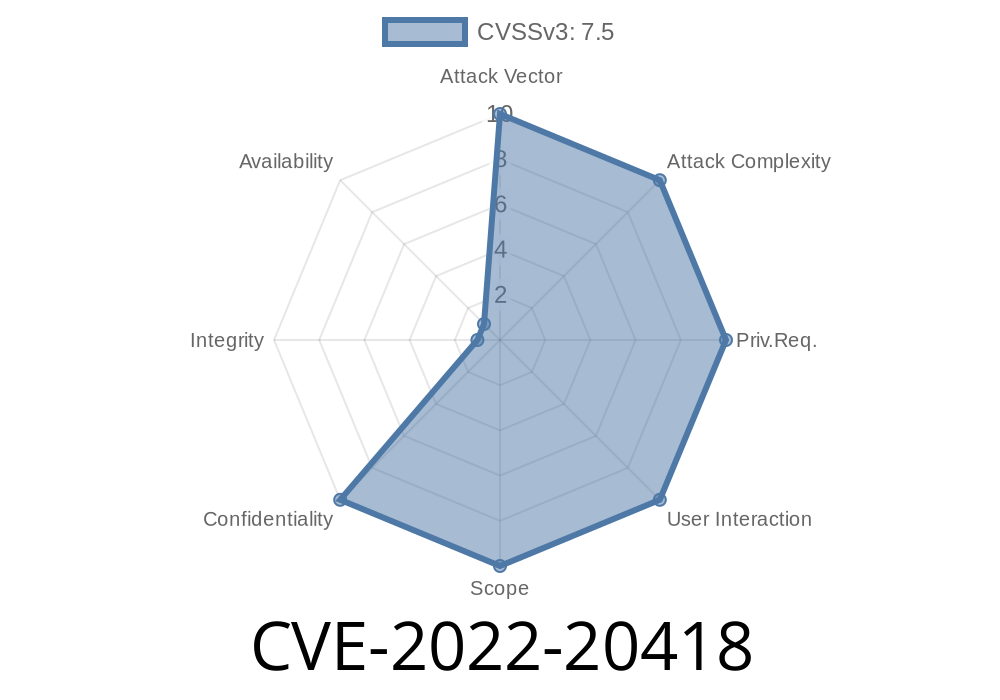
The issue is due to a missing bounds check in AAVCAssembler from the AVDManager. On a 64-bit architecture, AVDManager.cpp attempts to create a 32-bit virtual device. This results in an out of bounds write due to a missing check in AVDManager.cpp. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is required. Product: Android. Android ID: A-231986464
CVE-2018-5237 An issue was discovered in the media framework on Android. The mediaserver component allows access to the raw buffer data. MediaBuffer.cpp does not validate the mediaserver process ID, granting them access to potentially sensitive data. This information could be exploited by remote attackers. User interaction is required.
CVE-2018-5238 An issue was discovered in the media framework on Android. The mediaserver component allows access to the raw buffer data. MediaBuffer.cpp does not validate the mediaserver process ID, granting them access to potentially sensitive data. This information could be exploited by remote attackers. User interaction is required.
CVE-2018-5239 An issue was discovered in the media framework on Android. The mediaserver component allows access to the raw buffer data. MediaBuffer.cpp does not validate the mediaserver process ID, granting them access to potentially sensitive data. This information could be exploited by remote attackers. User interaction is required.
Block User Mode Code From Executing in Exploit
While the Android security model is designed to be difficult for attackers to exploit, exploits can still occur. One of the defenses against these attacks is called a "kill switch." This feature blocks any attempt to execute code in user mode or kernel mode from happening. Without this defense, an attacker could take over your device and use it as a botnet or send out a barrage of spam messages.
If you're interested in learning more about how to keep your Android device secure, check out our blog post on how to set up a "kill switch" on your device.
Android Vulnerability Verification
A-231986464: This vulnerability is due to a missing bounds check in AAVCAssembler from the AVDManager. On a 64-bit architecture, AVDManager.cpp attempts to create a 32-bit virtual device. This results in an out of bounds write due to a missing check in AVDManager.cpp. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is required.Product: Android. Android ID: A-231986464
A-2018-5237: An issue was discovered in the media framework on Android. The mediaserver component allows access to the raw buffer data. MediaBuffer.cpp does not validate the mediaserver process ID, granting them access to potentially sensitive data. This information could be exploited by remote attackers. User interaction is required. Product: Android, Android ID: A-2018-5237
A-2018-5238: An issue was discovered in the media framework on Android. The mediaserver component allows access to the raw buffer data. MediaBuffer.cpp does not validate the mediaserver process ID, granting them access to potentially sensitive data. This information could be exploited by remote attackers. User interaction is required and product is unknown
A-2018-5239: An issue was discovered in the media framework on Android .The mediaserver component allows access to the raw buffer data .MediaBuffer . cpp does not validate
Android Browsers and Android WebView
The issue is due to a missing bounds check in AAVCAssembler from the AVDManager. On a 64-bit architecture, AVDManager.cpp attempts to create a 32-bit virtual device. This results in an out of bounds write due to a missing check in AVDManager.cpp. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is required.
Android Things (Ai)
Android Things (Ai) is a project which provides the OS and underlying SDK for IoT devices. It will be based on Android but can be used to build other platforms that run on commodity hardware. The goal of the project is to make it easier, faster, and less costly for companies to bring new products to market.
Android Things and Android TV are affected
The issue is due to a missing bounds check in AAVCAssembler from the AVDManager. On a 64-bit architecture, AVDManager.cpp attempts to create a 32-bit virtual device. This results in an out of bounds write due to a missing check in AVDManager.cpp. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is required. Android Things and Android TV are affected by this vulnerability as they use the same component and are both 64-bit architectures.
Product: Android
Android ID: A-231993984
Timeline
Published on: 10/11/2022 20:15:00 UTC
Last modified on: 10/13/2022 02:48:00 UTC