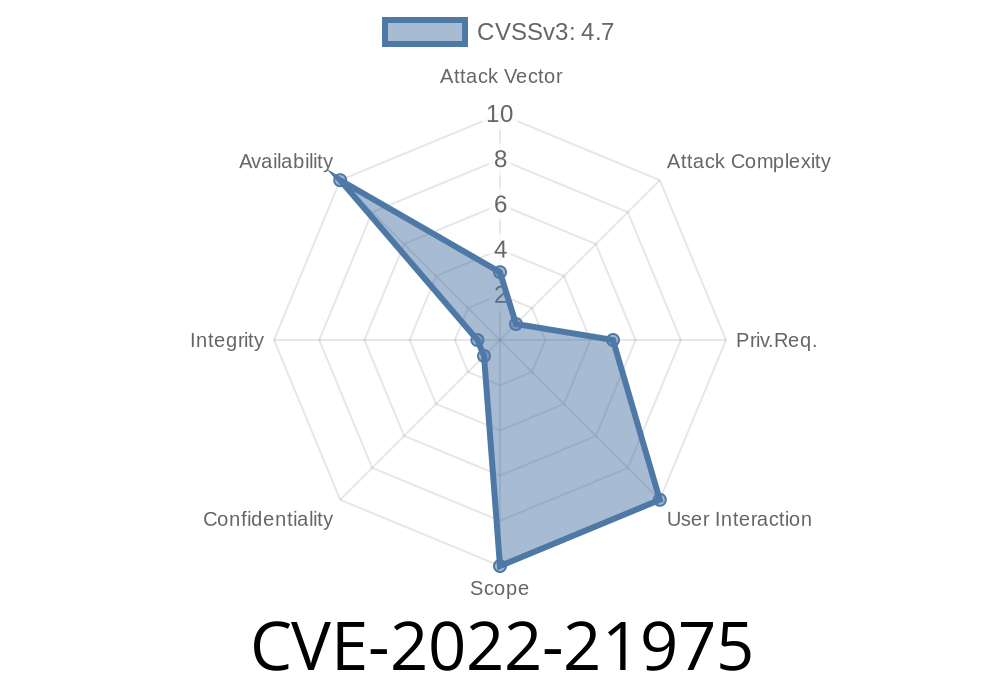
In February 2022, Microsoft patched a critical security bug in Windows Hyper-V, known as CVE-2022-21975. If you use virtualization in Windows environments, or if you’re a security enthusiast wanting to know more about virtualization threats, this vulnerability is essential. This deep-dive will explain the bug, show you how it can be exploited, and offer mitigation tips — all in straightforward, clear language.
1. What is Windows Hyper-V?
Windows Hyper-V is Microsoft’s native hypervisor for running multiple virtual machines (VMs) on a single hardware host. It's widely used in cloud, enterprise, and even home lab environments for development and production workloads.
2. What is CVE-2022-21975?
CVE-2022-21975 is a vulnerability in the Hyper-V virtual switch (vSwitch) component. Specifically, an attacker could cause a Denial of Service (DoS) by sending specially crafted packets to a Hyper-V server network port.
The exploit requires access to a guest VM on a vulnerable Hyper-V host, and can cause the entire host to reboot or crash — affecting all VMs.
Microsoft’s official advisory:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-21975
3. How Does the Exploit Work?
When a VM sends packets through its virtual network adapters, Hyper-V’s vSwitch handles those packets. The vulnerability is triggered by malformed packets sent over a synthetic network adapter.
By rapidly sending malformed or non-standard packets, the attacker can trigger exceptions or undefined behavior within the vSwitch code, causing the Hyper-V host to hang or crash. This action kills all running VMs and can cause prolonged downtime.
Key conditions:
4. Code Example: Fuzzing the Virtual Network
While Microsoft has not released exploit code, security researchers and red teamers sometimes use fuzzers to trigger and find vulnerabilities like this. Here’s a simple Python snippet using sockets to “spray” the virtual network interface from any Linux/Windows guest VM:
import socket
import random
import time
def fuzz_hyperv_vswitch(target_ip, port=5555, duration=10):
end_time = time.time() + duration
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
while time.time() < end_time:
payload = random.randbytes(1024) # Random bytes, 1024 bytes per packet
try:
s.sendto(payload, (target_ip, port))
except Exception as e:
print(f"Send failed: {e}")
s.close()
print("Fuzzing completed.")
# Run inside a guest VM on a vulnerable Hyper-V host, target the gateway bridge:
fuzz_hyperv_vswitch('192.168.1.1', 65535, duration=60)
> Disclaimer: Never use this code on networks you don’t own or have permission to test — it will crash affected Hyper-V hosts!
Fragments, bad sizes, or odd payloads may cause Hyper-V's vSwitch to crash.
*This is not a full weaponized exploit, but illustrates the DoS trigger potential.*
5. Impact and Real-World Scenarios
- Cloud Providers: A malicious customer could crash an entire Hyper-V host, affecting many tenants.
Home Labs: Any user with enough VM rights could crash their own host, causing data loss.
Severity:
Microsoft rates the vulnerability as “Important” (DoS), but in shared environments, it might reach “Critical” due to service disruption.
Microsoft Security Advisory:
Microsoft Patch Notes:
February 2022 Security Updates
- CERT/CC Vulnerability Note:
VU#506878
Hyper-V Internals:
Patch Early:
This bug was fixed in Windows Server security updates released on February 8, 2022. Make sure your Hyper-V servers are current.
- Windows Server 2019: MS KB5010354
- Windows Server 2022: MS KB5010354
Monitor for Crashes:
Monitor logs for unexpected host reboots or crashes that could signal attempts to exploit this or similar bugs.
Final Thoughts
CVE-2022-21975 is a stark reminder that vulnerabilities can exist at the infrastructure level, not just in apps or operating systems. Hyper-V, used in some of the world’s largest data centers, can be brought down with a single VM running a simple script. Always keep your virtualization platforms updated, and consider extra audit and control mechanisms for your guest environments.
Feel free to share or link to this post if you find it helpful. Security is everyone’s business!
*For more details, always refer to the official Microsoft documentation and advisories:*
MSRC CVE-2022-21975
Timeline
Published on: 03/09/2022 17:15:00 UTC
Last modified on: 05/23/2022 17:29:00 UTC