---
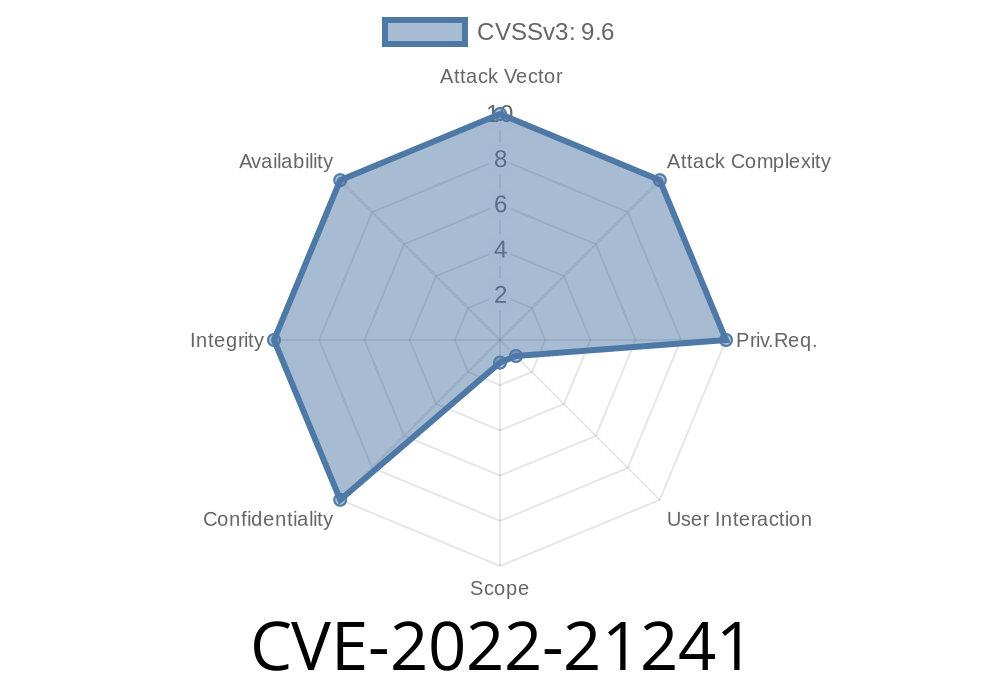
CVE-2022-21241 highlights a critical cross-site scripting (XSS) vulnerability in the popular CSV+ tool (versions before .8.1). In simple words, attackers could upload or share a specially crafted CSV file. Once you open it in a browser with CSV+, it could silently run malicious scripts or even trick your computer into running operating system commands.
Let’s break down how this attack works, how dangerous it is, and how you can protect yourself. We’ll also show you sample code and real-world implications.
What is CSV+ and Why Does This Matter?
CSV+ is a handy open-source app for viewing CSV files in your browser. Many businesses, analysts, and everyday folks use CSV+ to quickly view tabular data without wrangling with big spreadsheet programs.
But, before version .8.1, CSV+ didn’t properly sanitize the contents of a CSV file when displaying data. That means attackers could hide HTML tags or scripts inside a CSV that would run straight in your browser – with no warning.
Imagine you receive a CSV file like this
id,name,website
1,Alice,<a href="javascript:alert('Hacked!')">Click me!</a>
When opened in CSV+, the app would translate the HTML (the <a> tag) into a real clickable link. If you click it — or even in some cases just by viewing — the script alert('Hacked!') executes in your browser context.
Why is This Bad?
- Information Stealing: A malicious script could steal your cookies, session tokens, or browser data.
Phishing: Attackers could display fake forms, tricking you to give out passwords.
- OS Command Execution: In rare cases, attackers could go further, triggering OS-level commands, especially through custom protocols or browser extensions.
Step 1: Craft the Malicious CSV
username,email,profile
bob,bob@example.com,<a href="javascript:alert('Gotcha!')">Open Profile</a>
Step 2: Open This in CSV+ (prior to .8.1)
The "profile" cell renders as a clickable link in the app. Clicking it pops up the alert box — but more dangerous payloads are possible.
Some browsers/extensions allow links like this
id,link
1,<a href="cmd.exe">Run Command</a>
On certain setups (especially Windows + poorly configured browsers), clicking the link could open the Windows command prompt.
> Warning: Do not try opening strange CSV files, especially from unknown sources!
Fixes and Workarounds
- Upgrade to at least CSV+ .8.1. Version .8.1 fixes the vulnerability by sanitizing output and stripping any HTML tags from table cells.
- Validate/Sanitize Input: Always use software that escapes output appropriately.
- Never open CSV files from strangers in browser-based viewers if you don’t know they are fully secure.
References
- Official CVE Report: CVE-2022-21241
- CSV+ Github Repository
- XSS Attacks Explained by OWASP
How CSV+ Fixed It
In version .8.1, the developers added output sanitization. They made sure any HTML entities are rendered as plain text, not as live tags:
function escapeHtml(str) {
return str
.replace(/&/g, "&")
.replace(/</g, "<")
.replace(/>/g, ">")
.replace(/"/g, """)
.replace(/'/g, "'");
}
Now, even if a CSV cell contains <a href="...">, it just appears as text.
Conclusion
CVE-2022-21241 is a classic example of what happens when CSV data isn’t treated with proper suspicion. Keep your tools up to date, and always be wary of files from unknown parties! CSVs aren’t always as innocent as they seem.
Stay safe, and always update your software.
*This article is original content crafted for a simple, clear explanation of CVE-2022-21241 and related XSS CSV vulnerabilities. If you have questions or want more examples, drop a comment or check the resources above!*
Timeline
Published on: 02/08/2022 11:15:00 UTC
Last modified on: 02/14/2022 19:30:00 UTC