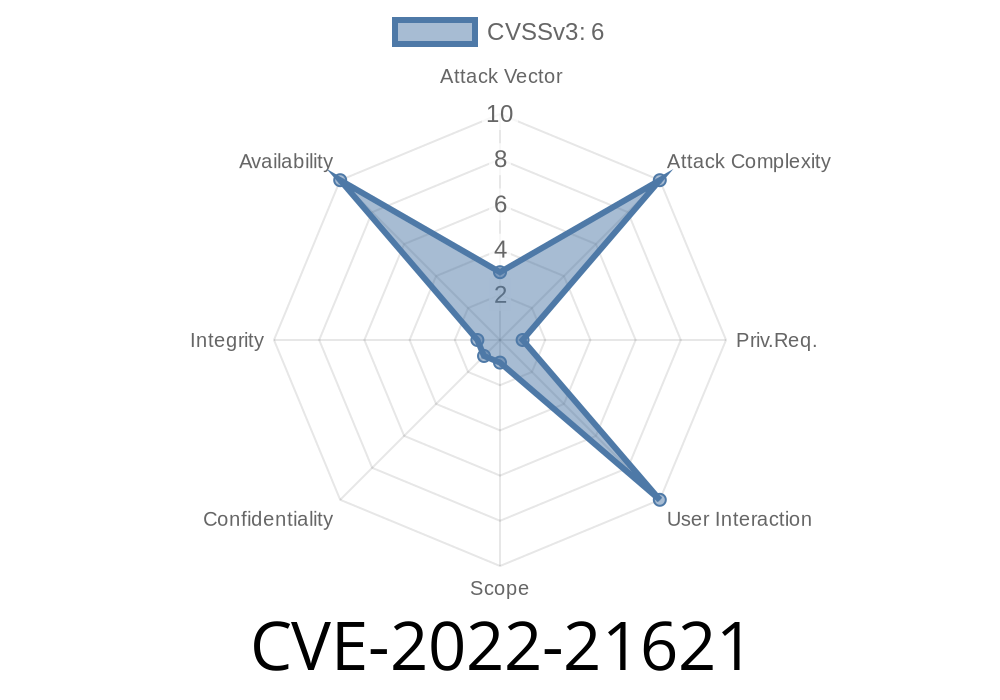
Oracle Virtualization (OVM) VirtualBox is prone to a high severity remote code execution vulnerability due to improper handling of input parameters in certain functions. An attacker can leverage this vulnerability to execute malicious code in the context of the affected virtual machine. This issue affects Oracle VM VirtualBox versions prior to 6.1.40. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP or network access via SSH to compromise Oracle VM VirtualBox. While the web server or SSH server is compromised, an attacker may be able to install a malicious code or conduct other attacks. Additionally, user may be infected by malware if Apache or Nginx is used for web services or SSH access. The update is now available for 6.1.20 and 6.0.24.
Vulnerable Package: Oracle VirtualBox 6.1.40
The following package is affected: Oracle VM VirtualBox 6.1.40
The update packages are available from the following location: https://www.virtualbox.org/wiki/Downloads
Vulnerability details
A vulnerability in Oracle VirtualBox allows an attacker to take over the virtual machine. This can lead to various types of attacks, including installing a malicious code or conducting other attacks.
This vulnerability affects Oracle VM VirtualBox versions prior to 6.1.40 and is easily exploitable. The attacker must have network access via HTTP or SSH. While the web server or SSH server is compromised, an attacker may be able to install a malicious code or conduct other attacks on the virtual machine's system. Additionally, user may be infected by malware if Apache or Nginx is used for web services or SSH access.
Vulnerability overview
VirtualBox is a general-purpose virtualization application that allows users to run multiple operating systems simultaneously on the same computer. VirtualBox is designed to be portable and executable using many guest operating systems. It also provides other features, such as advanced networking, storage, and multimedia support.
Vulnerability Scenario
Oracle VM VirtualBox is a widely used virtualization software that allows multiple operating systems to run on one computer. This software can be used for a variety of purposes, but it is mostly used for development and testing of software in an isolated environment.
The Oracle VM VirtualBox is prone to a high severity remote code execution vulnerability due to improper handling of input parameters in certain functions. An attacker can leverage this vulnerability to execute malicious code in the context of the affected virtual machine. This issue affects Oracle VM VirtualBox versions prior to 6.1.40. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP or network access via SSH to compromise Oracle VM VirtualBox. While the web server or SSH server is compromised, an attacker may be able to install a malicious code or conduct other attacks. Additionally, user may be infected by malware if Apache or Nginx is used for web services or SSH access
Timeline
Published on: 10/18/2022 21:15:00 UTC
Last modified on: 10/18/2022 21:18:00 UTC