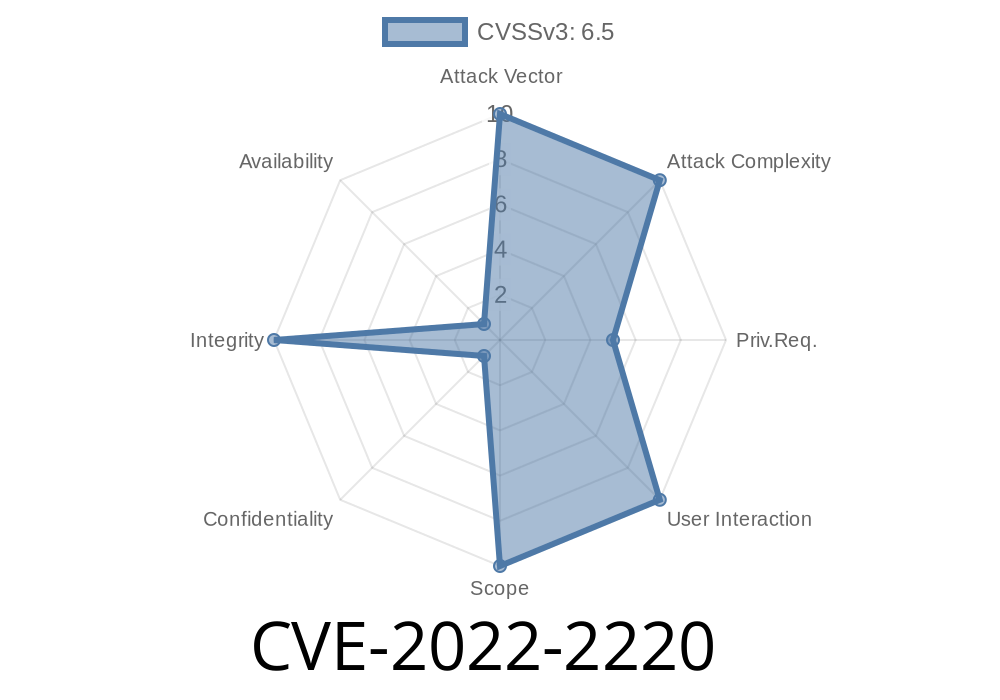
The OpenShift router (or any service that can serve custom routes) cannot be expected to check who owns the subdomain. A subdomain should be owned by a single entity only, as a subdomain is just a part of the domain name. Therefore, a malicious actor may create a subdomain and receive a warning when setting up the custom route.
Critical vulnerability: OpenShift does not verify the email address of the user who sets up a route. This means that an attacker can create a custom route and receive a warning, but the password will still be accepted.
Vulnerability description: OpenShift does not verify the email address of the user who sets up a rou e. This means that an attacker can create a custom route, and receive a warning, but the password will still be accepted.
OpenShift is an application platform that provides the ability to set up routes to access specific endpoints. This allows users to have a single point of access to all resources. OpenShift also has two built-in security mechanisms:
a) The default router does not trust any request sent by root routers and checks for the existence of a CA certificate for every request; b) The default router also verifies that the person requesting the route is who they say they are by checking their email address against their account information in OpenShift Identity and Access Management (OIAM).
Summary of OpenShift Router Vulnerability
A critical vulnerability in the OpenShift router (or any service that can serve custom routes) has been identified. A subdomain should be owned by a single entity only, as a subdomain is just a part of the domain name. Therefore, due to the subdomains being managed by the routing system, malicious actors may create a subdomain and receive a warning when setting up the custom route.
This vulnerability can be misused by attackers to steal data from internal systems or gain more control over an OpenShift environment.
Vulnerability description
An attacker can create a custom route and receive a warning, but the password will still be accepted. This vulnerability can be exploited solely by an attacker who already has access to the OpenShift system.
Timeline
Published on: 08/31/2022 16:15:00 UTC
Last modified on: 09/06/2022 22:10:00 UTC