dpkg.org/cgit/dpkg/dpkg.git/commit/?id=1f23dddc17f69c9598477098c7fb9936e15fa495
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-1664