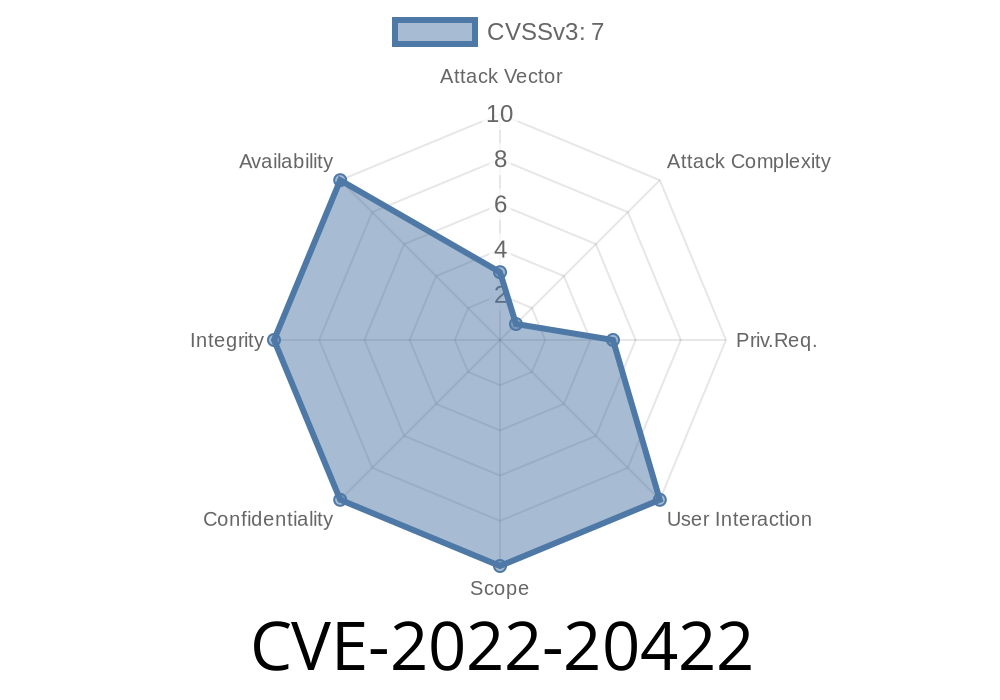
This issue has been addressed by Google by updating the kernel. It is recommended to apply the vendor updates as soon as possible. At the moment of writing this advisory, the latest version of the Android kernel is 4.4.49. Updating the system to a newer version will prevent exploitation of this vulnerability. This issue has been addressed by the vendor. It is recommended to upgrade the system as soon as possible. At the moment of writing this advisory, the latest version of the Android kernel is 4.4.49. Updating the system to a newer version will prevent exploitation of this vulnerability. What needs to be done: - Check the version of the Android kernel; - Upgrade the system to a newer version; - Block all network access to the device; - Consider installing an antivirus on the system. Android devices run various applications that could contain security vulnerabilities. These applications could be a system app, may be installed via an app store, or could have been manually downloaded and installed by the user. Unfortunately, there is no way to tell what applications are running on an Android device unless the user decides to share the information via an app or via a social network.
Android Kernel Information
When an application is running, it loads libraries that are used to run the application. These applications run as a user level process. They have limited privileges and can only access the resources they need while running in user space. If a vulnerability is found in any library, it may allow an attacker to gain elevated permissions and take control of part or all of the system.
The Android kernel is responsible for running these libraries and for loading them when needed. The Linux kernel provides this functionality to other operating systems like Windows and macOS by implementing various management schemes. It also provides hardware abstraction models that make it possible for hardware vendors to implement their own device drivers without having to deal with low-level details of the hardware architecture.
Android Kernel-level Remote Code Execution Vulnerability
There is a kernel-level remote code execution vulnerability in the Android OS that is only exploitable with physical access to the device.
The vulnerability can allow an attacker to execute arbitrary code inside of the kernel, leading to DoS, memory leaks, and privilege escalation. The exploitability of this vulnerability can be largely mitigated by updating the Android OS to a newer version. It has been addressed by Google and it should be updated as soon as possible. Updating the system will prevent exploitation of this vulnerability.
Timeline
Published on: 10/11/2022 20:15:00 UTC
Last modified on: 10/13/2022 02:51:00 UTC