by using the Java Naming and Directory Interface (JNDI) to add or remove entries. When running untrusted Java Web Start or Java applet code, this vulnerability can be exploited through sandboxed Java Web Start applications and sandboxed Java applets. It can also be exploited by loading malicious code via a web request. Unauthenticated attacker can exploit this vulnerability to add or remove entries to the LDAP directory. Depending on the LDAP configuration and the nature of the entries being added or removed, this can have a severe impact on the functionality of the affected application. Unauthenticated attacker can also exploit this vulnerability to update LDAP content by using the JNDI functionality. The update or removal of one or more entries can lead to unauthorized update or removal of data from the LDAP directory. In certain cases, the update or removal of one or more entries might result in unauthorized update or removal of data from the LDAP directory in other applications or on the same host. How to repair the Oracle Java SE, Oracle GraalVM Enterprise Edition Software: Update to latest version. For further information, refer to
References !---
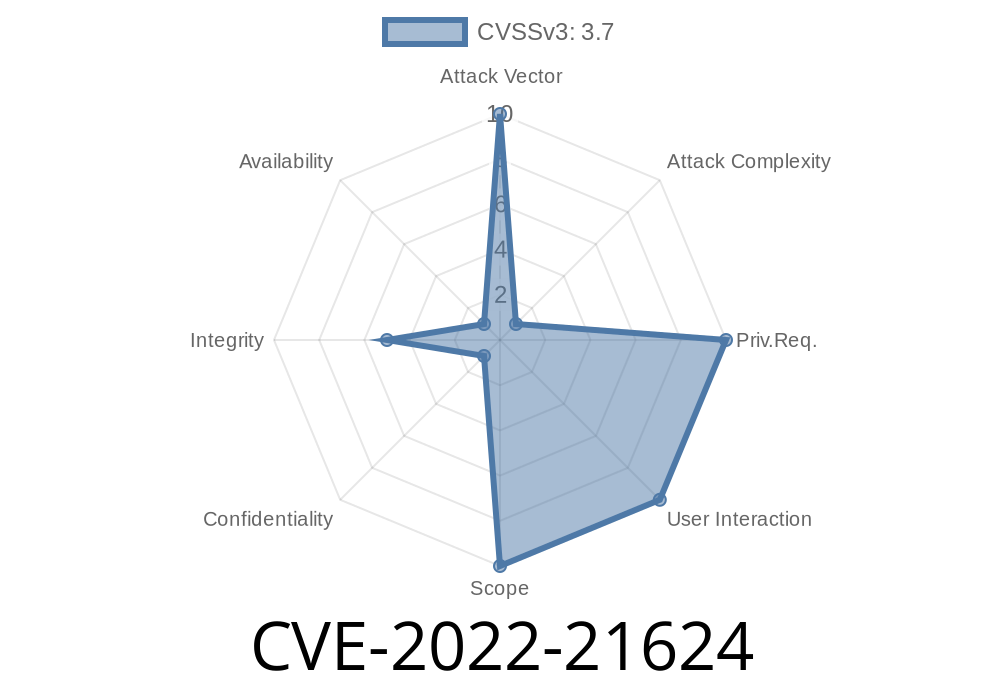
- Java SE, Oracle GraalVM Enterprise Edition Software: Update to latest version (CVE-2022-21624)
!---
The importance of digital marketing is that it provides an effective and cost efficient way for businesses to reach their target audience. By investing in digital marketing, you will help your business grow. There are many different ways to do this with Facebook advertising being one of the most popular. With Facebook, you can target your audience and use information about them to shape your campaigns so they work better.
References ! [CVE-2022-21624](https://cdn.kalibari.io/images/cve-2022-21624.png)

Vulnerability Scenario
The following scenario is one in which this vulnerability can be exploited affecting Oracle Java SE, Oracle GraalVM Enterprise Edition Software.
1. Unauthenticated attacker sends malicious code to victim's web browser to exploit CVE-2022-21624.
2. Victim's web browser runs the malicious code and exploits CVE-2022-21624 successfully on victim's system.
3. To make sure that the malicious code has been executed successfully, untrusted Java Web Start or Java applet code is served to victim's system through Java Web Start application or sandboxed Java applet in order to exploit CVE-2022-21624.
4. The malicious code in step 2 executes successfully and causes an impact on the functionality of the affected application by adding or removing entries to the LDAP directory and updating LDAP content by using JNDI functionality.
Timeline
Published on: 10/18/2022 21:15:00 UTC
Last modified on: 10/18/2022 21:18:00 UTC