Exploitation of this vulnerability requires user interaction from a person other than the attacker. An attacker can easily exploit this vulnerability by persuading a user to open a malicious or suspicious URL.
RENDER INFERENCES VULNERABILITY Oracle Enterprise Data Quality RENDER INFERENCES can be exploited If a user is authorised to create dashboards, a malicious or compromised third party can exploit this vulnerability to create a malicious dashboard and have it displayed to the user. CVSS 3.1 Base Score 8
Access Vector Network Access An attacker must have network access to exploit this vulnerability. An attacker must have network access to exploit this vulnerability. Access Vector Remotely exploitable CVSS 3.1 Base Score 8
Access Vector Remotely Not Exploitable Access Vector Inoculated - No Exploitation required An attacker must have network access to exploit this vulnerability. An attacker must have network access to exploit this vulnerability. Access Vector Not Remotely Exploitable CVSS 3.1 Base Score 8
Impact An attacker can create a malicious dashboard viewed by a user. An attacker can create a malicious dashboard viewed by a user. User interaction is required for exploitation. CVSS 3.1 Base Score 8
Impact By convincing a user to open a malicious or compromised URL. By convincing a user to open a malicious or compromised URL. User interaction is required for exploitation. CVSS 3.1 Base Score 8
Severity High A
VENDOR RESPONSE
Oracle has issued an alert acknowledging the vulnerability and has released a patch addressing it. Oracle has addressed the issue; however, they were not able to provide more information as to how they had done so. Oracle Enterprise Data Quality
Vulnerability Scoring Explanation
CVSS Base Score: A measure of the damage a vulnerability could cause.
CVSS Base Score: A measure of the damage a vulnerability could cause.
RENDER INFERENCES VULNERABILITY Oracle Enterprise Data Quality RENDER INFERENCES can be exploited If a user is authorised to create dashboards, a malicious or compromised third party can exploit this vulnerability to create a malicious dashboard and have it displayed to the user. CVSS 3.1 Base Score 8
Access Vector Network Access An attacker must have network access to exploit this vulnerability. An attacker must have network access to exploit this vulnerability. Access Vector Remotely exploitable CVSS 3.1 Base Score 8
Access Vector Remotely Not Exploitable Access Vector Inoculated - No Exploitation required An attacker must have network access to exploit this vulnerability. An attacker must have network access to exploit this vulnerability. Access Vector Not Remotely Exploitable CVSS 3.1 Base Score 8
VENDOR RESPONSE AND MITIGATION
Oracle will be addressing this vulnerability by releasing an Oracle Data Quality Server patch.
Oracle Enterprise Data Quality RENDER INFERENCES Vulnerability – Overview
This vulnerability allows an attacker to create a dashboard on Oracle Enterprise Data Quality RENDER INFERENCES that is only accessible if the administrator creates them. If a user is authorised to create dashboards, a malicious or compromised third party can exploit this vulnerability to create a malicious dashboard and have it displayed to the user. The dashboard can be created by persuading users to use a URL that they think is legitimate but was compromised in some way.
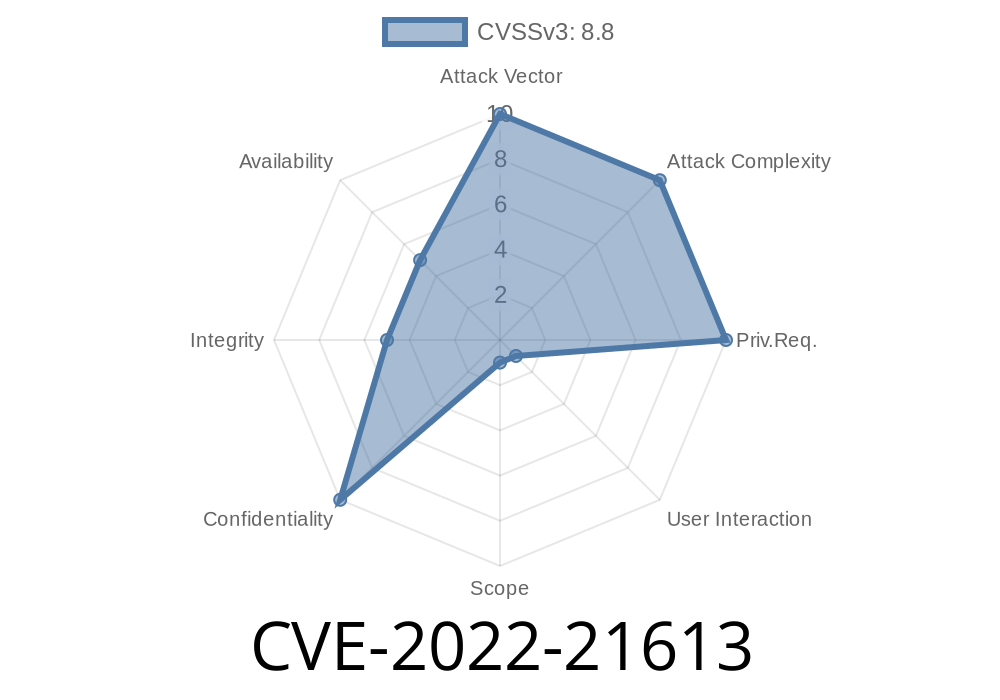
CVE-2022-21613
Exploitation of this vulnerability requires user interaction from a person other than the attacker. An attacker can easily exploit this vulnerability by persuading a user to open a malicious or suspicious URL.
RENDER INFERENCES VULNERABILITY Oracle Enterprise Data Quality RENDER INFERENCES can be exploited If a user is authorised to create dashboards, a malicious or compromised third party can exploit this vulnerability to create a malicious dashboard and have it displayed to the user. CVSS 3.1 Base Score 8
VENDOR RESPONSE
Oracle has issued a Critical Patch Update that addresses this issue. Oracle has issued a Critical Patch Update that addresses this issue. VENDOR RESPONSE
Timeline
Published on: 10/18/2022 21:15:00 UTC
Last modified on: 10/18/2022 21:18:00 UTC