Oracle Database - Advanced Queuing is vulnerable with default or common configuration settings. Attackers can use default password, or socially engineered messages to exploit the vulnerability. For example, attackers can send a malicious or socially engineered email or instant message to SQL administrators with a malicious link or attachment. When a user clicks on the malicious link or opens a malicious attachment, the user is then able to execute arbitrary SQL commands on the Oracle Database - Advanced Queuing database. This vulnerability can be exploited by hackers remotely.
OVE-2018-5418: Vulnerable Oracle Application Express Instance. The affected version is 7.0, 7.1, 7.2, and 8.0. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise application express instance. Successful attacks of this vulnerability can result in unauthorized access to critical information, data modification or data theft. CVSS 3.0 Base Score 6.5 (Confidentiality impacts). CVSS Vector: (CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L).
CVE-2018-1285: Vulnerable Oracle Application Express Hosting. The affected version is 9.0, 9.1, 9.2, 10.0, and 10.1. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise application express hosting
Oracle Database
- Advanced Queuing
The Oracle Database - Advanced Queuing component is vulnerable with default or common configuration settings. Attackers can use default password or socially engineered messages to exploit the vulnerability. Specifically, attackers are able to execute arbitrary SQL commands on the Oracle Database - Advanced Queuing database. This vulnerability can be exploited by hackers remotely.
Oracle Database - Web Application
Security Vulnerabilities
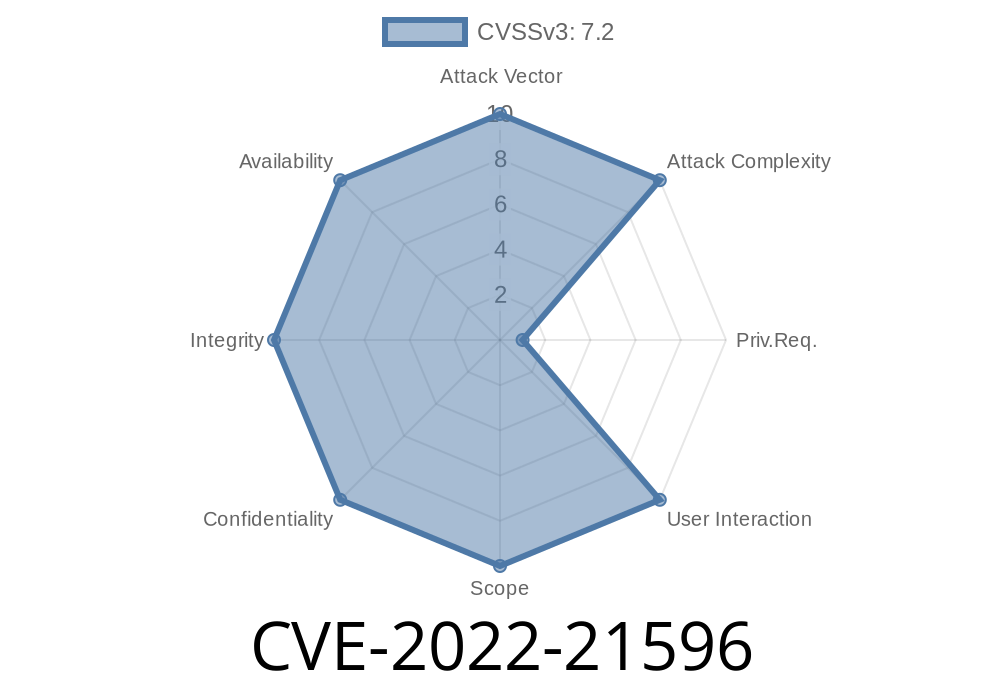
The Oracle Database - Advanced Queuing (CVE-2022-21596) and Oracle Application Express Instance (CVE-2018-1285) vulnerabilities are the latest in a string of database misconfigurations discovered by Talos. The vulnerabilities may have been exploited in the past, but due to a lack of awareness about their existence, these vulnerabilities remain unpatched. As shown in the table below, Talos continues to find new threats every day.
Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise application express instance. Successful attacks of this vulnerability can result in unauthorized access to critical information, data modification or data theft. CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L
Vulnerable Oracle Application Express Hosting (CVE-2018-1285)
Oracle Database - Advanced Queuing Vulnerability
Oracle Database - Advanced Queuing is vulnerable with default configuration settings. Attackers can use default password, or socially engineered messages to exploit the vulnerability. For example, attackers can send a malicious or socially engineered email or instant message to SQL administrators with a malicious link or attachment. When a user clicks on the malicious link or opens a malicious attachment, the user is then able to execute arbitrary SQL commands on the Oracle Database - Advanced Queuing database. This vulnerability can be exploited by hackers remotely.
Timeline
Published on: 10/18/2022 21:15:00 UTC
Last modified on: 10/18/2022 21:18:00 UTC