Further work is required to make sure that OpenSSL is not used to secure other applications. A possible mitigation would be to have the c_rehash script require explicit confirmation by the user before executing any commands. Another mitigation would be to require explicit confirmation before allowing untrusted data to be passed to a command. Last but not least, the c_rehash script could be rewritten so that the file names of the certificates being hashed are not passed to the hasher by default.
Conclusion:
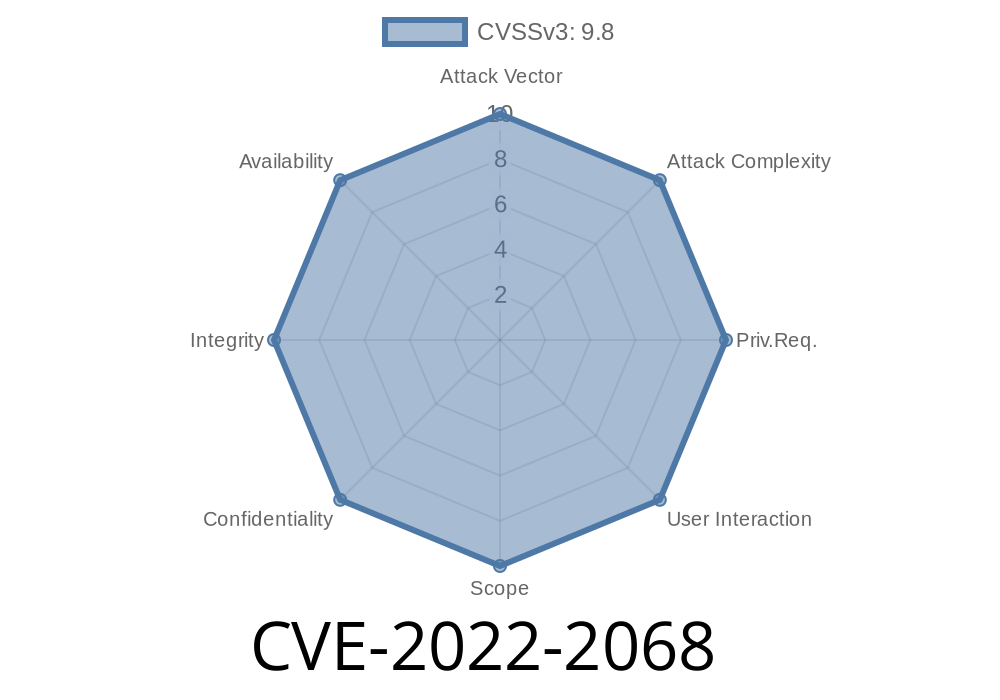
This blog post discusses the importance of the OpenSSL vulnerability, CVE-2022-2068. This vulnerability allows attackers to use a crafted certificate to impersonate servers and disclose data from other servers and applications. Since this vulnerability is not easily remedied, it is important to take steps in order to make sure that the system is secure. The blog post provides multiple recommendations for mitigating this issue.
References
[1] Hacker News
A blog post about the "CVE-2022-2068" vulnerability on the OpenSSL library and potential mitigation steps.
The blog post details a number of ways in which the issue could have been mitigated, including requiring explicit confirmation before executing any commands.
Timeline
Published on: 06/21/2022 15:15:00 UTC
Last modified on: 07/23/2022 04:15:00 UTC
References
- https://git.openssl.org/gitweb/?p=openssl.git;a=commitdiff;h=9639817dac8bbbaa64d09efad7464ccc405527c7
- https://www.openssl.org/news/secadv/20220621.txt
- https://git.openssl.org/gitweb/?p=openssl.git;a=commitdiff;h=7a9c027159fe9e1bbc2cd38a8a2914bff0d5abd9
- https://git.openssl.org/gitweb/?p=openssl.git;a=commitdiff;h=2c9c35870601b4a44d86ddbf512b38df38285cfa
- https://www.debian.org/security/2022/dsa-5169
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/6WZZBKUHQFGSKGNXXKICSRPL7AMVW5M5/
- https://security.netapp.com/advisory/ntap-20220707-0008/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/VCMNWKERPBKOEBNL7CLTTX3ZZCZLH7XA/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-2068