Microsoft Exchange Server is one of the most widely used email solutions. It offers a variety of features like calendar, contacts, tasks, and messaging, which are required by many organizations, small as well as large scale. In addition to it, Exchange also offers a web interface that can be accessed by all users, regardless of their mailbox location.
The web interface can be accessed remotely via a web browser, through a remote computer on the network. This makes the web interface vulnerable to cross-site scripting attacks, which can result in the execution of arbitrary script code on the targeted system. In addition to it, Exchange also provides the capability to connect to it via Outlook.
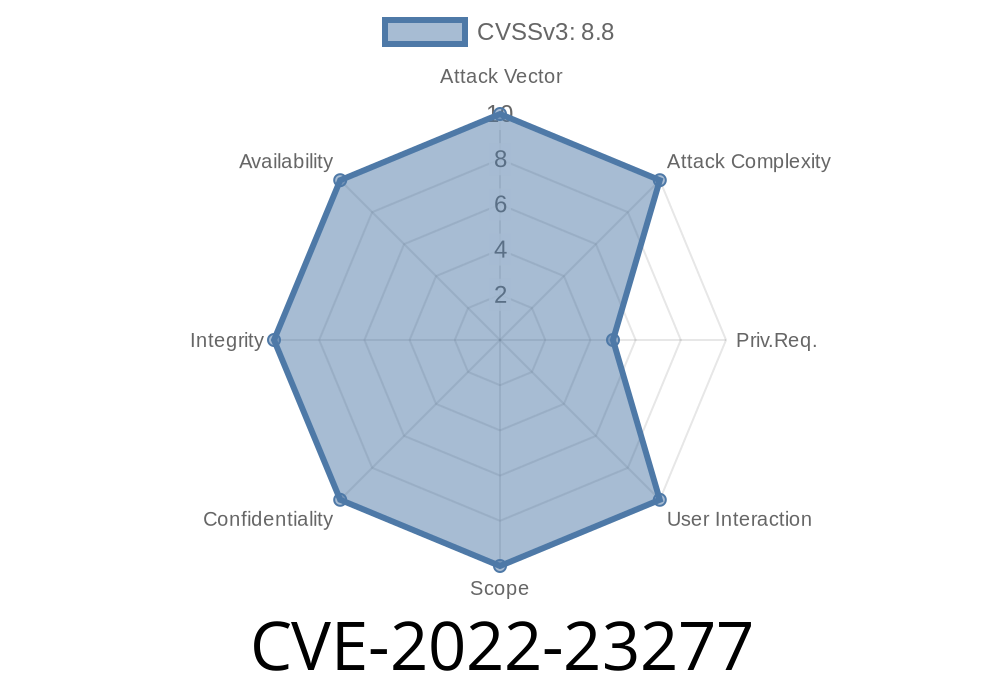
Overview: Exchange Cross Site Scripting vulnerability
The CVE-2022-23277 vulnerability is a cross site scripting vulnerability on Microsoft Exchange Server. It affects the web interface of Exchange and can be exploited to execute arbitrary script code on the targeted system. As mentioned earlier, it also provides the capability to connect to it via Outlook.
Unlike other cross site scripting vulnerabilities that occur when a user visits a malicious URL or file, this vulnerability occurs when a user opens an email with content that contains malicious script code which is generated by an attacker and delivered by Microsoft Exchange Server. The attack can be initiated by sending an email from any sender that's capable of sending mail from their account in Microsoft Exchange Server. An attacker may send such an email in a way that appears as if it's coming from someone else such as a colleague or boss, thereby bypassing security measures put in place on corporate networks. This may happen if users share their mailbox for collaboration purposes or because of password reuse between two different accounts using different credentials.
Exchange Server Cross Site Scripting (XSS) Vulnerability
Cross-site scripting (XSS) vulnerabilities occur when a website displays content generated by another site that is not properly sanitized. This often happens through web pages with embedded content, like iframe tags. After the user submits the form, malicious code can be executed in their browser and this is what makes XSS an example of a DOM-based attack.
Exchange Server doesn’t have any mechanism to prevent or mitigate these types of attacks. A malicious email that contains a script payload can cause Exchange server to execute it and then allow it to take further actions on the system without any further authentication from the user. The following code would cause Exchange to execute:
Exchange Server Vulnerability – Introduction
This vulnerability is due to the web interface designed for Exchange Server, which can be accessed via a remote computer on the network. The vulnerability can result in the execution of arbitrary script code on the targeted system and it's attributed to cross-site scripting attacks.
This vulnerability affects Microsoft Exchange Server versions from 2007 to 2013, which are still widely used.
Affected systems will have an error message displayed on the "Internal Error" page of Exchange Web Services when trying to access, for example, https://mailbox.domain.com/exchange/owa; additionally, there will be no response to a user clicking refresh (F5) on that particular URL.
The following screenshot shows what this might look like:
Technical Overview of Cross-Site Scripting Attacks
Cross-site scripting attacks are a type of security breach that allow attackers to execute malicious code on the targeted system. This is usually done through an injected script that is executed by the browser. If the script is embedded in content displayed on a web page, it will be executed in the context of that content's parent window. In Exchange, cross-site scripting vulnerabilities occur when the web interface is accessed via Outlook and allows for any script to be run in its context. When this happens, any client application can share its data with the server, which includes all emails and calendar items.
Cross-Site Scripting
(XSS) Attacks
Outlook connects to Exchange Server through RPC, a protocol that allows Outlook to access mailbox information and send/receive email. This protocol is vulnerable to an XSS attack, which can result in the execution of arbitrary script code on the targeted system.
To prevent this from happening, take the following precautions:
- Keep all Outlook client software up-to-date
- Make sure that only necessary ports are open on your firewall for RPC connections
- Make sure that the hosts for your Exchange server are located in fully trusted networks
Timeline
Published on: 03/09/2022 17:15:00 UTC
Last modified on: 08/22/2022 18:15:00 UTC