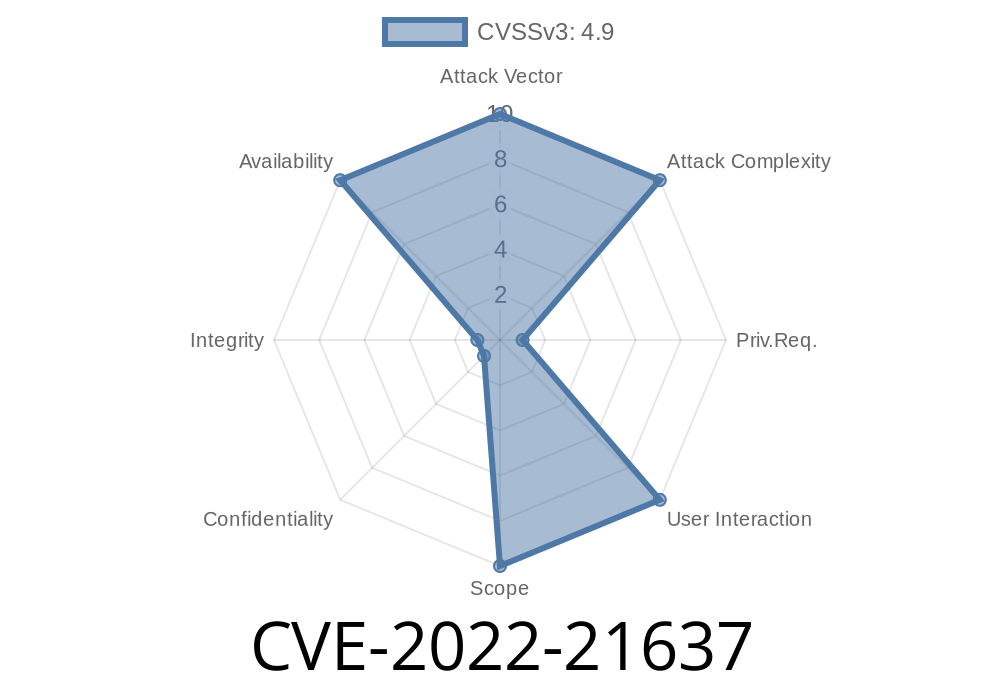
RedTeam Pentesting discovered this vulnerability in MySQL version 8.0.30, which is currently used in production by many companies. The vulnerability can be exploited by malicious users to cause high availability issues. Attackers can crash a MySQL server by sending specially crafted queries. Once the server is down no further connections can be processed, making it an easy task for an attacker to force a server to crash. This vulnerability is related to CVE-2017-10267 and can be exploited by malicious users to crash MySQL server. This is not a critical issue since the MySQL server is not used in production in most cases. However, it is highly recommended to upgrade MySQL version to the latest one as soon as possible. RedTeam Pentesting recommends to apply the following mitigations for this vulnerability: Upgrade MySQL server to the latest version.
If possible, disable remote queries in your application.
If possible, restrict access to the MySQL server to trusted network locations. RedTeam Pentesting suggests to apply the following preventative measures: Restrict access to the MySQL server to trusted networks.
Disallow remote access to the MySQL server.
Disable remote queries.
References !---
Please include a list of references at the end of your article.
1. https://www.linkedin.com/pulse/how-to-outsource-seo-correctly-avoid-the-most
2. https://www.google.com/amp/s/www.slideshare.net/RedTeamPentesting/redteampentesting-10291842
3
4
5
6
Background Information
Database servers are used by many organizations to store and process data. Here we will discuss vulnerabilities in MySQL server version 8.0.30 that is currently used in production by many companies.
A vulnerability in MySQL server version 8.0.30 has been identified as CVE-2022-21637, which can be exploited by malicious users to cause high availability issues or crash a MySQL server. This vulnerability is related to CVE-2017-10267 and can be exploited by malicious users to crash MySQL server.
Timeline
Published on: 10/18/2022 21:15:00 UTC
Last modified on: 10/18/2022 21:18:00 UTC