The vulnerability could be exploited remotely via the HTTP protocol. All software releases and imm revisions where the ERS REST API is affected are vulnerable. This component is currently not enabled by default. In certain installations, it may be enabled by setting the variable rest_enabled to ‘True’. This component can be enabled by setting the variable rest_enabled to ‘True’. To determine if you have an affected software release, look at the imm_version value listed in the - imm_version metadata field in the output of the show version command. You can also check to see if the ERS REST API is enabled by looking at the imm_rest_enabled metadata field in the output of the show version command. To determine if your installation is affected, look at the imm_rest_enabled metadata field in the output of the show version command.
Mitigation There are several mitigations you can implement to help protect against this threat. Restrict access to the ERS REST API to only trusted users.
Enable the REST API by setting the rest_enabled variable to ‘True’.
Disable verbose REST API output by setting the rest_verbose_output variable to ‘False’.
Upgrade to the latest software release.
If you are running Cisco ISE and receive an email message that has an attachment named ‘cisco-ise-dmp-report.zip’, it is important to
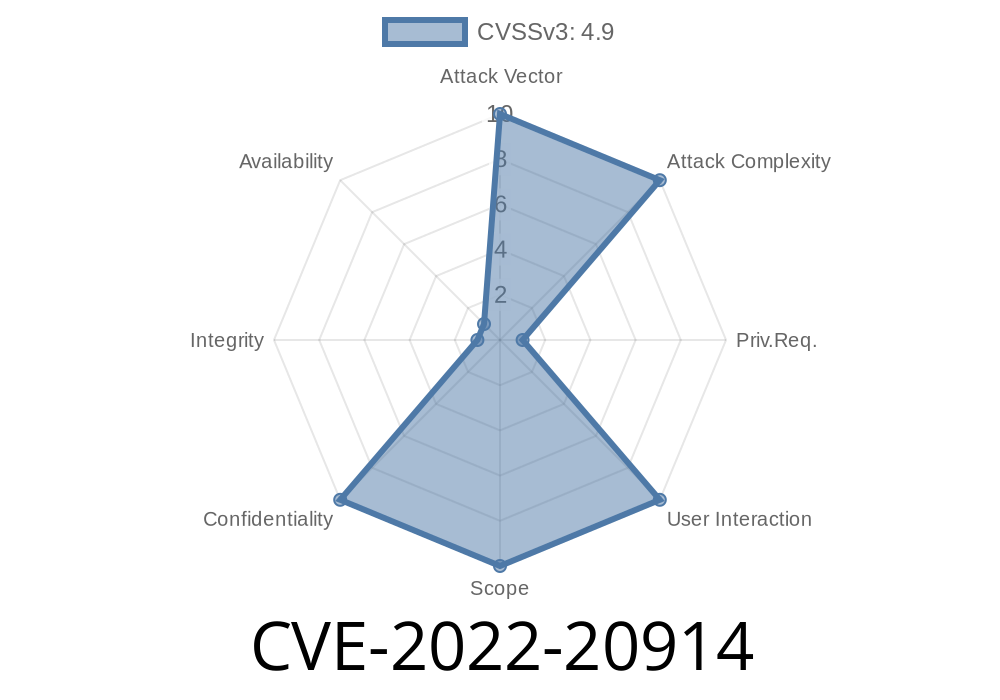
Affected Software: CVE-2022-20914
The vulnerability could be exploited remotely via the HTTP protocol. All software releases and imm revisions where the ERS REST API is affected are vulnerable. This component is currently not enabled by default. In certain installations, it may be enabled by setting the variable rest_enabled to ‘True’. This component can be enabled by setting the variable rest_enabled to ‘True’. To determine if you have an affected software release, look at the imm_version value listed in the - imm_version metadata field in the output of the show version command. You can also check to see if the ERS REST API is enabled by looking at the imm_rest_enabled metadata field in the output of the show version command. To determine if your installation is affected, look at the imm_rest_enabled metadata field in the output of the show version command.
Mitigation There are several mitigations you can implement to help protect against this threat. Restrict access to the ERS REST API to only trusted users.
Enable the REST API by setting rest_enabled variable to 'True'.
Disable verbose REST API output by setting rest_verbose_output variable to 'False'.
Cisco ISE Dump Collector immediately remove the attachment from your system.
ERS REST API Overview
The ERS REST API is a Cisco ISE feature which allows administrators to perform management tasks via the ISE web interface. The API allows access to a subset of the capabilities available through the Cisco ISE GUI and CLI.
Timeline
Published on: 08/10/2022 09:15:00 UTC
Last modified on: 08/12/2022 18:20:00 UTC