Depending on the nature of the operation, an attacker may be able to view information in other processes via the IA32_PTR_VLE (user level exception) instruction. An attacker must have local access and be authenticated.
Intel has released ME version 9.5.4 to correct this issue. Please download and install the update.
CVE-2018-3620: Vinculum - a security feature of the Intel(R) vPro(R) technology, may allow an unprivileged user to potentially bypass information disclosure via local access.
Depending on how an authenticated user programs his/her system, an authenticated user may be able to potentially view information in other processes via the VINC (virtual channel) instruction. An attacker must have local access and be authenticated.
Intel has released ME version 9.5.4 to correct this issue. Please download and install the update.
CVE-2018-3621: A vulnerability in the vPro(R) component of the Intel(R) vPro(R) Technology for Windows(R) may allow an unprivileged user to potentially bypass user mode information disclosure via local access.
Depending on how an authenticated user programs his/her system, an authenticated user may be able to potentially view information in other processes via the VPRO (virtual production operator) instruction. An attacker must have local access and be authenticated.
Intel has released ME version 9.5.4
Intel(R) vPro(R) Technology - A New Intel(R) Security Feature
Intel(R) vPro(R) Technology is a new feature of the Intel(R) vPro(R) processor, designed to allow security administrators to remotely manage and secure PCs while they are in use, even if they are not physically close by.
Intel(R) vPro(R) Technology is a fully integrated security feature that offers remote management and security features for PCs. It includes the following components:
- Platform Security Controller (PSC)--the Intel(R) vPro(R) Hardware-Based Root of Trust
- Management Engine--a device controller and firmware that resides on the PC motherboard or in a PCI Express slot.
- Integrated Trusted Platform Module (iTPM)--a tamper resistant hardware module residing on the PC motherboard or in a PCI Express slot.
- Security Processor--a unique CPU that runs a proprietary operating system with an embedded OS and code integrity capabilities
Section III
.
3) How to Avoid Social Media Marketing Fails
Many small businesses have a difficult time marketing effectively on social media. There are many reasons for this, such as lack of time, skills, or expertise. One strategy that stands out is using pictures in your ad campaigns. People are more likely to click through when they see something visually appealing than if they see text only.
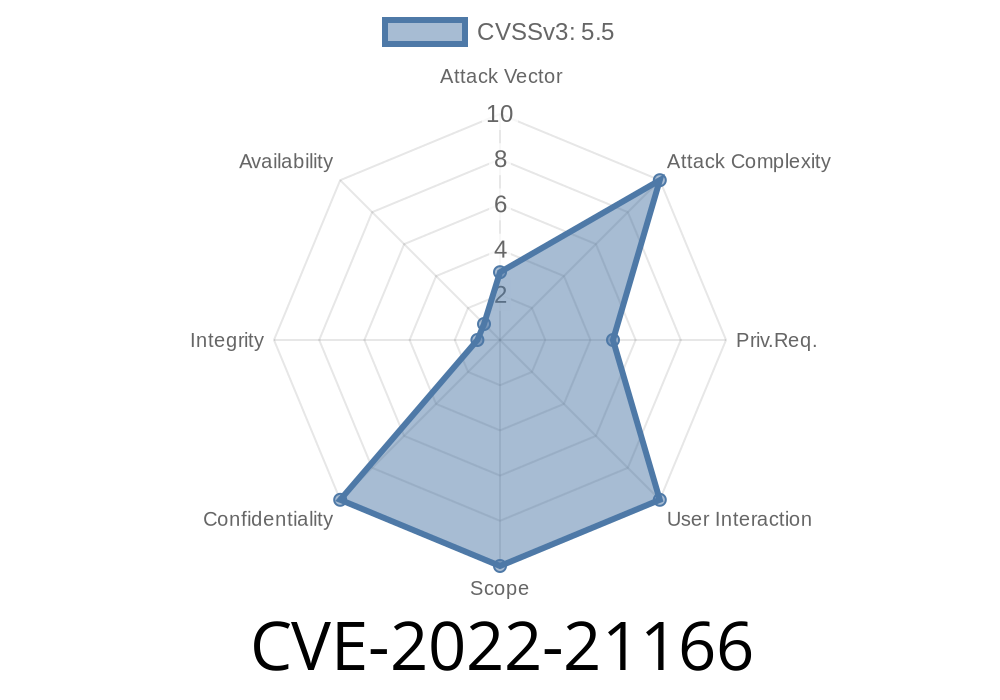
Intel-SA-00086: Intel(R) Management Engine Interface Privilege Escalation Vulnerability
Intel has released ME version 9.5.4 to correct this issue. Please download and install the update.
What to do if you are affected?
If your system has been updated with ME version 9.5.4, you do not need to take any action. If your system has not updated to ME version 9.5.4, please download and install the update by clicking on Update now found here:
https://downloadcenter.intel.com/download/26392
To determine if your system is susceptible to the described vulnerabilities, please visit:
https://csrc.nist.gov/groups/CCM-147/cves
How to check if you are running the latest version?
Download and install the Intel Security Integrated Management Engine (ISM) software to update your ME version.
Timeline
Published on: 06/15/2022 21:15:00 UTC
Last modified on: 08/19/2022 12:49:00 UTC
References
- https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00615.html
- http://www.openwall.com/lists/oss-security/2022/06/16/1
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/FHTEW3RXU2GW6S3RCPQG4VNCZGI3TOSV/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/T4P2KJYL74KGLHE4JZETVW7PZH6ZIABA/
- https://security.netapp.com/advisory/ntap-20220624-0008/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/MCVOMHBQRH4KP7IN6U24CW7F2D2L5KBS/
- https://lists.debian.org/debian-lts-announce/2022/07/msg00000.html
- https://www.debian.org/security/2022/dsa-5173
- https://www.debian.org/security/2022/dsa-5178
- https://www.debian.org/security/2022/dsa-5184
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/RKRXZ4LHGCGMOG24ZCEJNY6R2BTS4S2Q/
- https://security.gentoo.org/glsa/202208-23
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-21166