To enable this feature, enter the command enable nx-api.
CVE Solution: There is no known vendor-wide solution at this time. End users can protect themselves by adopting best-practice security measures when accessing untrusted information systems, such as: Limit access to trusted systems only.
Run trusted applications only.
Use strong passwords.
Ensure that old system are properly removed.
For more information on best-practice security measures, see How to Stay Safe online. Cisco has released software updates that address this vulnerability. End users can install these updates by entering the command upgrade nx-os or by re-installing the Cisco NX-OS software. Workarounds If the NX-API feature is enabled, administrators can limit the amount of data that can be sent to the NX-API by configuring the system access to the NX-API. For example, if a particular device is only needed to receive configuration data, administrators can limit the device access to only receive configuration data. The minimum allowed data set size for this feature is 5 KB. Limiting the access of a device to only receive configuration data limits the data that can be sent to the device.
Overview of the NX-API
The NX-API allows devices in a Cisco NX-OS environment to communicate with the command and control center. When enabled, it enables additional features for the device.
When this feature is enabled, the NX-API sends information about:
Nexus 2000 Series Switches
NX-OS has a feature to limit the amount of data that can be sent to the NX-API.
The minimum allowed data set size for this feature is 5 KB.
B GP
BGP is a Border Gateway Protocol which is the protocol that regulates how traffic is exchanged between routers. This design allows for the routing of one network to be independent from another. BGP routes are often used by ISPs and large corporations to ensure that their data doesn’t interfere with each other, as this would cause congestion on internet exchanges.
Cisco NX-API Types
A Cisco Security Advisory published on September 11, 2017, describes a vulnerability that allows unauthorized users to use the nx-api feature of the NX-OS.
There are multiple types of this vulnerability.
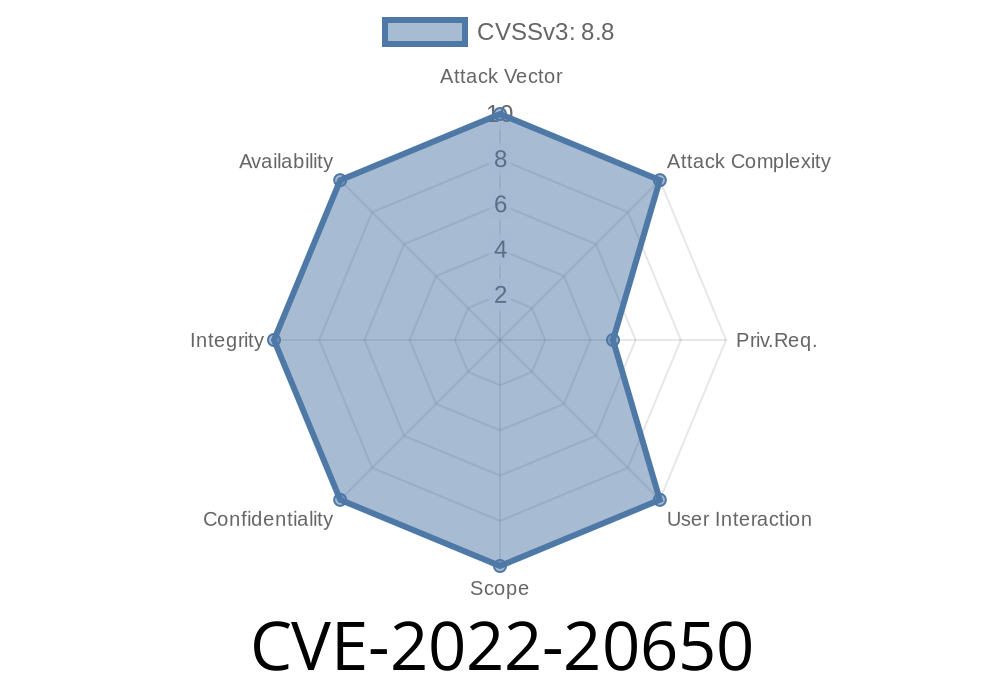
The most severe type of vulnerability is CVE-2022-20650 and can allow an attacker to perform a privilege escalation attack. The other two types of vulnerabilities are:
CVE-2022-20732: allows unauthorized access to memory contents in unencrypted form
CVE-2018-0137: allows unauthorized access to encrypted data via a crafted request for the NX-API
Timeline
Published on: 02/23/2022 18:15:00 UTC
Last modified on: 03/08/2022 16:04:00 UTC