The issue was discovered by Michal Zalewski from Google’s Project Zero team. The vulnerability affects the JPEG and PNG image formats, allowing remote attackers to execute arbitrary code on vulnerable installations of Heif-enabled applications. The attack vector is related to image parsing, as the affected formats allow the inclusion of arbitrary JavaScript code. The problem exists in the handling of PNG and JPEG images with a ‘magic’ value of 80 (PNG) or 49 (JPEG) that contain JavaScript code. If a user were to view a maliciously crafted image on a website, the JavaScript code would be executed in the context of the user’s web browser. The severity of the issue depends on the type of application using the Heif image format. An attacker can exploit the vulnerability via any of the following scenarios: In a web application that uses the Heif image format, an attacker can host a crafted image on a website. When the user visits the website and views the image, the code is executed in the context of the user’s web browser. In a mobile application that uses the Heif image format, an attacker can send a crafted application to a user’s device. When the user launches the application, the code is executed in the context of the user’s mobile device. In a native application that uses the Heif image format, an attacker can send a crafted application to a user’s device. When the user launches the application
Finding and fixing Heif vulnerabilities
Heif is a common format for the storage of JPEG and PNG images in web pages. This vulnerability affects all versions of the software, including in Adobe Photoshop, Illustrator, InDesign, CorelDRAW and Microsoft Office applications.
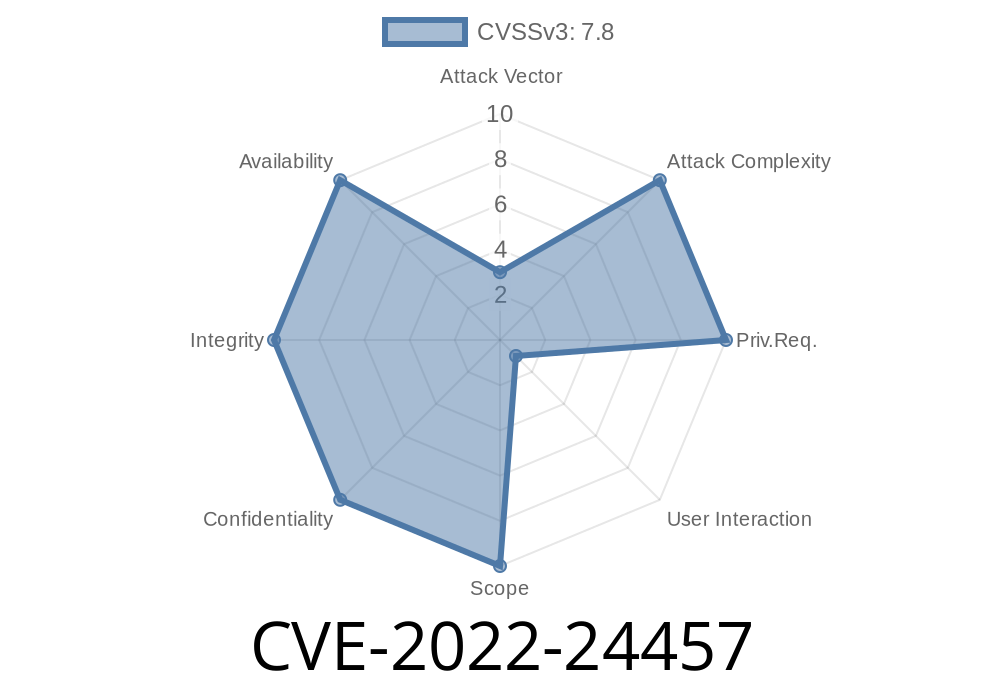
The vulnerability was discovered by Michal Zalewski from Google’s Project Zero team. The issue has been assigned CVE-2022-24457. If you have any Heif-enabled applications on your network that are vulnerable to this issue, please contact your IT administrators immediately. Your IT administrators will be able to help mitigate this issue by ensuring that the appropriate patches have been applied on their systems. Please note that this patch will only prevent malicious JavaScript code from being executed; it will not eliminate the risk of attackers exploiting this vulnerability more generally.
Vulnerability overview
The vulnerability was discovered by Michal Zalewski from Google’s Project Zero team. The issue affects the JPEG and PNG image formats, allowing remote attackers to execute arbitrary code on vulnerable installations of Heif-enabled applications. The attack vector is related to image parsing, as the affected formats allow the inclusion of arbitrary JavaScript code.
The problem exists in the handling of PNG and JPEG images with a ‘magic’ value of 80 (PNG) or 49 (JPEG) that contain JavaScript code. If a user were to view a maliciously crafted image on a website, the JavaScript code would be executed in the context of the user’s web browser. The severity of the issue depends on the type of application using the Heif image format. An attacker can exploit the vulnerability via any of the following scenarios:
In a web application that uses the Heif image format, an attacker can host a crafted image on a website. When the user visits the website and views the image, the code is executed in the context of the user’s web browser. In a mobile application that uses the Heif image format, an attacker can send an app to a user’s device. When they launch it, it is executed in their mobile device's context and would have access to all available resources on their device (e.g., camera). In a native application that uses Heif format, an attacker could send an app to a user's phone when
What is Heif?
Heif is a format that allows users to send small images and videos of up to 1 megabyte in size. Despite the small file size, it supports progressive image loading, which means that the image or video will not be fully loaded until the user actually needs it.
Timeline
Published on: 03/09/2022 17:15:00 UTC
Last modified on: 03/14/2022 18:45:00 UTC