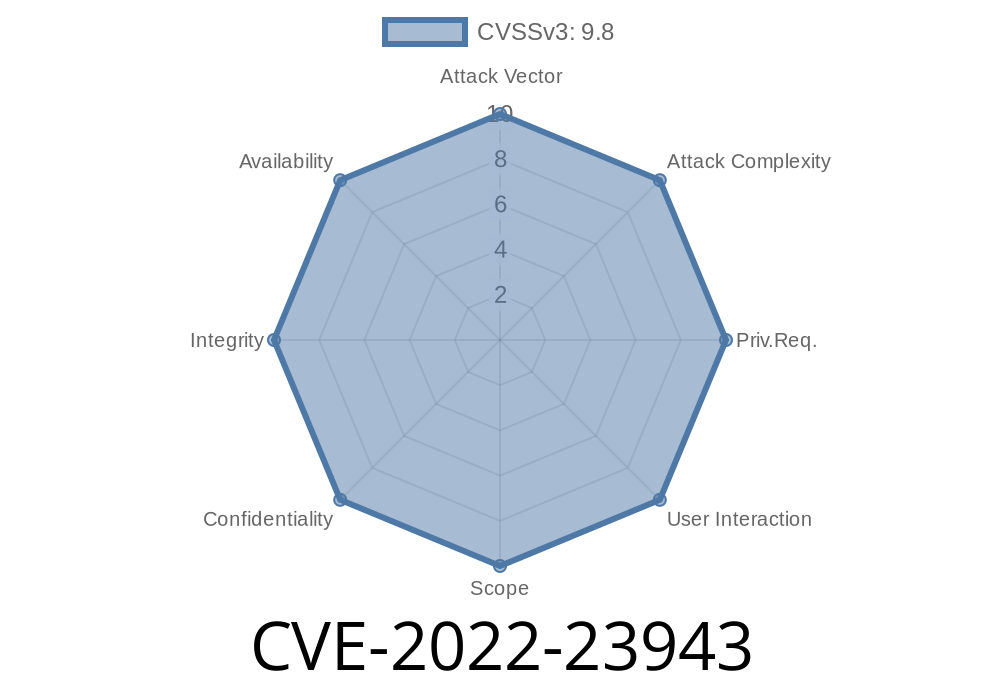
mod_sed is a stream filter module for Apache HTTPD web server. mod_sed is used for filtering requests before they are passed to a server program, typically a CGI program. This issue results in an attacker being able to send a specially crafted request which will cause the server to attempt to write data from the request's data stream into the server's heap memory, resulting in a crash of the server. This vulnerability can be exploited by attackers with low privileged user rights. This issue only affects installations that have mod_sed enabled. With mod_sed enabled, you can get an Out-of-bounds Write in mod_sed as follows. 1. On Debian/Raspbian, edit the /etc/apache2/mods-enabled/nologin.conf file and add a new line after the '#' character like below. IfModule mod_sed_module> Filter_ passes_as_doc_stream "A HREF=\"\" data for user-agent\">" Filter_pass_through "script>alert('XSS');/script>" /IfModule> This will allow you to put HTML code in the data stream. 2. Change to the /var/www/html/subdirectory/subdirectory/subdirectory/subdirectory/subdirectory/ subdirectory/subdirectory/subdirectory/subdirectory/subdirectory/subdirectory/subdirectory/subdirectory/subdirectory/subdirectory/subdirectory/ subdirectory/
2
. Change to the /var/www/html/subdirectory/subdirectory/subdirectory/subdirectory/ subdirectory/subdirectory/subdirectory/subdirectory/subdirectory/subdirectory/subdirectory/subdirectory
Timeline
Published on: 03/14/2022 11:15:00 UTC
Last modified on: 08/15/2022 11:18:00 UTC
References
- https://httpd.apache.org/security/vulnerabilities_24.html
- http://www.openwall.com/lists/oss-security/2022/03/14/1
- https://security.netapp.com/advisory/ntap-20220321-0001/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/RGWILBORT67SHMSLYSQZG2NMXGCMPUZO/
- https://lists.debian.org/debian-lts-announce/2022/03/msg00033.html
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/Z7H26WJ6TPKNWV3QKY4BHKUKQVUTZJTD/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/X73C35MMMZGBVPQQCH7LQZUMYZNQA5FO/
- https://www.tenable.com/security/tns-2022-08
- https://www.oracle.com/security-alerts/cpuapr2022.html
- https://www.tenable.com/security/tns-2022-09
- https://security.gentoo.org/glsa/202208-20
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-23943