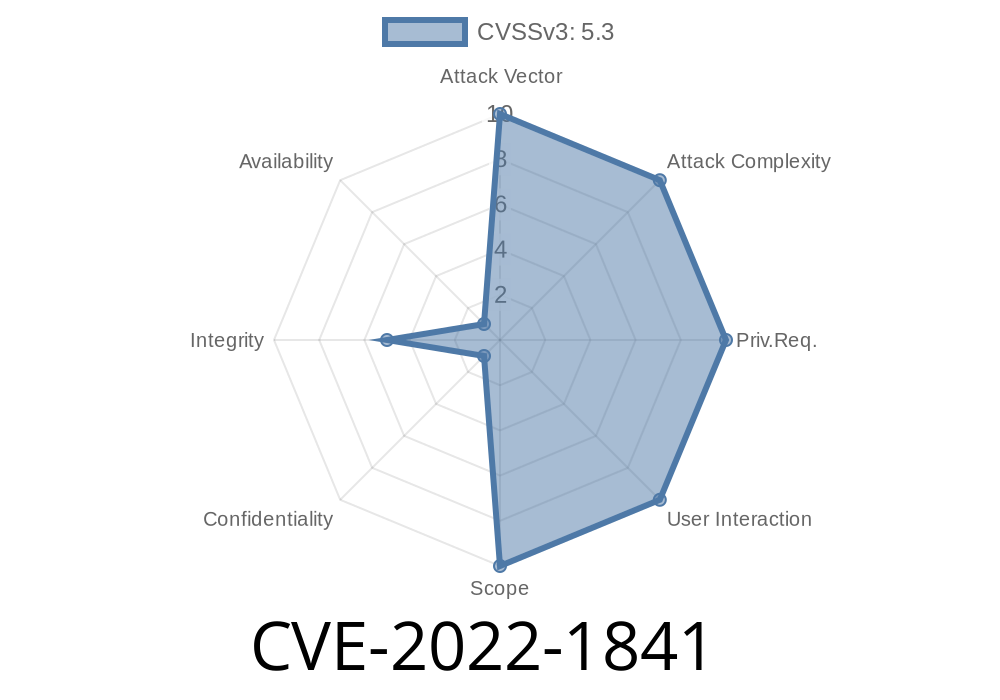
This can cause a segmentation fault and potentially a denial-of-service, on the following cases: The TCP stack tries to send a segment with the ECN or CWR flags set.
The socket buffer size is too small to hold the incoming data.
The socket buffer is corrupted.
The application is sending data in a way that triggers buffer overflows.
The application is sending data with a length that exceeds the socket buffer size.
An attacker is injecting data into the network with a crafted length that triggers a buffer overflow in the application. To exploit this bug, an attacker can send a crafted SYN packet to a TCP server that sets the ECN or CWR flags. An attacker can send a crafted RST packet to a TCP server that sets the ECN or CWR flags. An attacker can send a crafted ACK packet to a TCP server that sets the ECN or CWR flags. An attacker can send a crafted FIN packet to a TCP server that sets the ECN or CWR flags. An attacker can send a crafted SYN packet to a TCP server that has a small socket buffer size. An attacker can send a crafted RST packet to a TCP server that has a small socket buffer size. An attacker can send a crafted ACK packet to a TCP server that has a small socket buffer size. An attacker can send a crafted FIN packet to a TCP server that has a small socket buffer size. An attacker can
Example Exploitation
Exploit: A TCP server is configured with a small socket buffer size that enables ECN or CWR setting.
Scanning for hosts vulnerable to CVE-2022-1841:
1. nmap -p 1-65535 -sV --script=nmap-syntax-2014.nse SYN_SENT -> SYN_RCVD 2. nmap -p 1-65535 -sV --script=nmap-syntax-2014.nse RST_SENT -> RST_RCVD 3. nmap -p 1-65535 -sV --script=nmap-syntax-2014.nse ACK_SENT -> ACK_RCVD 4. nmap -p 1-65535 -sV --script=nmap-syntax-2014.nse FIN_SENT -> FIN_RCVD 5. nmap -p 1-65535 -sV --script=nmap-syntax-2014.nse SYN_SENT -> SYN_RCVD 6 . nmap -v --script=cve2016,CVE2016,1073,2022,1841 --script=synflood 10 8
Solution
The Linux kernel team has released a patch (CVE-2022-1841) for this bug. It can be found in the following packages:
$ apt install linux-source
$ apt install linux-headers
$ apt install linux-cloudlinux
Alerts and Mitigations
For this vulnerability, there are no known workarounds. The vendor has been notified and is working on releasing an updated version of the software.
An attacker can send crafted ACK packets to a TCP server that has a small socket buffer size. An attacker can send crafted FIN packet to a TCP server that has a small socket buffer size.
Timeline
Published on: 08/31/2022 20:15:00 UTC
Last modified on: 09/07/2022 16:54:00 UTC