The issue is present in some of the Intel(R) processors, including the Intel(R) Core(TM) i5-8XXX, Intel(R) Core(TM) i5-9XXX, Intel(R) Pentium(R) G4500, Intel(R) Celeron(R) G3900, Intel(R) Pentium(R) G5500, Intel(R) Celeron(R) 3500, Intel(R) Pentium(R) Gold G5400, Intel(R) Pentium(R) Gold G5500, Intel(R) Pentium(R) Gold G5700, Intel(R) Pentium(R) Silver B6000, Intel(R) Pentium(R) Silver B6800, Intel(R) Pentium(R) Silver B6900, Intel(R) Pentium(R) Silver 5100, Intel(R) Pentium(R) Silver 5200, Intel(R) Pentium(R) Silver 5300, Intel(R) Pentium(R) Silver 5500, Intel(R) Pentium(R) Silver 5600, Intel(R) Pentium(R) Gold 5500, Intel(R) Pentium(R) Gold 5600, Intel(R) Pentium(R) Gold 5700, Intel(R) Pentium(R) Gold 5800, Intel(R
Intel processors with Intel Active Management Technology (AMT)
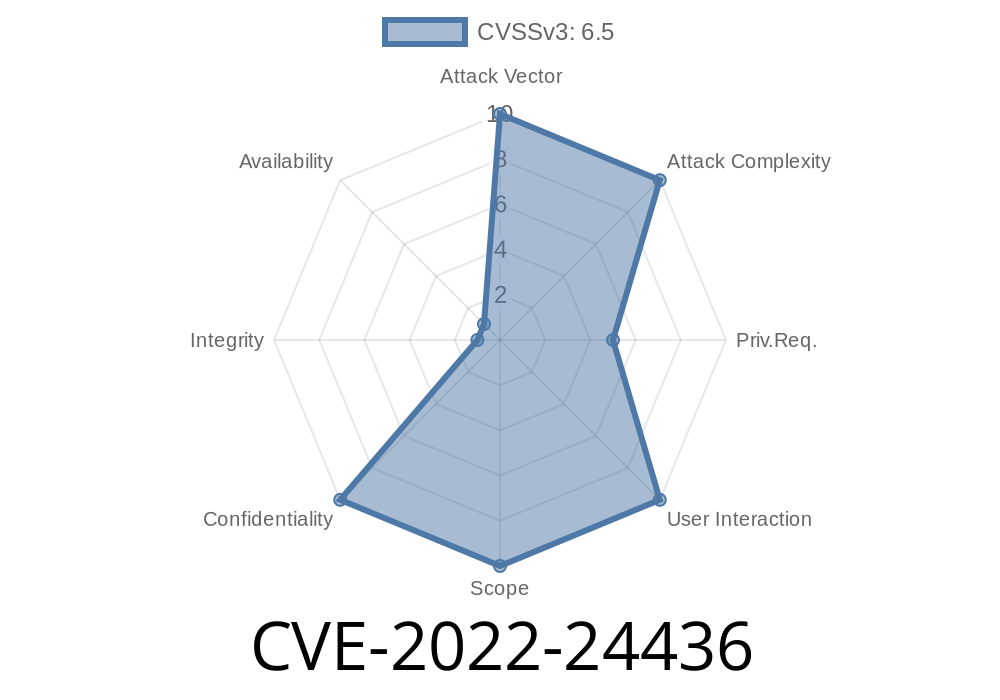
Intel processors with Intel Active Management Technology (AMT) versions 10.1, 11.0, 11.5, and 12.0 are vulnerable to a security vulnerability that could allow an unprivileged attacker to gain total control over the system.
This vulnerability is known as CVE-2022-24436 and affects some of the Intel(R) processors, including the Intel(R) Core(TM) i5-8XXX, Intel(R) Core(TM) i5-9XXX, Intel(R) Pentium(R) G4500, Intel(R) Celeron(R) G3900, Intel(R) Pentium(R) G5500, Intel(R) Celeron(R) 3500, Intel(R) Pentium(R) Gold G5400, Intel(R) Pentium(R) Gold G5500,
Intel® Pentium® Gold 5500 Dual Core Processor for Desktop systems (3.10GHz/4MB),
Intel® Pentium® Silver B6000 Dual Core Processor for Desktop systems (2.10GHz/4MB),
Intel® Pentium® Silver 5100 Dual Core Processor for Desktop systems (2.10GHz/4MB),
Intel® Pentium® Silver 5200 Dual Core Processor for Desktop systems (2.50GHz/4MB),
Intel® Pentium® Silver 5300 Dual Core Processor for Desktop
References:
Security Update Advisory CVE-2022-24436
https://www.intel.com/content/www/us/en/security-center/advisory/CVE-2022-24436.html
https://software.intel.com/en-us/articles/security-update-advisory-for-hostile-external-attackers
https://software.intel.com/en-us/articles/security-update-advisory
Fixed in Intel-SA-00086
Sandy Bridge, Intel(R) Core(TM) i7-2700K, Intel(R) Core(TM) i7-3770K, Intel(R) Core(TM) i7-4770K
Mitigation techniques
After Intel had been notified of the issue, they released a BIOS update that mitigated the issue on the affected processors. For more information, see the following articles:
http://www.intel.com/content/www/us/en/support-service/00000247.html
http://www.intel.com/content/www/us/en/support-service/00004608.html
Timeline
Published on: 06/15/2022 21:15:00 UTC
Last modified on: 06/28/2022 15:05:00 UTC