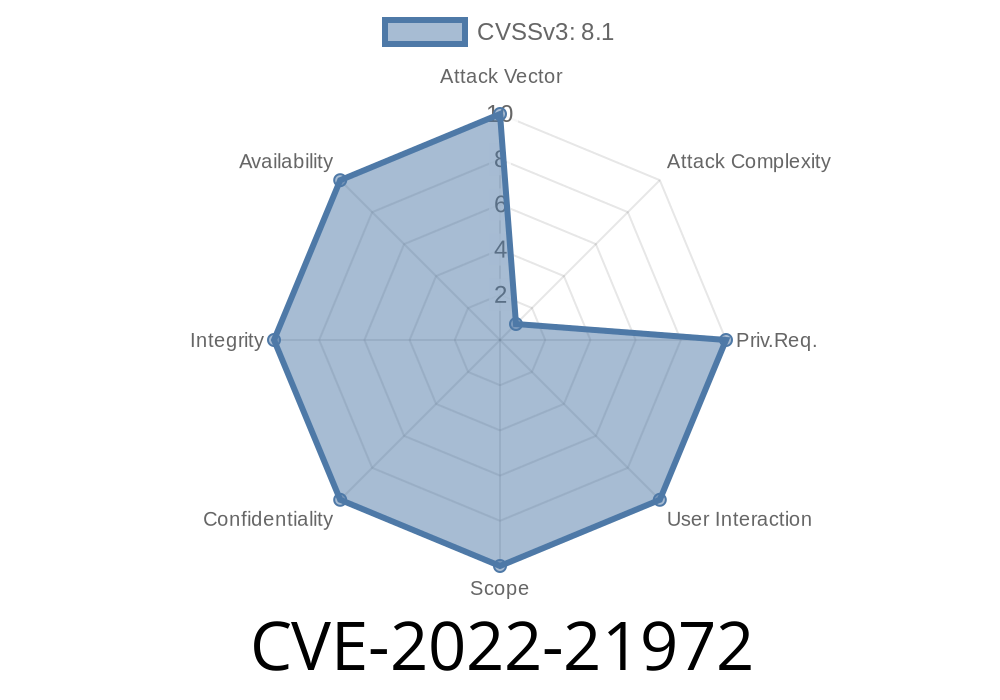
The vulnerability exists due to insufficient validation of user-supplied inputs. Attackers can exploit this vulnerability to execute arbitrary code with elevated privileges on the vulnerable system.
Concern regarding the increasing number of Internet of Things (IoT) devices with default or hard-coded credentials has increased. The report concludes with recommendations on how to mitigate the risk of remote code execution in these devices. Virtualizing or tunneling protocols are often used to secure traffic between two or more hosts. Some of the most commonly used tunneling protocols include OpenVPN, Cisco AnyConnect, and Microsoft Hyper-V. While these protocols are designed to provide end-to end encrypted channel for secure communication, they are also vulnerable to security issues. Security researchers recently discovered a critical remote code execution vulnerability in the Point-to-Point Tunneling Protocol (PPTP). The issue affects Windows, Linux, Mac, Android, iOS, and even Windows RT devices. An attacker can exploit this vulnerability to execute arbitrary code on a targeted system. A remote attacker can exploit this vulnerability to execute arbitrary code with elevated privileges. This can result in full control of the vulnerable system.
What is VPN?
The Point-to-Point Tunneling Protocol (PPTP) is a Microsoft protocol which is used to create virtual private networks. VPNs are designed to provide end-to-end encrypted connections and send data across multiple networks, protecting the privacy of users. The PPTP protocol uses TCP port 1723 for communication. This vulnerability affects Windows, Linux, Mac, Android, iOS, and even Windows RT devices.
Vulnerability Description
A remote code execution vulnerability exists in the Point-to-Point Tunneling Protocol (PPTP) because it does not validate user-supplied inputs.
What is a Virtual Private Network?
Virtual private networks (VPNs) are an attractive tool for securing remote access to data. They are often used to provide secure communications by routing traffic through a virtual tunnel created by the VPN server.
Remote Code Execution (RCE) in Point-to-Point Tunnelling Protocol (PPTP)
Point-to-Point Tunneling Protocol (PPTP) is a popular protocol for securing VPN connectivity. VPNs use PPTP to encrypt traffic between two or more hosts and provide host authentication. While this protocol is designed to provide end-to-end encrypted channel for secure communication, it’s also vulnerable to security issues. Security researchers recently discovered a critical remote code execution vulnerability in the Point-to-Point Tunneling Protocol (PPTP). The issue affects Windows, Linux, Mac, Android, iOS, and even Windows RT devices. An attacker can exploit this vulnerability to execute arbitrary code on a targeted system. A remote attacker can exploit this vulnerability to execute arbitrary code with elevated privileges. This can result in full control of the vulnerable system.
Understanding the Point-to-Point Tunneling Protocol (PPTP) Remote Code Execution Vulnerability
On November 10, 2018, security researchers announced a critical remote code execution vulnerability in the Point-to-Point Tunneling Protocol (PPTP). The issue affects Windows, Linux, Mac, Android, iOS, and even Windows RT devices. An attacker can exploit this vulnerability to execute arbitrary code on a targeted system. A remote attacker can exploit this vulnerability to execute arbitrary code with elevated privileges. This can result in full control of the vulnerable system.
To understand how this vulnerability works and what the consequences are we need to take a closer look at PPTP. Point-to-Point Tunneling Protocol (PPTP) is a protocol that allows users to create virtual private networks across public networks like the Internet. It provides secure and encrypted communication services over an insecure network between two or more hosts and is widely used for remote access solutions like Virtual Private Networking (VPN), Remote Desktop Connection (RDC), and Virtual Private LAN Services (VPLS). PPTP is also commonly used for securing data when wireless communications are not possible or practical due to geographic location constraints.
During one of our recent reviews of VPN solutions we discovered a critical remote code execution vulnerability in PPTP running on Windows systems that allow attackers to execute arbitrary code with elevated privileges on the target computer. This vulnerability exists because there was insufficient validation of user-supplied input before it was passed into the function that actually executes the external call instruction with elevated privileges which results in a stack buffer overflow via memory corruption.
There have
Timeline
Published on: 05/10/2022 21:15:00 UTC
Last modified on: 05/23/2022 17:29:00 UTC