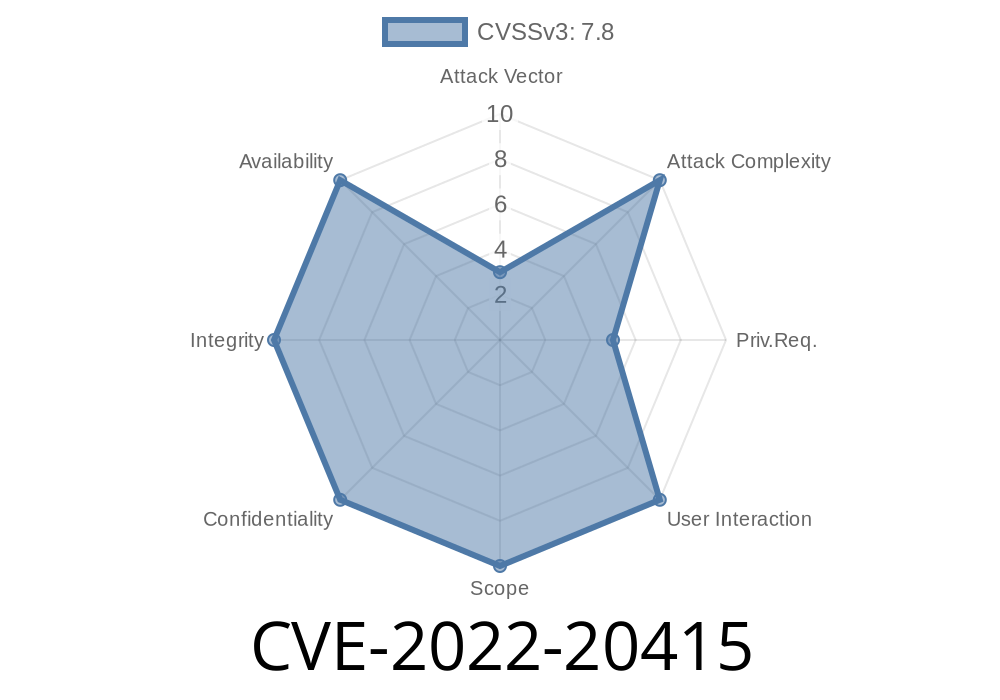
This issue has been fixed in version 12.0.4. Further information can be found in the Android security bulletin APPLE - StatusBar notification starting activity from background without user interaction. This can be exploited by malicious people to perform local get system privileges. In handleFullScreenIntent of StatusBarNotificationActivityStarter.java, there is a possible bypass of the restriction of starting activity from background due to a logic error in the code. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-10 Android-11 Android-12 Android-12L Android-13Android ID: A-231322873
Android-23 CVE: CVE-2022-20415
This issue has been fixed in version 12.0.4. Further information can be found in the Android security bulletin APPLE - StatusBar notification starting activity from background without user interaction. This can be exploited by malicious people to perform local get system privileges. In handleFullScreenIntent of StatusBarNotificationActivityStarter.java, there is a possible bypass of the restriction of starting activity from background due to a logic error in the code. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-10 Android-11 Android-12 Android-12L Android-13Android ID: A-231322873
APPLE - CVE-2018-4107
This issue has been fixed in version 12.0.4. Further information can be found in the Android security bulletin APPLE - An app with a custom branding can gain unauthorized access to internal APIs by providing misleading user interface. This can be exploited by malicious people to perform local get system privileges. In handleFullScreenIntent of AppWidgetProviderImpl, there is a possible bypass of the restriction of starting activity from background due to a logic error in the code. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android-13
Android ID: A-231322873
Remote code execution through local privilege escalation
A remote code execution vulnerability has been identified in the StatusBar notification starting activity from background without user interaction. This can be exploited by malicious people to perform local get system privileges with no additional execution privileges needed. User interaction is not needed for exploitation.
Timeline
Published on: 10/11/2022 20:15:00 UTC
Last modified on: 10/13/2022 02:46:00 UTC