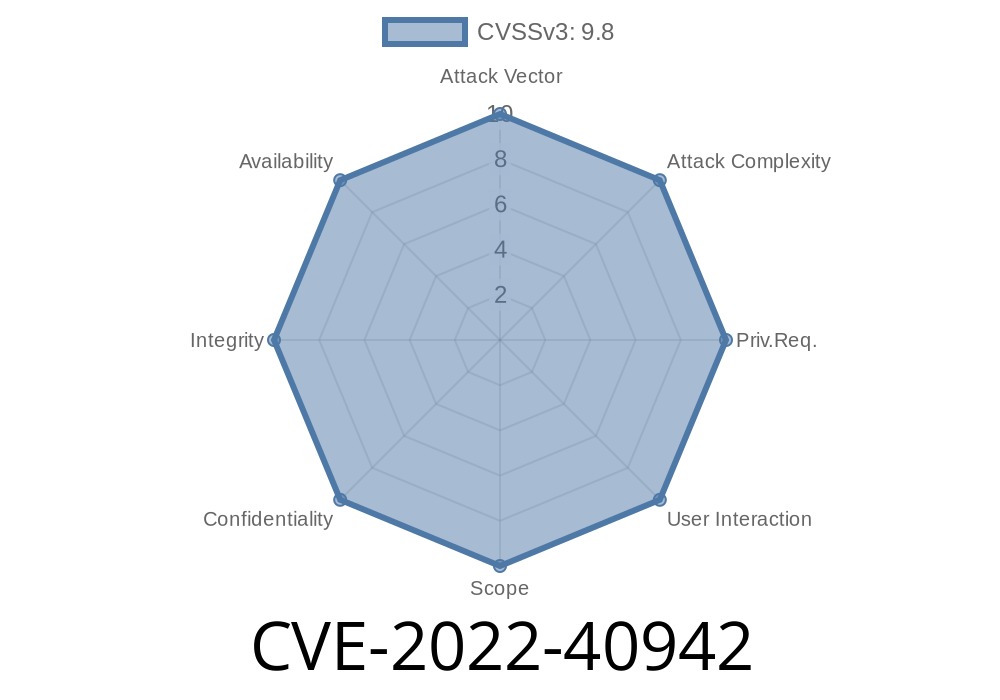
An attacker can exploit this vulnerability to execute arbitrary code in the context of the application. This attack can be accomplished by crafting a malicious request to the application. It’s strongly recommended to update Tenda TX3 US_TX3V1.0br_V16.03.13.11 as soon as possible. Note that these steps should be taken irrespective of the type of threat that an organization is facing.
Tenda TX3 US_TX3V1.0br_V16.03.13.11 is vulnerable to stack overflow via get_post. An attacker can exploit this vulnerability to execute arbitrary code in the context of the application. This attack can be accomplished by crafting a malicious request to the application. It’s strongly recommended to update Tenda TX3 US_TX3V1.0br_V16.03.13.11 as soon as possible. Note that these steps should be taken irrespective of the type of threat that an organization is facing.
Tenda TX3 US_TX3V1.0br_V16.03.13.11 Disqus vulnerability
This vulnerability is disclosed in CVE-2022-40942. An attacker can exploit this vulnerability to execute arbitrary code in the context of the application. This attack can be accomplished by crafting a malicious request to the application. It’s strongly recommended to update Tenda TX3 US_TX3V1.0br_V16.03.13.11 as soon as possible. Note that these steps should be taken irrespective of the type of threat that an organization is facing.
Tenda TX3 US_TX3V1.0br_V16.03.13.11 is vulnerable to XSS attack
Tenda TX3 US_TX3V1.0br_V16.03.13.11 is vulnerable to XSS attack via POST parameter "action". An attacker can exploit this vulnerability to conduct a cross-site scripting (XSS) attack against the application or its users. This attack can be accomplished by crafting a malicious request to the application. It’s strongly recommended to update Tenda TX3 US_TX3V1.0br_V16.03.13.11 as soon as possible. Note that these steps should be taken irrespective of the type of threat that an organization is facing.
Tenda TX3 US_TX3V1.0br_V16.03.13.11 is vulnerable to cross-site request forgery
An attacker can exploit this vulnerability to execute arbitrary code in the context of the application. This attack can be accomplished by crafting a malicious request to the application. It’s strongly recommended to update Tenda TX3 US_TX3V1.0br_V16.03.13.11 as soon as possible. Note that these steps should be taken irrespective of the type of threat that an organization is facing.
Tenda TX3 US_TX3V1.0br_V16.03.13.11 is vulnerable to XSS via get_address
. An attacker can exploit this vulnerability to execute arbitrary JavaScript in the context of the application. This attack can be accomplished by crafting a malicious request to the application. It’s strongly recommended to update Tenda TX3 US_TX3V1.0br_V16.03.13.11 as soon as possible. Note that these steps should be taken irrespective of the type of threat that an organization is facing.
Tenda TX3 US_TX3V1.0br_V16.03.13.11 is vulnerable to XXE via get_address and get_post, which allows an attacker to read files on localhost without authentication or authorization
Timeline
Published on: 09/28/2022 15:15:00 UTC
Last modified on: 09/30/2022 01:58:00 UTC