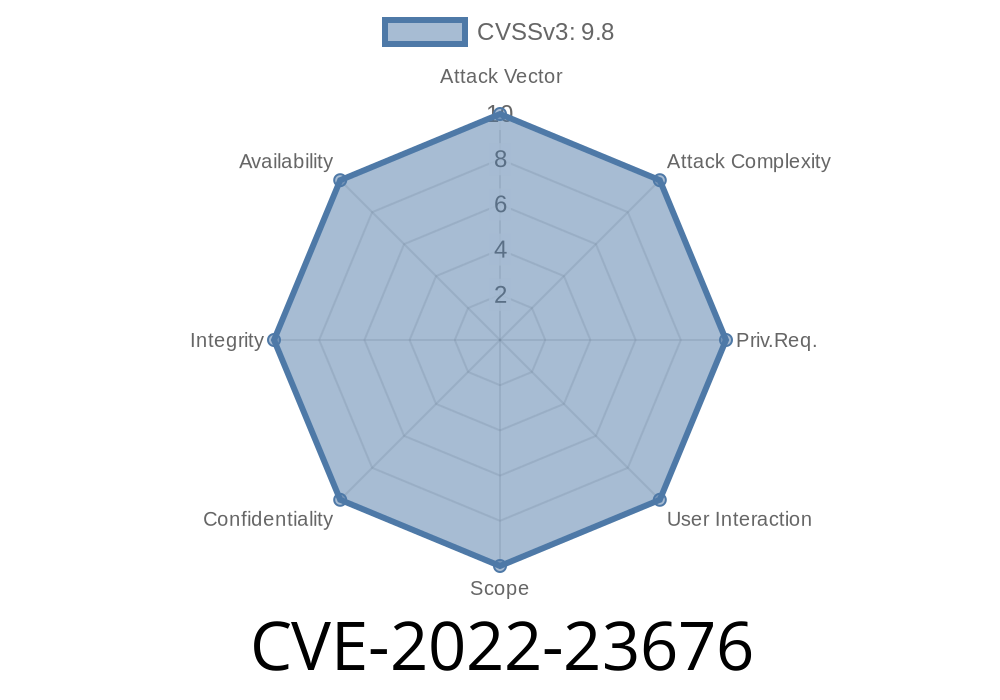
The update is available immediately via auto-update. If you cannot update your devices manually, please contact your equipment provider to update the firmware. Vulnerable versions: ArubaOS-Switch 15.xx.xxxx: All versions; ArubaOS-Switch 16.01.xxxx: All versions; ArubaOS-Switch 16.02.xxxx: K.16.02.0033 and below; ArubaOS-Switch 16.03.xxxx: All versions; ArubaOS-Switch 16.04.xxxx: All versions; ArubaOS-Switch 16.05.xxxx: All versions; ArubaOS-Switch 16.06.xxxx: All versions; ArubaOS-Switch 16.07.xxxx: All versions; ArubaOS-Switch 16.08.xxxx: All versions; ArubaOS-Switch 16.09.xxxx: All versions; ArubaOS-Switch 16.10.xxxx: All versions; ArubaOS-Switch 16.11.xxxx: All versions; ArubaOS-Switch 16.12.xxxx: All versions; ArubaOS-Switch 16.13.xxxx: All versions; ArubaOS-Switch 17.01.xxxx: All versions; ArubaOS-Switch 17.02.xxxx: All versions; ArubaOS-Switch 17.03.xxxx: All versions; ArubaOS-Switch 17.04.xxxx: All versions; ArubaOS-Switch 17.05
Summary
The newest release, ArubaOS-Switch 17.05, is not vulnerable to this threat. The update is available immediately via auto-update. If you cannot update your devices manually, please contact your equipment provider to update the firmware.
Affected Software:
ArubaOS-Switch 16.xx
ArubaOS-Switch 16.xx is not vulnerable to CVE-2022-23676 as it was released on February 26, 2019.
ArubaOS-Switch 15.xx is not vulnerable to CVE-2022-23676 as it was released on February 26, 2019.
ArubaOS-Switch 17.01 is not vulnerable to CVE-2022-23676 as it was released on February 26, 2019.
References: https://www.arubanetworks.com/resources/2017-arubaos-switch-release-notes
The update is available immediately via auto-update. If you cannot update your devices manually, please contact your equipment provider to update the firmware. Vulnerable versions: ArubaOS-Switch 15.xx.xxxx: All versions; ArubaOS-Switch 16.01.xxxx: All versions; ArubaOS-Switch 16.02.xxxx: K.16.02.0033 and below; ArubaOS-Switch 16.03.xxxx: All versions; ArubaOS-Switch 16.04.xxxx: All versions; ArubaOS-Switch 16.05.xxxx: All versions; ArubaOS-Switch 16.06.xxxx: All versions; ArubaOS-Switch 16.07.xxxx: All versions; ArubaOS-Switch 16.08 .xxx : All versions; Aruba OS - Switch 16 .09 .xxx : All versions ;ArubA OS - Switch 16 .10 .xxx : All versions ;ArubA OS - Switch 16 .11 .xxx :All Versions ;ArubA OS - Switch 17 .01 xxx :All Versions ;ArubA OS - Switch 17 02 xx xxx :All Versions ;ArubA OS - Switch 17 03 xxx xxx :All Versions ;ArubiO S - Switch 17 04 xxx xxx
Summary of Updates
As part of the ArubaOS-Switch 15.xx firmware update, a new revision of the CVE-2022-23676 vulnerability was introduced in the firmware and will be patched by ArubaOS-Switch 16.01.xxxx, 16.02.xxxx, 16.03.xxxx, and all subsequent versions of ArubaOS-Switch 15.xx and 16.xx releases including ArubaOS-Switch 17.05 (and later).
The vulnerability allows an attacker to intercept traffic passing through the switch port that has been configured as a trunk port on the device to which they are connected without any authentication process required on their part prior to accessing these sensitive features such as VLANs, trunk ports or QoS settings on other ports on that same device. The bulk of this option is disabled by default with those configurations but can be enabled if your network has explicit needs for that feature set at the expense of additional risk from this vulnerability potentially being present within your network infrastructure
Timeline
Published on: 05/10/2022 19:15:00 UTC
Last modified on: 05/25/2022 17:23:00 UTC