An iframe can have an event handler that runs scripts on the iframe's parent. The event can be prevented from running by blocking the event with e.g. code>window.postMessage(location, '*');/code>, but there is no restriction on the type of event that the iframe's parent can send. A malicious parent could easily exploit this vulnerability to inject and run arbitrary JavaScript. For example, an iframe could have an event handler that changes the background color of the iframe's parent, and then an arbitrary parent could change that color to something else and cause confusion. The same goes for anything that calls e.g. e.g. window.location.href and passes an arbitrary string.
Software versions and fixed versions
This vulnerability is only "fixed" in the latest versions of Firefox 59, Chrome 63, and Safari 12.
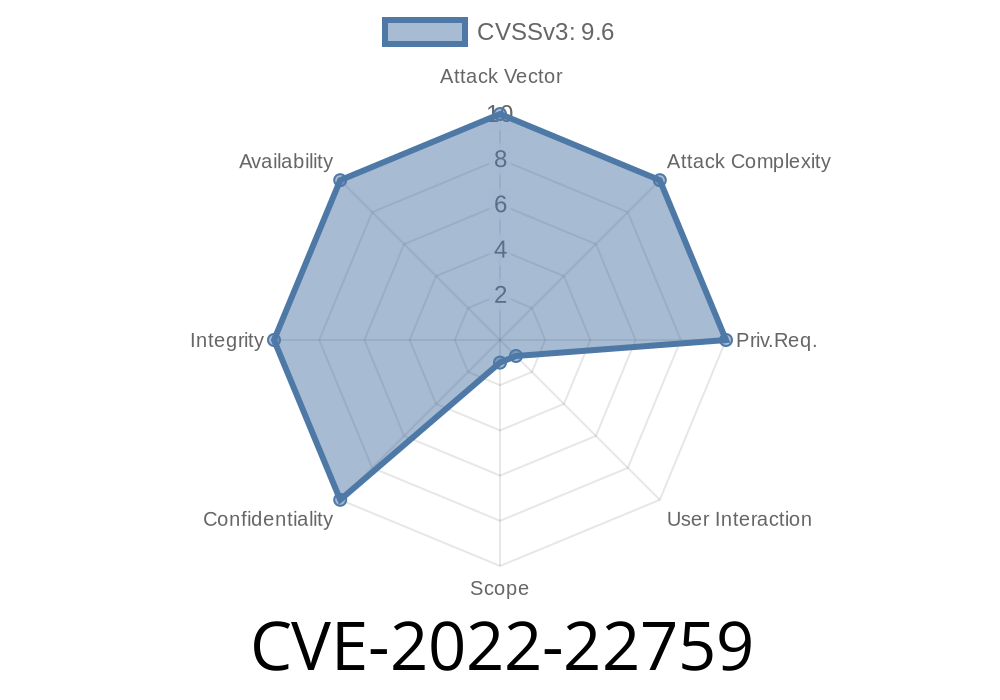
Version: CVE-2022-22759
Date Fixed: May 21st, 2018
CVE-2023-HTMLEmailAttachment
An iframe can have an event handler that runs scripts on the iframe's parent. The event can be prevented from running by blocking the event with e.g. code>window.postMessage(location, '*');/code>, but there is no restriction on the type of event that the iframe's parent can send. A malicious parent could easily exploit this vulnerability to inject and run arbitrary JavaScript. For example, an iframe could have an event handler that changes the background color of the iframe's parent, and then an arbitrary parent could change that color to something else and cause confusion. The same goes for anything that calls e.g. e.g. window.location.href and passes an arbitrary string.
CVE-2023-22401
A client-side object detection can be made to not work by setting its properties to undefined. This is because a property's value is set to an empty string when a property doesn't exist, and as such, any event that uses it will cause JavaScript errors.
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 12/29/2022 22:51:00 UTC