An attacker could exploit this vulnerability to obtain information such as encryption keys, financial data, or other information. You can protect your organization by monitoring for signs of cache allocation attacks. If you notice an unusual increase in cache activity, you might have an attacker trying to leak information. What to look out for: cache allocation issues (e.g., unusually large cache sizes, cache growing over time)
sudden cache activity outside of normal workloads
Cache allocations that occur between branches Why to monitor: This vulnerability exists in all processor types, so any vulnerable processor could be used to leak information. What to monitor: Processors — Any Intel, AMD, or ARM v5 processor types.
Anchor — Any v5 processor type.
Intel Cache Allocation Vulnerabilities
Intel's Cache Allocation vulnerabilities allow an attacker to use code execution to read data from the L1 cache of a target processor. This allows for information disclosure and worse, could allow for privilege escalation.
The vulnerability is found on all Intel processors, but each processor has different mitigation capabilities. For example, the vulnerability exists on all v5 processor types and will be mitigated on most v2 and v3 processors.
This is one of many vulnerabilities in 8-series chipsets that can be exploited by attackers to inject malicious code into the kernel space of the system.
Intel Cache Allocation Vulnerability
An attacker could exploit this vulnerability to obtain information such as encryption keys, financial data, or other information. You can protect your organization by monitoring for signs of cache allocation attacks. If you notice an unusual increase in cache activity, you might have an attacker trying to leak information. What to look out for: cache allocation issues (e.g., unusually large cache sizes, cache growing over time)
sudden cache activity outside of normal workloads
Cache allocations that occur between branches Why to monitor: This vulnerability exists in all processor types, so any vulnerable processor could be used to leak information. What to monitor: Processors — Any Intel, AMD, or ARM v5 processor types.
Anchor — Any v5 processor type.
Intel CPU Cache Allocation Vulnerabilities
An attacker can exploit this vulnerability to obtain information such as encryption keys, financial data, or other information. You can protect your organization by monitoring for signs of cache allocation attacks. If you notice an unusual increase in cache activity, you might have an attacker trying to leak information. What to look out for: cache allocation issues (e.g., unusually large cache sizes, cache growing over time)
sudden cache activity outside of normal workloads
Cache allocations that occur between branches Why to monitor: This vulnerability exists in all processor types, so any vulnerable processor could be used to leak information. What to monitor: Processors — Any Intel, AMD, or ARM v5 processor types.
Anchor — Any v5 processor type.
Intel Processors
Cache Allocations in Intel Processors:
You can monitor all of the cache allocations in an Intel processor using the icache_info tool. You can also view a specific cache allocation by using the command below:
# icache_info -peh
Timeline
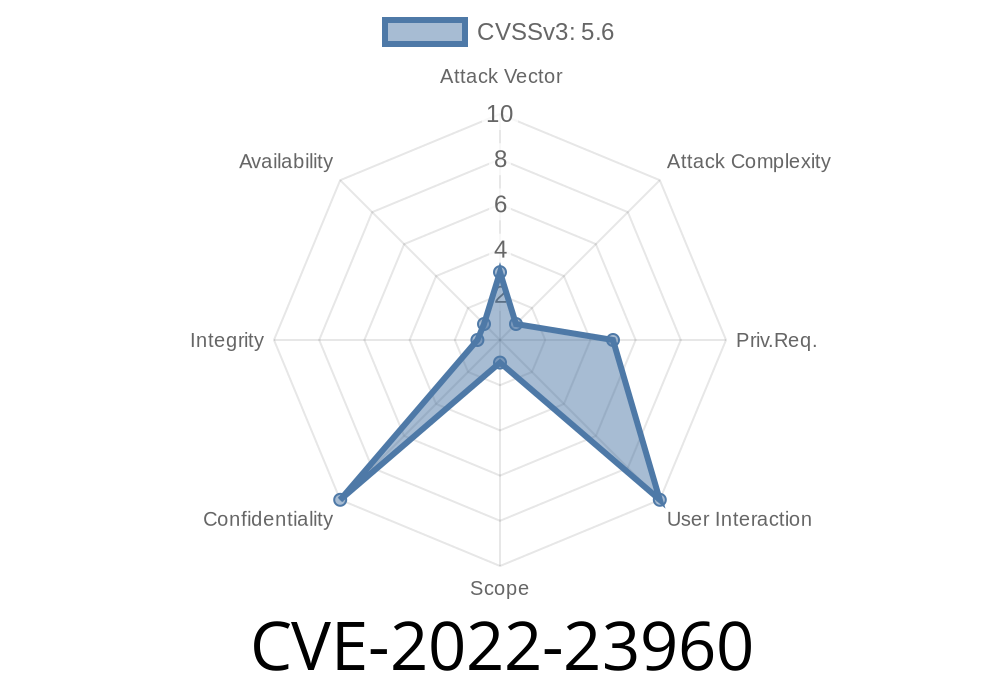
Published on: 03/13/2022 00:15:00 UTC
Last modified on: 07/04/2022 11:15:00 UTC
References
- https://developer.arm.com/support/arm-security-updates/speculative-processor-vulnerability
- https://developer.arm.com/support/arm-security-updates
- http://www.openwall.com/lists/oss-security/2022/03/18/2
- https://lists.debian.org/debian-lts-announce/2022/07/msg00000.html
- https://www.debian.org/security/2022/dsa-5173
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-23960