The issue affects systems that have Active Directory deployed, and if Active Directory is enabled, it is highly recommended that you disable it on your target systems. A remote code execution vulnerability exists in Windows Domain Services, which could allow an attacker to take advantage of this issue to install programs, view or change data, or create new accounts with full user rights. In order to exploit this issue, an attacker must first be able to run a malicious code on the target system. It is possible to do so if a user clicks on a specially crafted website or if a user opens a specially crafted Microsoft Office document.
In Windows domain environments, Active Directory is enabled by default, which makes it a high risk to deploy in such environments. It is recommended that administrators disable Active Directory on domain controllers and disable user login to Active Directory by default. If you are running Windows 10, we recommend that you disable the ability to join a domain. To disable this feature, navigate to Settings > Accounts > Sign-in options > Never allow signing in with this device . - Windows PDEV Elevation of Privilege Vulnerability. A remote code execution vulnerability exists in Windows that could allow an attacker to take advantage of this issue to install programs, view or change data, or create new accounts with full user rights. In order to exploit this issue, an attacker must first be able to run a malicious code on the target system
Windows Privileged Elevation of Privilege (PDEV) vulnerability
A privilege escalation vulnerability exists in Windows that could allow an attacker to take advantage of this issue to install programs, view or change data, or create new accounts with full user rights. In order to exploit this issue, an attacker must first be able to run a malicious code on the target system. It is possible to do so if a user clicks on a specially crafted website or if a user opens a specially crafted Microsoft Office document.
In Windows domain environments, Active Directory is enabled by default, which makes it a high risk to deploy in such environments. It is recommended that administrators disable Active Directory on domain controllers and disable user login to Active Directory by default. If you are running Windows 10, we recommend that you disable the ability to join a domain. To disable this feature, navigate to Settings > Accounts > Sign-in options > Never allow signing in with this device .
Windows PDEV Elevation of Privilege Vulnerability
The issue affects systems that have Active Directory deployed, and if Active Directory is enabled, it is highly recommended that you disable it on your target systems. A remote code execution vulnerability exists in Windows Domain Services, which could allow an attacker to take advantage of this issue to install programs, view or change data, or create new accounts with full user rights. In order to exploit this issue, an attacker must first be able to run a malicious code on the target system. It is possible to do so if a user clicks on a specially crafted website or if a user opens a specially crafted Microsoft Office document.
In Windows domain environments, Active Directory is enabled by default, which makes it a high risk to deploy in such environments. It is recommended that administrators disable Active Directory on domain controllers and disable user login to Active Directory by default. If you are running Windows 10, we recommend that you disable the ability to join a domain. To disable this feature, navigate to Settings > Accounts > Sign-in options > Never allow signing in with this device .
Windows Privileged Device Enumeration Elevation of Privilege (CVE-2022)
A remote code execution vulnerability exists in Windows that could allow an attacker to take advantage of this issue to install programs, view or change data, or create new accounts with full user rights. In order to exploit this issue, an attacker must first be able to run a malicious code on the target system. It is possible to do so if a user clicks on a specially crafted website or if a user opens a specially crafted Microsoft Office document.
In Windows domain environments, Active Directory is enabled by default, which makes it a high risk to deploy in such environments. It is recommended that administrators disable Active Directory on domain controllers and disable user login to Active Directory by default. If you are running Windows 10, we recommend that you disable the ability to join a domain. To disable this feature, navigate to Settings > Accounts > Sign-in options > Never allow signing in with this device
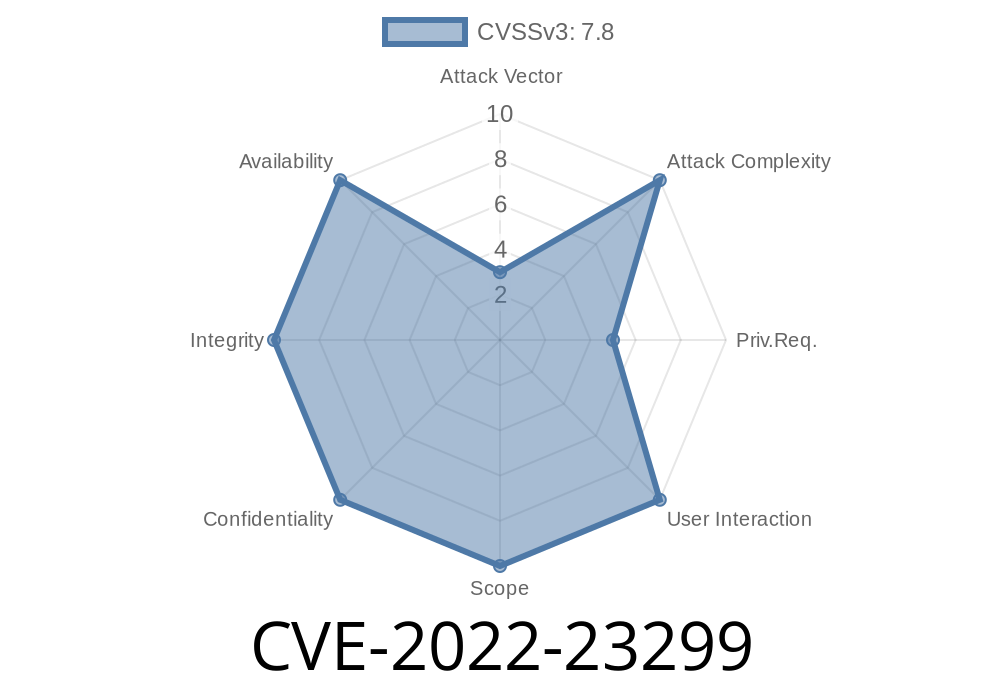
- CVE-2022-23299: A remote code execution vulnerability exists in Windows Domain Services that could allow an attacker to take advantage of this issue to install programs, view or change data, or create new accounts with full user rights. In order to exploit this issue, an attacker must first be able to run a malicious code on the target system
If you have any questions about how your business can benefit from digital marketing strategies then please contact our experts today!
Timeline
Published on: 03/09/2022 17:15:00 UTC
Last modified on: 05/23/2022 17:29:00 UTC