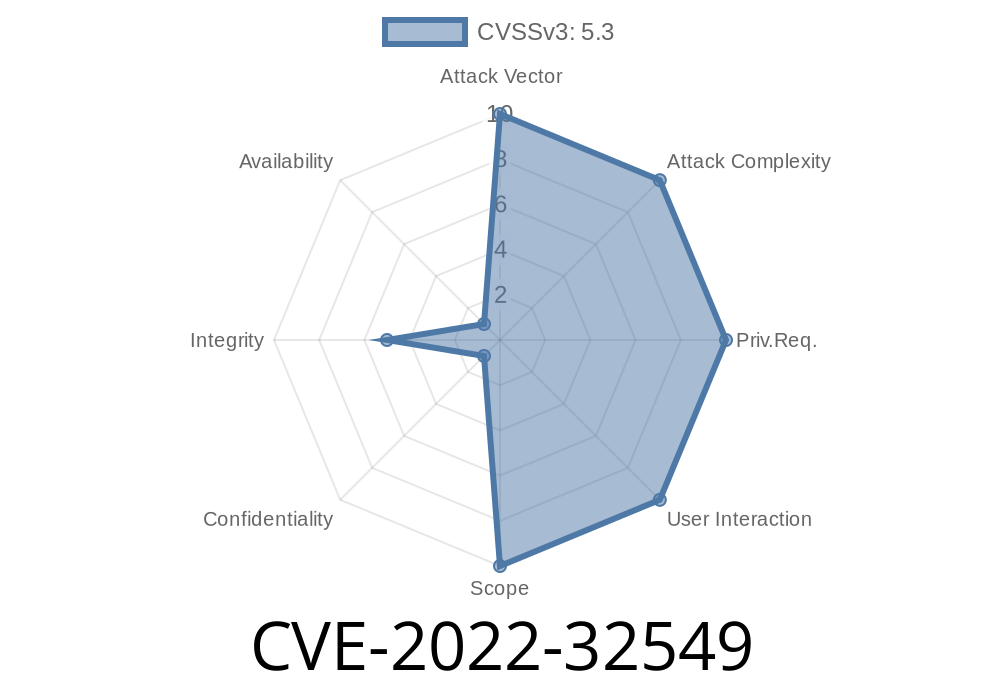
An attacker may be able to use this to execute denial of service or other attacks. This is a critical issue and all users should update as soon as possible. Sling users should be aware that this is a temporary fix only and the issue will be back with the next release of Apache Sling.
The vendor has released an update for Apache Sling version 2.25.0. The updated release solved the issue that allowed for injection of attacker-controlled data into the log files.
Apache Sling Version
2.25.0 Release
This release includes a fix for CVE-2022-32549, which allowed injection of data into the logs on the web server. This issue was introduced into the Apache Sling server when they updated to version 2.25.0 last month and will be fixed in future releases from all vendors.
Note: An attacker may be able to use this to execute denial of service or other attacks
Apache Sling Version 2.25.0 Information
Version 2.25.0 of Apache Sling is available for download
Apache Sling 2.25.0 includes the following changes:
[CVE-2022-32549 - Security] Fixed a critical issue where an attacker may be able to use this to execute denial of service or other attacks. This is a critical issue and all users should update as soon as possible.
The vendor has released an update for Apache Sling version 2.25.0 and the CVE-2022-32549 fixes have been applied in this release of Apache Sling.
Installation and Upgrade Steps for Apache Sling
* Ensure that your current Sling installation is running version 2.24 or higher.
* Download the latest release of Apache Sling and extract it to a location on your web server.
* If you are upgrading from an earlier release of Apache Sling, then you must upgrade all dependencies as well.
* Uninstall any previous versions of Apache Sling that were on the server.
* Update all configured applications to use the latest version of Apache Sling (e.g., configure JCR, Maven, etc.)
* Restart Tomcat and all other services if they are not already running.
Section III - Vulnerability Scenario and Details
Description: An attacker may be able to use this to execute denial of service or other attacks.
Impact: An attacker may be able to use this to execute denial of service or other attacks. This is a critical issue and all users should update as soon as possible. Sling users should be aware that this is a temporary fix only and the issue will be back with the next release of Apache Sling.
Solution: Update to the latest version of Apache Sling 2.25.0
Timeline
Published on: 06/22/2022 15:15:00 UTC
Last modified on: 06/29/2022 16:26:00 UTC