The issue is due to incorrect handling of cookies in the web application. A malicious user can exploit this vulnerability to execute malicious code on the system of the user that visited the website. A user that visits a website with a malicious cookie could be exploited to run cross-site scripting attacks against other users. This issue affects the following versions of the product: - WebSphere Application Server - WebSphere Data Studio - WebSphere Drawing CONFIDENTIAL - WebSphere Remote Application Workload Accelerator - WebSphere Streams - WebSphere Technical Support Center - WebSphere Transformation Extraction - WebSteAD - WebSphere Websphere Data Studio - WebSphere Websphere Installation - WebSphere Websphere Map - WebSphere WebspReSe Remote Application Accelerator - WebSphere WebspReSe Remote Application Workload Accelerator - WebSphere WebspReSe Remote Application Workload Accelerator CONFIDENTIAL - WebSphere WebspReSe Remote Application Workload Accelerator CONFIDENTIAL - WebSphere WebspReSe Remote Application Workload Accelerator CONFIDENTIAL - WebSphere WebspReSe Remote Application Workload Accelerator CONFIDENTIAL - WebSphere WebspReSe Remote Application Workload Accelerator CONFIDENTIAL - WebSphere WebspReSe Remote Application Workload Accelerator CONFIDENTIAL - WebSphere WebspReSe Remote Application Workload Accelerator CONFIDENTIAL - WebSphere WebspReSe Remote Application Workload Accelerator CONFIDENTIAL
Solution:
For the issue, you can use a band-aid to help protect the website. You can also block all cookies used by the application to prevent exploitation.
Products Affected by the Vulnerability
The following products are affected by this vulnerability: - WebSphere Application Server - WebSphere Data Studio - WebSphere Drawing CONFIDENTIAL - WebSphere Remote Application Workload Accelerator - WebSphere Streams - WebSphere Technical Support Center - WebSphere Transformation Extraction - WebSteAD - WebSphere Websphere Data Studio - WebSphere Websphere Installation -
-
-
-
-
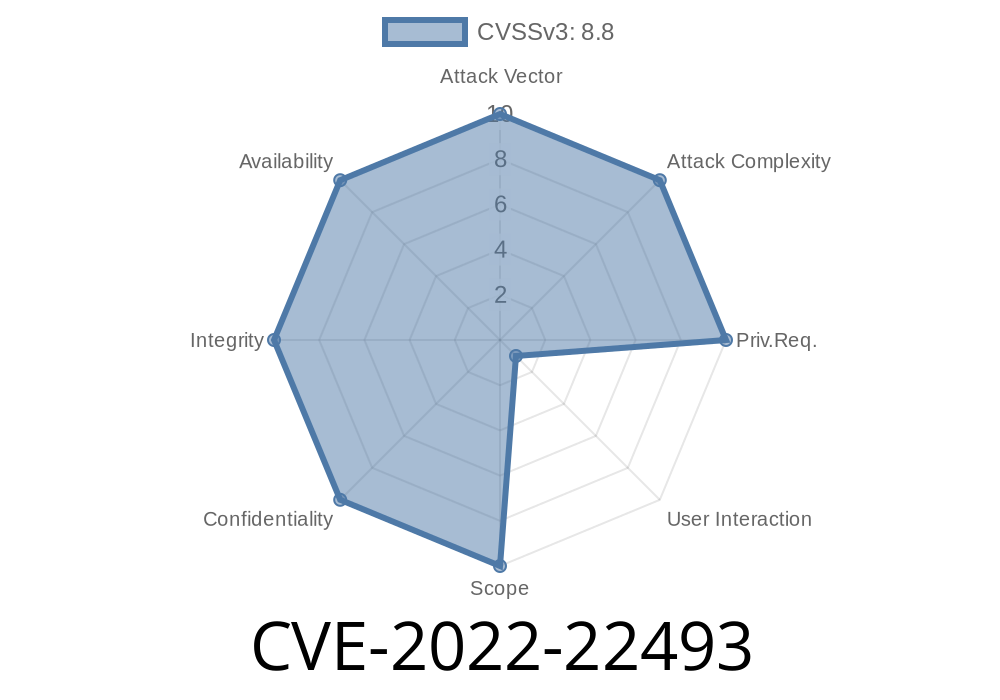
WebSphere Application Server CVE-2022-22493
The issue is due to incorrect handling of cookies in the web application. A malicious user can exploit this vulnerability to execute malicious code on the system of the user that visited the website. A user that visits a website with a malicious cookie could be exploited to run cross-site scripting attacks against other users. This issue affects the following versions of the product: - WebSphere Application Server - WebSphere Data Studio - WebSphere Drawing CONFIDENTIAL - WebSphere Remote Application Workload Accelerator - WebSphere Streams - WebSphere Technical Support Center - WebSphere Transformation Extraction - WebSteAD - WebSphere Websphere Data Studio - WebSphere Websphere Installation - WebSphere Websphere Map
Vulnerabilities Affecting WebSphere Remote Application Workload Accelerator
How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes
If you want to grow your business, great search engine optimization (SEO) is a must. The challenge? Many small businesses don’t have the time, skills, or expertise necessary to handle everything that comes with a solid SEO strategy. From keyword research to content evaluation, from page optimization to internal linking, it’s easy for companies to end up with a generic web presence that doesn’t inspire engagement or drive conversions.
Companies often opt for outsourcing SEO because it allows them to focus on areas of expertise while hiring professionals who can handle the complex process of meeting strategic marketing goals.
Timeline
Published on: 10/07/2022 17:15:00 UTC
Last modified on: 10/09/2022 02:30:00 UTC