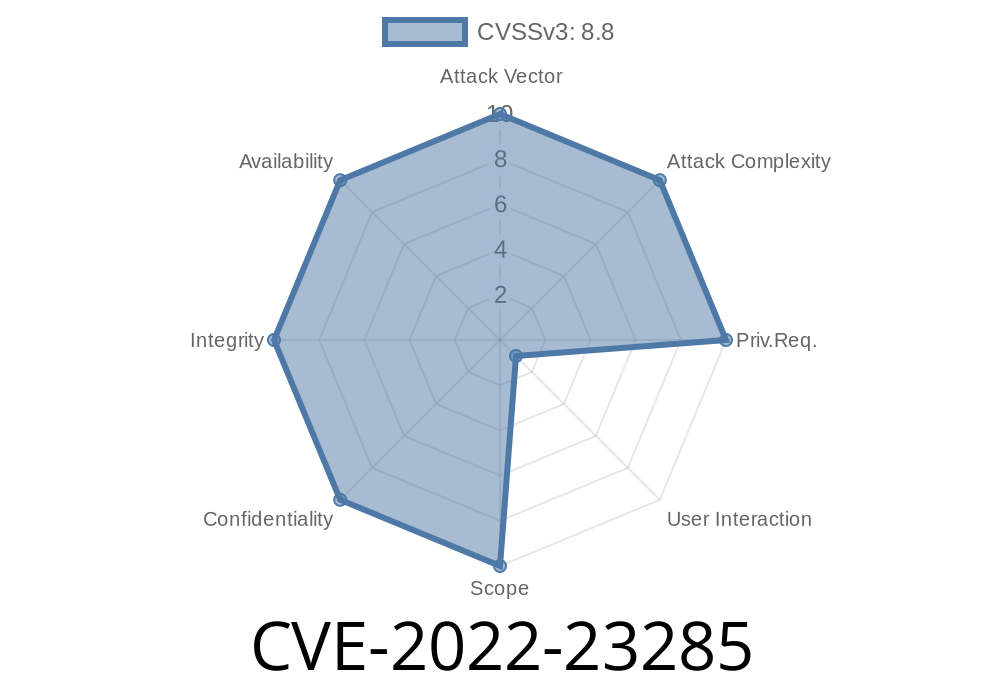
Remote Code Execution is the capability of a program to run on another system, with that system’s owner consent or acquiescence, for the purpose of executing any command, on that system. This can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it. Remote Code Execution can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it. Remote Code Execution can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it. Remote Code Execution can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it. Remote Code Execution can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials
Understanding the value of monitoring
The value of monitoring is having an awareness of the current status and state of the system.
Monitoring systems provide a host of information that can be used to help determine if a remote code has been executed on a system. It can quickly be determined if there are signs of it, or if it has been done.
The value of monitoring is having an awareness of the current status and state of the system. Monitoring systems provide a host of information that can be used to help determine if a remote code has been executed on a system. It can quickly be determined if there are signs of it, or if it has been done. The value of monitoring is having an awareness of the current status and state of the system. Monitoring systems provide a host of information that can be used to help determine if a remote code has been executed on a system. It can quickly be determined if there are signs of it, or if it has been done.
Why is Remote Code Execution a bad thing?
Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it. Remote Code Execution can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it. Remote Code Execution can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it. Remote Code Execution can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials.
How does Remote Code Execution work?
1. Remote Code Execution is the capability of a program to run on another system, with that system’s owner consent or acquiescence, for the purpose of executing any command, on that system.
2. This capabilitiy can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials.
3. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it. Remote Code Execution can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it. Remote Code Execution can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it
How to Detect Signs of Abuse?
If you get a report from your monitoring system that there is something suspicious going on, it may be a good idea to check and see if there are any signs of abuse. For example, the following symptoms may indicate remote code execution:
1) Programs like cmd.exe or taskmgr.exe are running / not running
2) Loops in user input or files - for example, when cmd.exe executes ps.exe and ps does not exit
3) Malicious toolbars in browsers
4) Strange new files uploaded to your website
5) When users report feeling unusual after visiting your site
What is a Remote Code Execution Vulnerability?
Remote Code Execution is the capability of a program to run on another system, with that system’s owner consent or acquiescence, for the purpose of executing any command, on that system. This can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it. Remote Code Execution can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it. Remote Code Execution can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials.
Remote Code Execution is the capability of a program to run on another system, with that system’s owner consent or acquiescence, for the purpose of executing any command, on that system. This can be accomplished by either gaining access to the system, or by gaining access to the user’s credentials. Remote Code Execution is the most serious vulnerability a system can have. It is critical to have a monitoring system in place to detect signs of it.
Timeline
Published on: 03/09/2022 17:15:00 UTC
Last modified on: 03/14/2022 16:55:00 UTC