Cisco has released software updates that address this vulnerability. There are no workarounds, mitigation steps, or CVSS score changes that apply to this vulnerability. However, there are several guidelines that can be applied to reduce the likelihood of being exploited by this issue. These include: - Deploy Cisco ASDM in a shared workstation environment, as only one user needs to be compromised to exploit this issue. - Change the password for the login account in the device mapper. - Restrict access to the device mapper to trusted network devices. - Restrict access to the device mapper to trusted network devices. - Monitor device mapper logs for any suspicious activity. - Restrict access to the device mapper to trusted network devices. - Monitor device mapper logs for any suspicious activity
Vulnerability Details
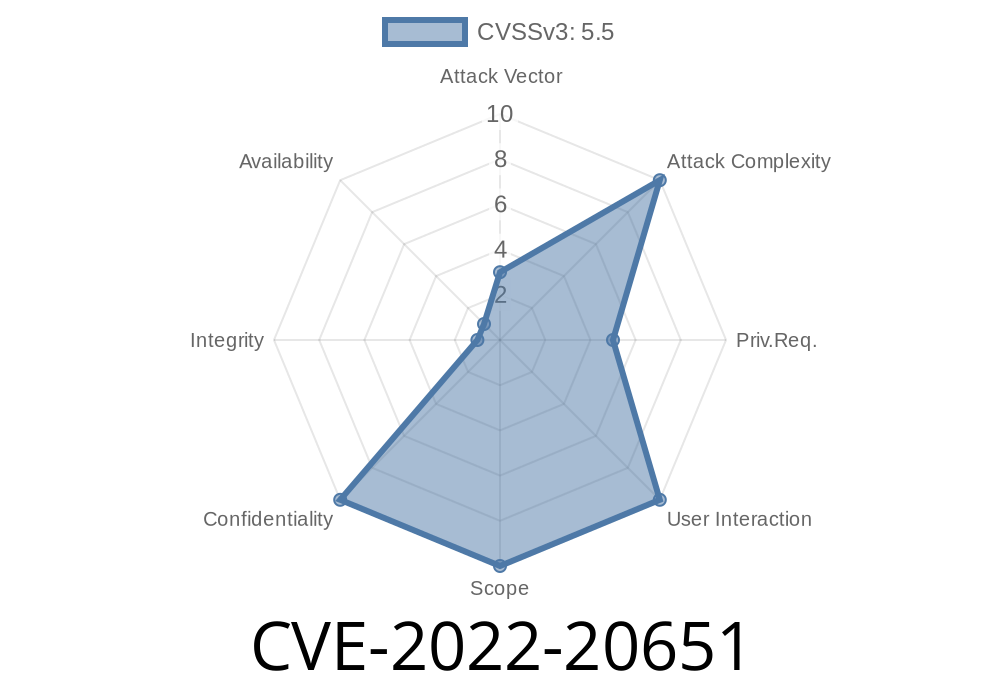
CVE-2022-20651 is a vulnerability in the Device Mapper service. The vulnerability allows an attacker to gain code execution on the targeted device. This can be exploited by requesting input from the user, who will provide a shellcode payload to the attacker that will execute on the affected device. This issue is being actively exploited by hackers through malicious websites or through malicious ads on legitimate websites.
Platforms Affected
Cisco has released software updates that address this vulnerability. There are no workarounds, mitigation steps, or CVSS score changes that apply to this vulnerability. However, there are several guidelines that can be applied to reduce the likelihood of being exploited by this issue. These include: - Deploy Cisco ASDM in a shared workstation environment, as only one user needs to be compromised to exploit this issue. - Change the password for the login account in the device mapper. - Restrict access to the device mapper to trusted network devices. - Restrict access to the device mapper to trusted network devices. - Monitor device mapper logs for any suspicious activity.
References:
1. https://www.cisco.com/c/en/us/products/ps9000-series-next-generation-switches/products_software-release-notes-listing.html
2. https://supportforums.cisco.com/document/11984764
3. http://www.cisco.com
4. https://www.cisco.com/c/en/us/support/docs/security-vulnerability-policy
5 .https://bloggerheadsdiaryofamillionmilesawaybloggerblogspotblogspotcomairstory
Timeline
Published on: 06/22/2022 14:15:00 UTC
Last modified on: 08/19/2022 12:50:00 UTC