This issue is related to the fact that application gateways are designed to process HTML content and this functionality also allows to execute arbitrary JavaScript code. In order to exploit this issue an attacker must be able to obtain access to a vulnerable system and perform a series of steps in order to exploit it. This can be easily done by sending a malicious link or email message to an administrator or user with administrative rights. Once an attacker has access to a system they can send a link or email message containing a script that attempts to execute arbitrary code in the context of the vulnerable application gateway server.
Overview of Application Gateways
Application gateways are used in applications to process content coming from outside the application. These gateways often have a web server as a part of their functionality, which is typically running on port 80. An attacker can send a link or email message containing a script that attempts to execute arbitrary code in the context of the vulnerable application gateway server.
Vulnerable System Requirements
The vulnerability is caused by the fact that application gateways are designed to process HTML content and this functionality also allows to execute arbitrary JavaScript code. In order to exploit this issue an attacker must be able to obtain access to a vulnerable system and perform a series of steps in order to exploit it. This can be easily done by sending a malicious link or email message to an administrator or user with administrative rights.
Vulnerability Scenario
The following scenario demonstrates how an attacker would exploit this vulnerability.
1) An attacker finds a vulnerable system on the target network and with administrative rights 2) An attacker sends email message containing a malicious link or .htaccess file to an administrator or user with administrative rights 3) The administrator or user clicks on the malicious link or .htaccess file and executes it in the context of the vulnerable application gateway server
Vulnerable System Overview
This vulnerability affects the following Microsoft products:
• Microsoft Internet Explorer (IE)
• Microsoft Edge
• Windows 10
A vulnerable system is required to be running a web-based application that has been compromised, such as an email client. In order to exploit this vulnerability an attacker must be able to access the web-based application and perform a series of steps in order to exploit it. This can be easily done by sending a malicious link or email message to an administrator or user with administrative rights. Once an attacker has access to a system they can send a link or email message containing a script that attempts to execute arbitrary code in the context of the vulnerable application gateway server.
Vulnerability overview
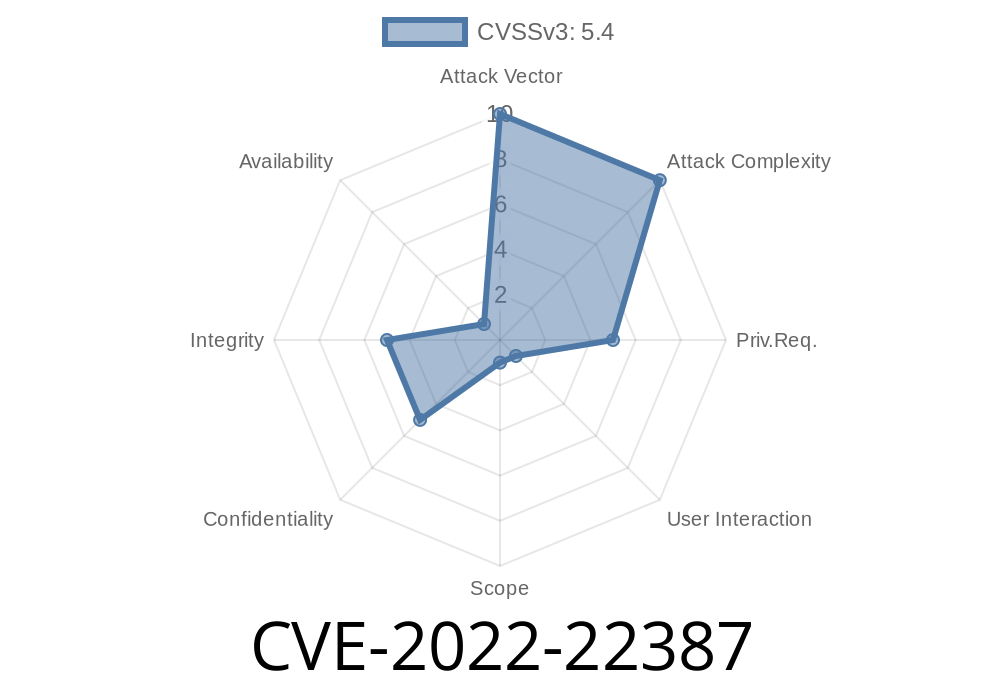
Attackers can exploit CVE-2022-22387 by sending a link or email message to an administrator or user with administrative rights on a vulnerable system. These messages will contain a script that attempts to execute arbitrary code in the context of the application gateway server.
Timeline
Published on: 09/28/2022 16:15:00 UTC
Last modified on: 09/28/2022 19:03:00 UTC