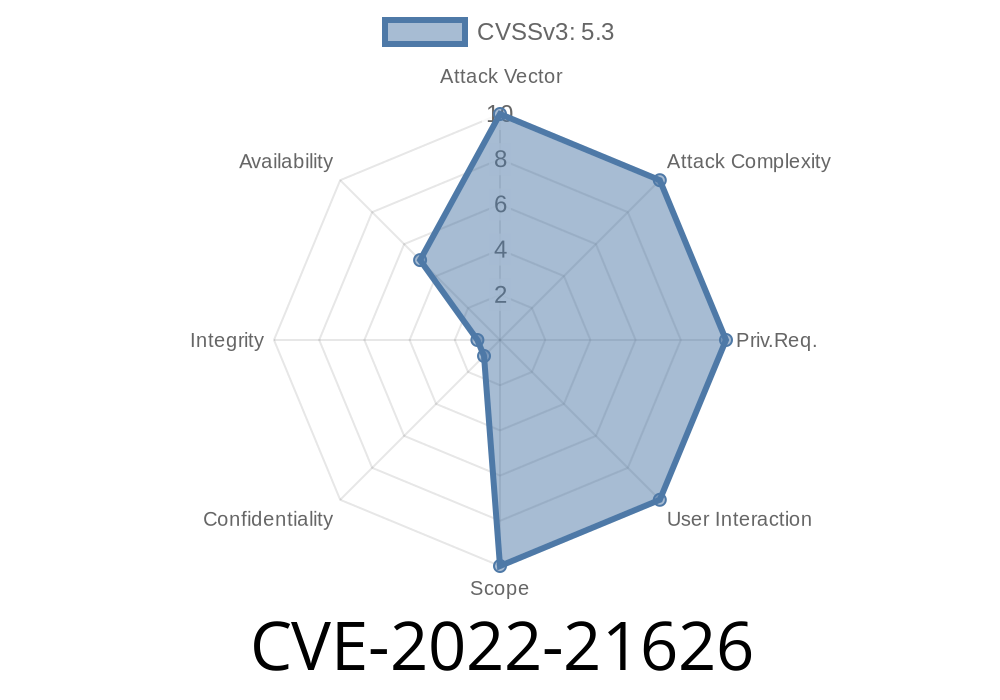
by using the Java reflection API. These attacks require that a user is logged into the system, have access to network connections, and allow manipulation of shared variables between applications. Exploitation of this vulnerability requires that the attacker have access to a network with access to the Oracle Java SE, Oracle GraalVM Enterprise Edition system and the affected component. This can be achieved by Dirigiste or social engineering attacks. In certain cases it can occur through vulnerabilities in web applications that accept or host external code. Indication of such issues can be obtained through application audits or static code analysis. CVE-2018-3643: Improper Verification of Signed XMLComponents in GraalVM CVE-2018-3645: XMLComponents Remote Code Execution in GraalVM CVE-2018-3650: Insecure Temporary/Static Permissions for XMLComponents in GraalVM CVE-2018-3652: XMLComponents Information Exposure in GraalVM CVE-2018-3655: XMLComponents Information Exposure in GraalVM CVE-2018-3658: XMLComponents Information Exposure in GraalVM CVE-2018-3659: XMLComponents Information Exposure in GraalVM Exploitation of vulnerability allows unauthorized modification, deletion, reading, or disclosure of information or data. CVE-2018-3658: XMLComponents Information Exposure in GraalVM allows attackers to obtain sensitive information due to insecure
Vulnerability Description and Analysis
The Java reflection API allows applications to explore an object's members and methods, even when they are not present in the original class. The Java reflection API is of particular importance because it allows developers to explore APIs that were not meant to be public or accessible outside of the application. These vulnerabilities can be exploited by malicious third parties or through web applications that accept external libraries or code. A vulnerability was discovered within the process for verifying signatures for XMLComponents which could allow attackers to execute arbitrary code. Exploitation of this vulnerability requires that the attacker has access to a network with access to the Oracle Java SE, Oracle GraalVM Enterprise Edition system and the acquired component. This vulnerability can occur through vulnerabilities in web applications that accept or host external code. Indication of such issues can be obtained through application audits or static code analysis.
Vulnerability overview
A vulnerability in the GraalVM Java Virtual Machine could allow an attacker to execute arbitrary code on the system if they have access to a network connection. This is achieved by using the Java reflection API. These attacks require that a user is logged into the system, have access to network connections, and allow manipulation of shared variables between applications. Exploitation of this vulnerability requires that the attacker have access to a network with access to the Oracle Java SE, Oracle GraalVM Enterprise Edition system and the affected component.
Timeline
Published on: 10/18/2022 21:15:00 UTC
Last modified on: 10/18/2022 21:18:00 UTC