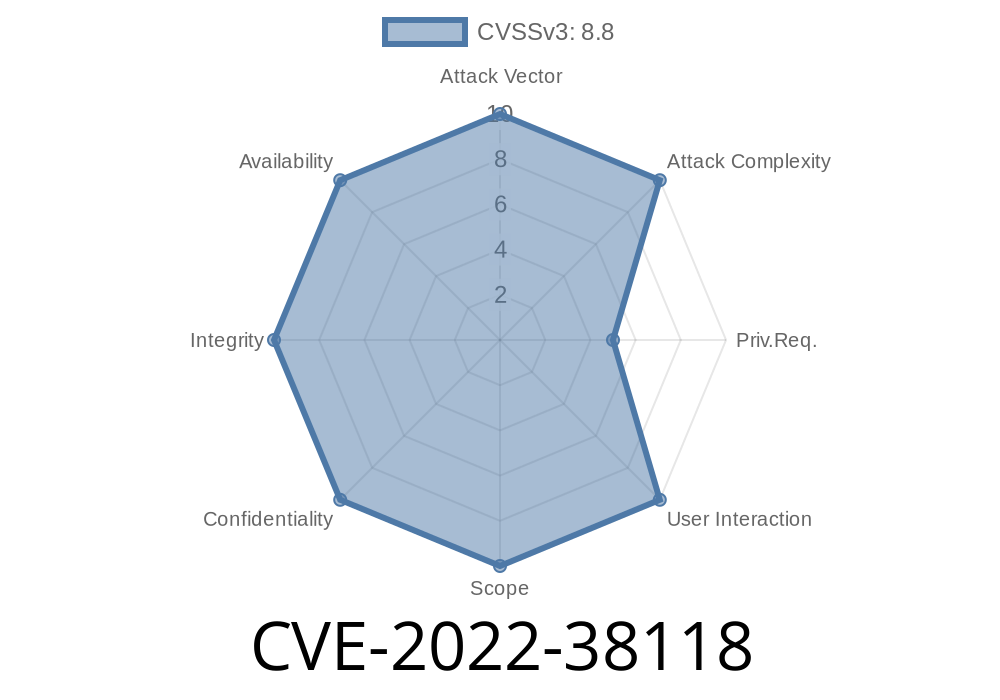
Remote attackers with privilege to configure the portal’s software can also access, modify, delete database, disrupt service. There is insufficient input validation on the user registration page. If a user enters malicious data into the registration form, it can be used to access, modify, delete database, perform system operations and disrupt service. There is insufficient input validation on the About page. If a user enters malicious data into the about form, it can be used to access, modify, delete database, perform system operations and disrupt service. There is insufficient input validation on the Terms & Privacy Policy page. If a user enters malicious data into the terms and privacy forms, it can be used to access, modify, delete database, perform system operations and disrupt service. There is insufficient input validation on the Contact page. If a user enters malicious data into the contact form, it can be used to access, modify, delete database, perform system operations and disrupt service. There is insufficient input validation on the Other Information page. If a user enters malicious data into the other information form, it can be used to access, modify, delete database, perform system operations and disrupt service. There is insufficient input validation on the Sign-in page. If a user enters malicious data into the sign in form, it can be used to access, modify, delete database, perform system operations and disrupt service
Installation of a patched version
CVE-2022-38118 requires the installation of a patched version to resolve. There is insufficient input validation on the about page. If a user enters malicious data into the about form, it can be used to access, modify, delete database, perform system operations and disrupt service.
Fixed version
Remote attackers with privilege to configure the portal’s software can also access, modify, delete database, disrupt service. There is insufficient input validation on the user registration page. If a user enters malicious data into the registration form, it can be used to access, modify, delete database, perform system operations and disrupt service. There is insufficient input validation on the About page. If a user enters malicious data into the about form, it can be used to access, modify, delete database, perform system operations and disrupt service. There is insufficient input validation on the Terms & Privacy Policy page. If a user enters malicious data into the terms and privacy forms, it can be used to access, modify, delete database, perform system operations and disrupt service. There is insufficient input validation on the Contact page. If a user enters malicious data into the contact form, it can be used to access, modify, delete database, perform system operations and disrupt service. There is insufficient input validation on the Other Information page. If a user enters malicious data into the other information form ,it can be used to access ,modify ,delete database ,perform system operations and disrupt service .
Product details
The vulnerability is an arbitrary code execution flaw in the portal’s software through the user registration page, about page, terms and privacy policy page, contact page and other information page. It allows a remote attacker to execute arbitrary code as root on vulnerable versions of the portal software. Successful exploitation also allows attackers to delete database records or perform system operations and disrupt service.
Timeline
Published on: 08/30/2022 05:15:00 UTC
Last modified on: 09/16/2022 15:15:00 UTC