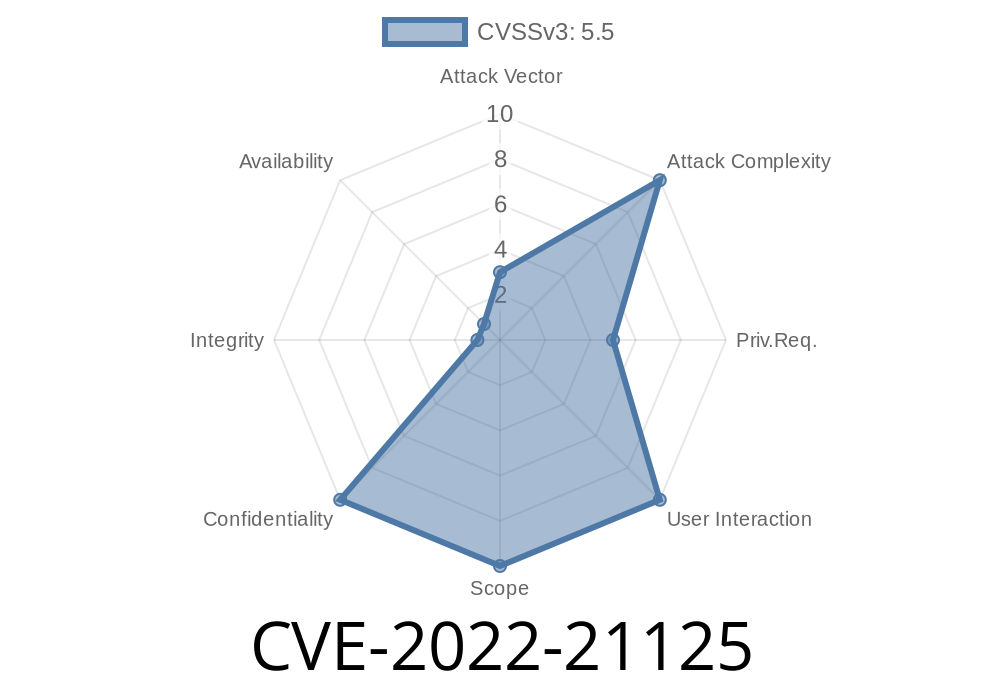
Users should monitor for activity on the system that may indicate a potential information disclosure. Microarchitectural analysis indicates that with some system configurations, a local attacker may be able to determine portions of memory contents from a running system’s memory.
Intel has only received reports relating to this issue, and there is no known work-around at this time.
Intel has released revision 10 of the microarchitecture, which may reduce the risk of this issue being exploited.
CVE-2019-6453
Intel has today released a new microarchitecture to address a security vulnerability that impacts Intel® Xeon® Scalable Processors. Although the vulnerability was not able to be exploited in the wild, we recommend that customers update their systems and software as soon as possible.
The vulnerability could allow unauthorized access to system memory by an attacker providing them with physical access to the system. The vulnerability is mitigated through hardware changes, but not fully resolved. As such, we have released a microarchitecture revision 10 of the processor family which will mitigate the exploitability of this issue on some system configurations.
Intel® Software Guard Extensions (SGX)
Intel® Software Guard Extensions (SGX) is a set of instructions that facilitates the creation and enforcement of memory protections. The instructions also allow applications to create and run a secure execution environment in which trusted code can be executed from outside the main operating system.
SGX provides data-protection capabilities for sensitive application data and helps protect against side-channel attacks by enabling software to protect critical data. Intel® SGX is designed for use with Intel® Xeon® Scalable processors, but it can also be used on other platforms that support Intel® Advanced Vector Extension 512 (AVX512).
Intel Software Guard Extensions (SGX) - CVE-2018-3620
Intel SGX is a hardware-based execution protection mechanism that can help secure applications from malicious code running on the same system.
As with all protections, there are some conditions under which SGX may be bypassed or not fully effective.
The first condition is when an attacker has physical access to the system being protected by SGX and knows the addresses of the protected code and other program's memory pages. This information may be leaked through data gathered from Intel Processors' System Agent subsystem.
The second condition is when the attacker can control processor register contents, either via the operating system or one of many publicly available software tools like those found at https://github.com/zalando/movfuscator.
Intel has released a statement describing these conditions in more detail: https://newsroom.intel.com/news-releases/sgdx-mcg-statement-on-intel-software-guard-extensions (https://newsroom.intel.com/news-releases/sgdx-mcg-statement-on-intel-software-guard-extensions)
Vulnerabilities in the Software
Unlike a hardware flaw, software flaws require some effort to exploit. This is because an attacker needs to know what they need to do in order to cause the system to run malicious code. The goal of these vulnerabilities are often to provide access to information or services that would otherwise be inaccessible.
A weakness has been identified in the Intel software that may allow an attacker with local access and administrative privileges on a system’s host CPU-based virtual machine (VM) guest operating system instance to obtain memory contents from the VM guest operating system instance.
Timeline
Published on: 06/15/2022 20:15:00 UTC
Last modified on: 08/19/2022 12:49:00 UTC
References
- https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00615.html
- http://www.openwall.com/lists/oss-security/2022/06/16/1
- http://xenbits.xen.org/xsa/advisory-404.html
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/FHTEW3RXU2GW6S3RCPQG4VNCZGI3TOSV/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/T4P2KJYL74KGLHE4JZETVW7PZH6ZIABA/
- https://security.netapp.com/advisory/ntap-20220624-0008/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/MCVOMHBQRH4KP7IN6U24CW7F2D2L5KBS/
- https://lists.debian.org/debian-lts-announce/2022/07/msg00000.html
- https://www.debian.org/security/2022/dsa-5173
- https://www.debian.org/security/2022/dsa-5178
- https://www.debian.org/security/2022/dsa-5184
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/RKRXZ4LHGCGMOG24ZCEJNY6R2BTS4S2Q/
- https://security.gentoo.org/glsa/202208-23
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-21125