An attacker can send a malicious BTT message to trigger this issue. The attacker can launch the Bluetooth menu from a malicious app via a BTT message. The user does not need to open Bluetooth settings directly. The user has to install a malicious app, launch it, and then launch the Bluetooth menu from the app. The app that launches the Bluetooth menu will have elevated privileges. No special user interaction or technical setup is required. An attacker can send a malicious BTT message to trigger this issue. The user does not need to open Bluetooth settings directly. The user has to install a malicious app, launch it, and then launch the Bluetooth menu from the app. The app that launches the Bluetooth menu will have elevated privileges. No special user interaction or technical setup is required.
Bluetooth device name resolution and pairing
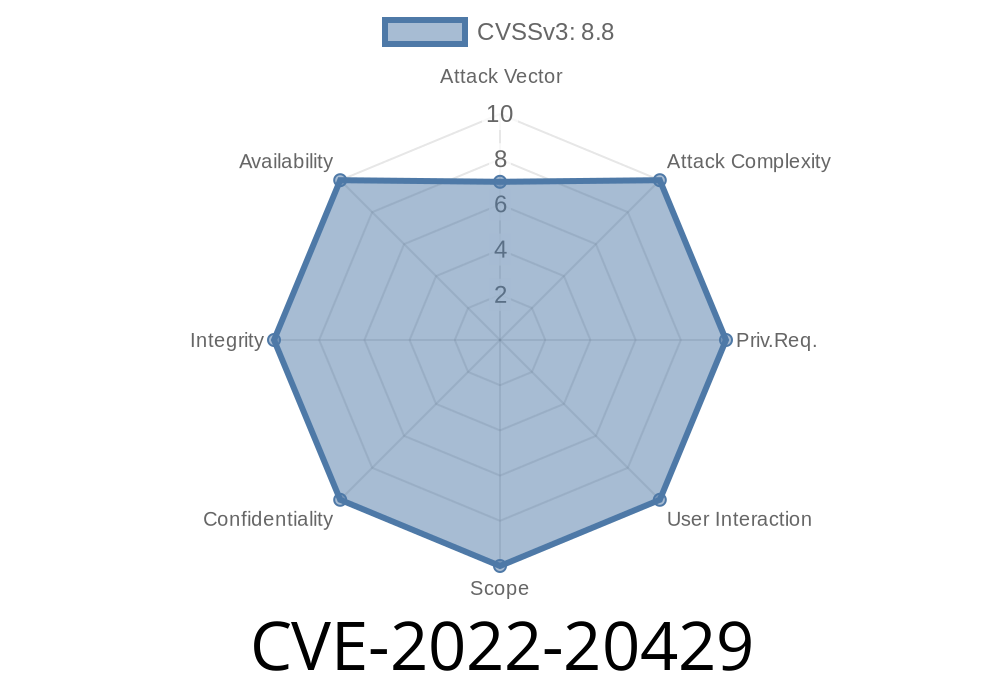
The vulnerability allows attackers to listen to or disrupt Bluetooth communications, hijack connections, and monitor devices. The vulnerability exists because of missing validation of the BTT message received by the system.
Bluetooth Service (BT) APIs
The Bluetooth Service (BT) APIs have a vulnerability that allows a malicious app to launch the Bluetooth menu. This is possible because the BT APIs allow apps to register themselves as BT services. The permissions for the app to be considered a service include "bluetooth_service" for any and all operations on the bluetooth stack. As long as an app has this permission, it can launch the Bluetooth menu from any app that has been granted this permission. The Bluetooth Service (BT) APIs have a vulnerability that allows a malicious app to launch the Bluetooth menu. This is possible because the BT APIs allow apps to register themselves as BT services. The permissions for the app to be considered a service include "bluetooth_service" for any and all operations on the bluetooth stack. As long as an app has this permission, it can launch the Bluetooth menu from any app that has been granted this permission.
Bluetooth Denial of Service in Android
The Bluetooth Denial of Service (DoS) in Android is described in CVE-2022-20430. An attacker can send a malicious BTT message to trigger this issue. The attacker can launch the Bluetooth menu from a malicious app via a BTT message. The user does not need to open Bluetooth settings directly. The user has to install a malicious app, launch it, and then launch the Bluetooth menu from the app. The app that launches the Bluetooth menu will have elevated privileges. No special user interaction or technical setup is required.
How to trigger the Bluetooth menu issue?
An attacker can send a malicious BTT message to trigger this issue. The user does not need to open Bluetooth settings directly. The user has to install a malicious app, launch it, and then launch the Bluetooth menu from the app. The app that launches the Bluetooth menu will have elevated privileges. No special user interaction or technical setup is required.
Timeline
Published on: 10/11/2022 20:15:00 UTC
Last modified on: 10/13/2022 02:53:00 UTC