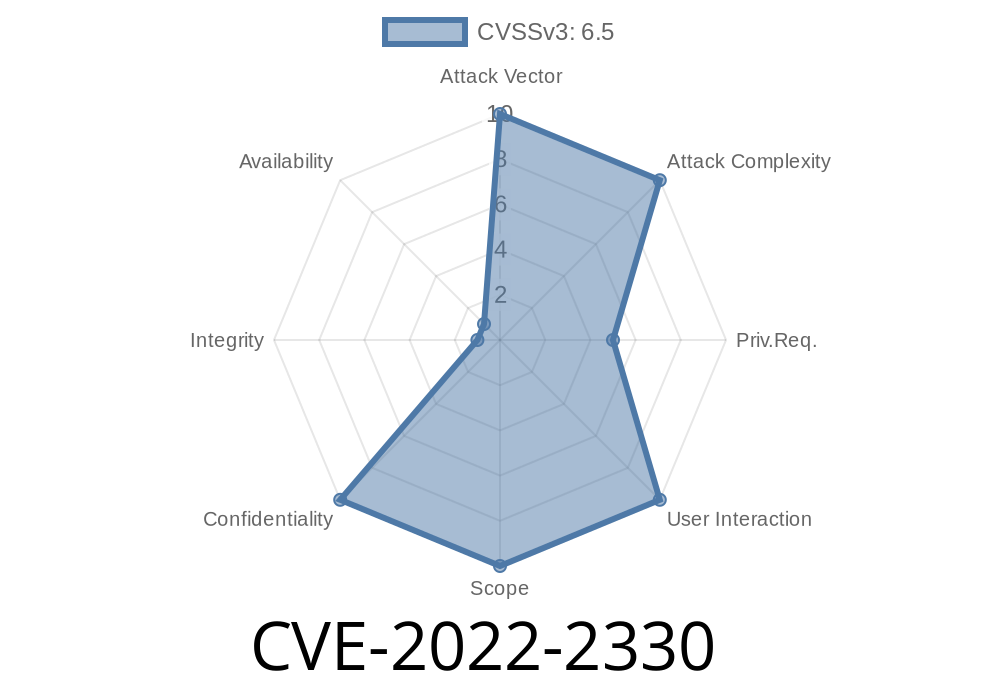
This issue can be exploited when DLP Agent processes a specially crafted XML file that contains one or more entity references to local Windows services, which are not whitelisted in the DLP policy. An attacker can send such a file to the DLP Agent with the intent of tricking the DLP Agent into executing code in a privileged context. This issue can be exploited when DLP Agent processes a specially crafted XML file that contains one or more entity references to local Windows services, which are not whitelisted in the DLP policy. An attacker can send such a file to the DLP Agent with the intent of tricking the DLP Agent into executing code in a privileged context.
Vulnerability details
A specially crafted XML file that contains one or more entity references to local Windows services, which are not whitelisted in the DLP policy, can be used to exploit this vulnerability. An attacker can send such a file to the DLP Agent with the intent of tricking the DLP Agent into executing code in a privileged context.
Vulnerability overview
An attacker can send a specially crafted XML file to the DLP Agent with the intent of tricking the DLP Agent into executing code in a privileged context.
Timeline
Published on: 08/30/2022 08:15:00 UTC
Last modified on: 09/15/2022 08:15:00 UTC