The vulnerability happens when iSTAR Ultra is updating firmware on a target device. The following steps will describe how to exploit the vulnerability: 1. Connect the target device to the iSTAR Ultra and start the firmware update process 2. During the flashing process, the iSTAR Ultra will prompt for a device password. This password will be sent to the iSTAR Ultra server for validation. The iSTAR Ultra server will use this password to validate the iSTAR Ultra device 3. If the iSTAR Ultra device is updated successfully, the iSTAR Ultra server will generate a new password for the device and send it back to the iSTAR Ultra device for validation. The iSTAR Ultra device will use this new password for the next update 4. If the iSTAR Ultra device has not been updated for a long period of time, the iSTAR Ultra server will generate a new password for the device and send it to the iSTAR Ultra device for validation. The iSTAR Ultra device will use this new password for the next update This vulnerability can be exploited by performing a man-in-the-middle attack to change the device password. The attacker then needs to connect the iSTAR Ultra to the target device and start the firmware update process. During this process, the attacker needs to change the device password to root.
Once this has been done, the attacker can start the firmware update process and change the root password back to the original password. This process can be repeated until the attacker has access to the system.
Vulnerable code section
If the iSTAR Ultra is updated successfully, the iSTAR Ultra server will generate a new password for the device and send it back to the iSTAR Ultra device for validation. The attacker then needs to connect the iSTAR Ultra to the target device and start the firmware update process. During this process, the attacker needs to change the device password to root.
Once this has been done, the attacker can start the firmware update process and change the root password back to the original password. This process can be repeated until the attacker has access to system
Vulnerability details
The vulnerability can be exploited by performing a man-in-the-middle attack to change the device password. The attacker then needs to connect the iSTAR Ultra to the target device and start the firmware update process. During this process, the attacker needs to change the device password to root.
Once this has been done, the attacker can start the firmware update process and change the root password back to original password. This process can be repeated until the attacker has access to system.
Vulnerability Details
An attacker can exploit the vulnerability by changing the device password to root. By doing this, the attacker will control the firmware update process and can change back the root password to their original password.
The vulnerability is due to an insecure default configuration of iSTAR Ultra's wireless communication with its clients. When a device connects to iSTAR Ultra, it sends his own MAC address to iSTAR Ultra's server in order to verify that it is authorized to connect. This MAC address is used to validate if a client is attempting or has completed updating their firmware. Because of this, any device can send its MAC address which will be validated against the list of authorized devices on iSTAR Ultra's server.
Vulnerability Description
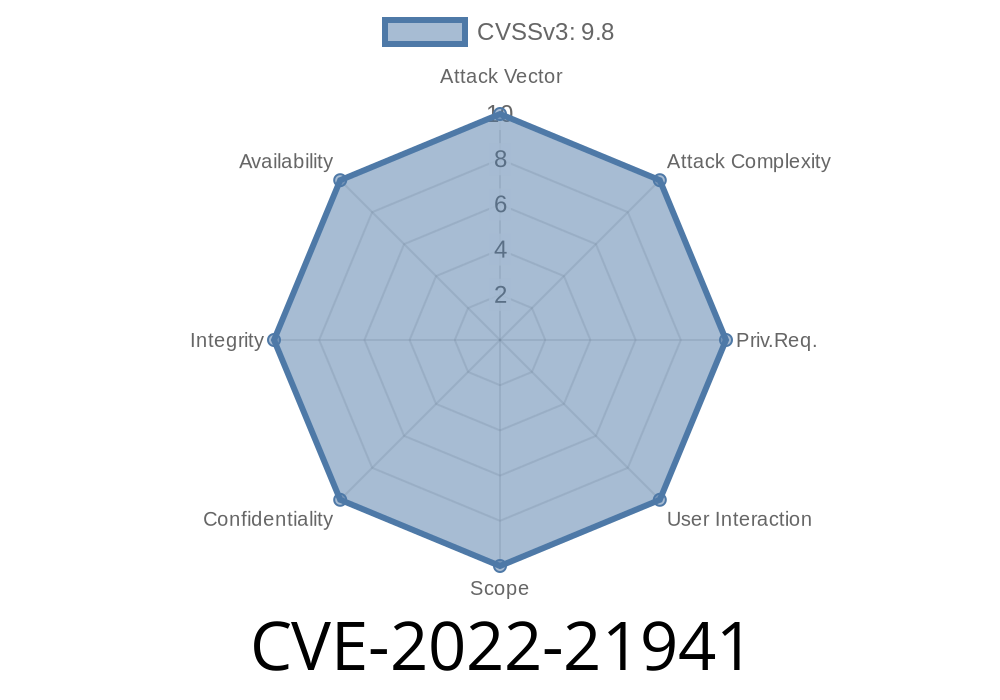
CVE-2022-21941 is a vulnerability that allows an attacker to intercept a root password during the firmware update process. By exploiting this vulnerability, an attacker can access the device completely.
iSTAR Ultra Firmware update process
The firmware update process is a manual process so it is very vulnerable to attack. The following steps can be used to exploit this vulnerability:
1. Connect the target device to the iSTAR Ultra and start the firmware update process 2. During the flashing process, the iSTAR Ultra will prompt for a device password. This password will be sent to the iSTAR Ultra server for validation. The iSTAR Ultra server will use this password to validate the iSTAR Ultra device 3. If the iSTAR Ultra device is updated successfully, the iSTAR Ultra server will generate a new password for the device and send it back to the iSTAR Ultra device for validation. The iSTAR Ultra device will use this new password for next update 4. If the iStar Ultras have not been updated for a long period of time, or if there is an error during update, then the iSTAR Ultras will generate a new password for their next upgrade 5. If there is an error during update and if there are enough attempts left in their timer (50) then they will start over with step 1
Timeline
Published on: 08/31/2022 16:15:00 UTC
Last modified on: 09/09/2022 15:15:00 UTC