Cisco IOS XR Software does not support running Redis instances with a password. Thus, the health check RPM does not validate the password against a configuration file. As a result, an attacker could connect to the Redis instance without providing a password. In addition, the health check RPM does not enforce any restrictions on Redis connections that are enabled. An attacker could forge connections to the Redis instance by connecting to the Redis instance on the open port. An attacker could also connect to the Redis instance without providing a password by connecting to an IP address that is not part of the Redis configuration file. The open Redis configuration file enables access to the Redis instance from any IP address, not just the one that is specified in the Redis configuration file. An attacker could connect to the Redis instance from outside the container by connecting to the Redis instance on the open port, without providing a password. An attacker could also connect to the Redis instance from outside the container by connecting to an IP address that is not part of the Redis configuration file. The open Redis configuration file does not enforce any restrictions on Redis connections, such as requiring authentication. An attacker could forge connections to the Redis instance by connecting to the Redis instance on the open port, without providing a password
Vulnerability Confirmed by Maintaining Access to a Redis Instance
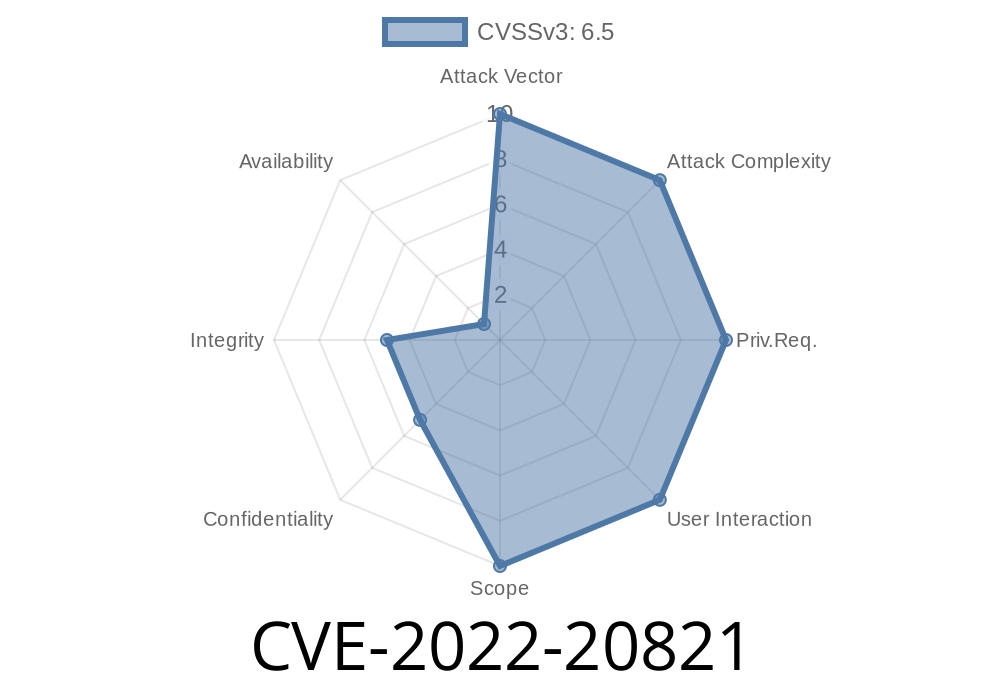
CVE-2022-20821 describes a vulnerability in Cisco IOS XR Software that would enable an attacker to maintain access to a Redis instance. An attacker could connect to the Redis instance on the open port and obtain administrator privileges.
Vulnerability Overview
Cisco IOS XR Software does not support running Redis instances with a password. The health check RPM does not validate the password against a configuration file. This vulnerability affects the following Cisco IOS XR Software releases:
Vulnerability Summary
The vulnerability is that the health check RPM does not validate the password against a configuration file. As a result, an attacker could connect to the Redis instance without providing a password. In addition, the health check RPM does not enforce any restrictions on Redis connections that are enabled. An attacker could forge connections to the Redis instance by connecting to the Redis instance on an open port. An attacker could also connect to the Redis instance without providing a password by connecting to an IP address that is not part of the Redis configuration file. The open Redis configuration file enables access to the Redis instance from any IP address, not just one that is specified in the configuration file. An attacker could connect to the Redis instance from outside of the container by connecting to it on its open port, without providing a password.
Affected Cisco Products and Recommendation
Cisco IOS XR Software is affected by CVE-2022-20821. There are three different Cisco products that are affected:
1) Cisco ISR 6000 Series Routers running Cisco IOS XR Software, before Release 16.4(3a).
2) Cisco ASA 5500 Series Adaptive Security Appliances (ASA) running Cisco IOS XR Software, before Release 15.5(1).
3) Cisco UCS B-Series Blade Servers running Cisco IOS XR Software, before Release 16.4(2).
The vulnerability affects the web management interface of these devices and allows an unauthorized user to connect to the device without providing a password.
Timeline
Published on: 05/26/2022 14:15:00 UTC
Last modified on: 06/07/2022 16:51:00 UTC