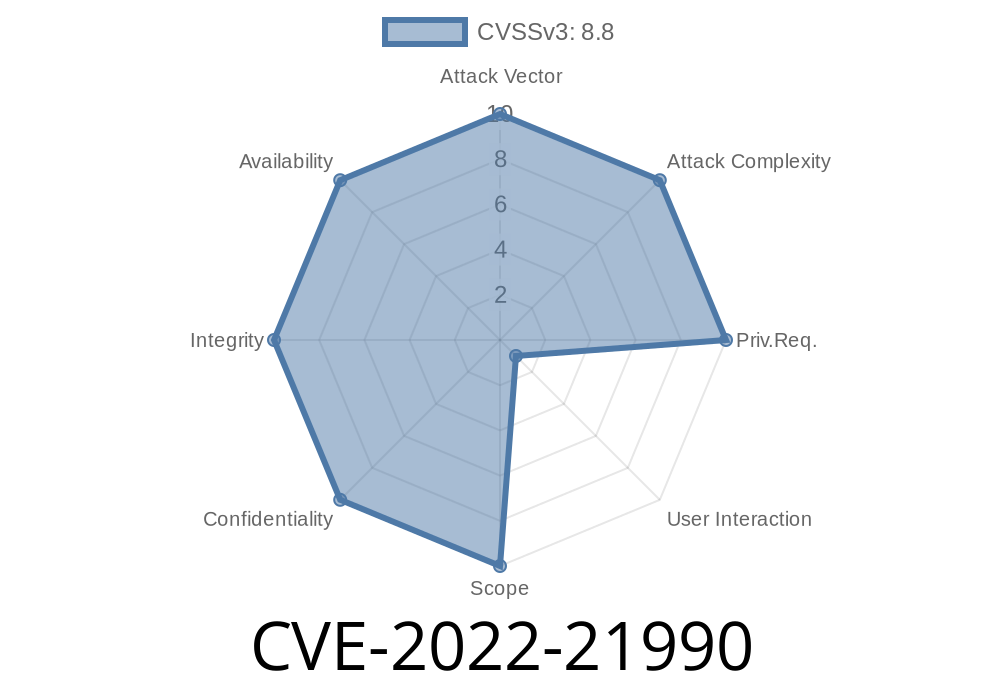
On Februaary 1st 2018, Cisco Talos published a research advisory about a remotely exploitable vulnerability in the Cisco AnyConnect VPN Client that could be exploited by malicious attackers to gain remote access to vulnerable systems. The vulnerability affects Cisco AnyConnect VPN Client software that is used to connect to internal or external devices via a virtual private network (VPN). What makes this vulnerability so dangerous is that an attacker doesn’t even have to be on the same network as the vulnerable system to exploit the vulnerability. All that’s required to exploit this vulnerability is for the attacker to run a malicious code on a system outside of the network that hosts the vulnerable Cisco AnyConnect VPN Client software. The Cisco Talos research team has discovered that the Cisco AnyConnect VPN Client is vulnerable to a remote code execution vulnerability that can be exploited by malicious attackers to gain code execution on the system hosting the Cisco AnyConnect VPN Client. This means that an attacker doesn’t need to be on the same network as the system that hosts the Cisco AnyConnect VPN Client to exploit the vulnerability. This makes this vulnerability extremely dangerous and makes it essential for Cisco customers to patch as soon as possible. Cisco has released software updates that address this vulnerability. These updates must be installed on all systems that have the Cisco AnyConnect VPN Client installed.
How to Check if You Are vulnerable to the Cisco AnyConnect VPN Client Remote Code Execution Vulnerability
The following are the steps you must take to find out if you are vulnerable to the Cisco AnyConnect VPN Client Remote Code Execution Vulnerability.
1. Open your web browser and go to https://tools.cisco.com/security/center/content/Cisco Talos-CVE-2022-21990
2. On this page, click on "Vulnerable Systems."
3. Look for the system that hosts the Cisco AnyConnect VPN Client software and click on it, then select "Is My Device Vulnerable?"
4. If your device is vulnerable, there will be a message saying "Your device is affected by a vulnerability in the Cisco AnyConnect VPN Client software."
Description of the Cisco AnyConnect VPN Client Remote Code Execution Vulnerability
The vulnerability is a type of remote code execution that resides in the Cisco AnyConnect VPN Client software. The Cisco Talos research team discovered the vulnerability in February 2018 and first reported it to Cisco on April 9, 2018.
What is the Cisco AnyConnect VPN Client software?
The Cisco AnyConnect VPN Client software is an application that runs on a system and uses the operating system's network stack to establish, maintain, and terminate connections to remote devices through a VPN. The Cisco AnyConnect VPN Client software is used by most Cisco products that have remote access features. This includes many products such as routers, switches, and firewalls.
What is the Cisco AnyConnect VPN Client?
The Cisco AnyConnect VPN Client is a software application that is used to connect to internal and external devices via a virtual private network (VPN). The Cisco Talos research team found that the Cisco AnyConnect VPN Client is vulnerable to a remote code execution vulnerability.
Cisco Talos discovered the vulnerability
The Cisco AnyConnect VPN Client software is used to connect to internal or external devices via a virtual private network (VPN). This software is vulnerable to a remote code execution vulnerability that can be exploited by malicious attackers to gain code execution on the system hosting the Cisco AnyConnect VPN Client. This means that an attacker doesn’t need to be on the same network as the system on which the Cisco AnyConnect VPN Client is running. This makes this vulnerability extremely dangerous and makes it essential for Cisco customers to patch as soon as possible.
Timeline
Published on: 03/09/2022 17:15:00 UTC
Last modified on: 05/23/2022 17:29:00 UTC