It was discovered that the .NET Framework hosted on Windows Server, Windows 8, Windows 8.1 and Windows 10 can be easily exploited to cause Denial of Service. In other words, a remote attacker could send a specially-crafted HTTP request to the targeted system and cause it to crash. Microsoft has released a patch for this vulnerability. However, it is advised to apply the update as soon as possible. If your system is still running Windows 7 or Windows Server 2008, you may want to consider upgrading the system to Windows 10 or Windows 8.1 as soon as possible.
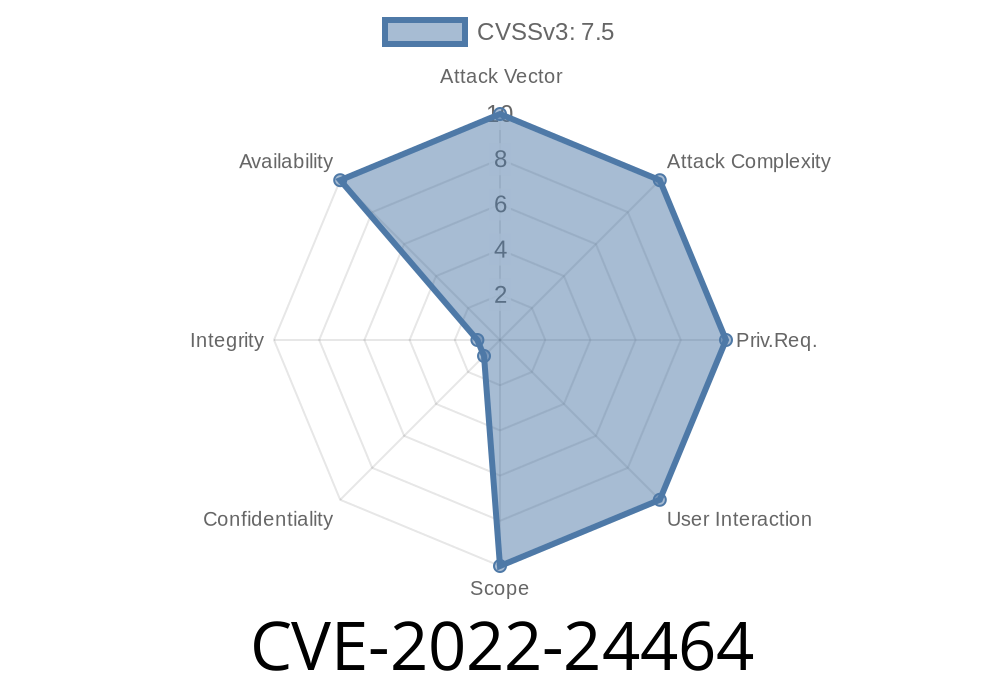
Microsoft .NET Framework Remote Code Execution Vulnerability – CVE-2022-24464
This vulnerability can be accessed by sending a specially-crafted HTTP request to the targeted system. The vulnerability could be exploited by an unauthenticated, remote attacker to cause a Denial of Service.
Microsoft has released a patch for this vulnerability and it is advised to apply the update as soon as possible. If your system is still running Windows 7 or Windows Server 2008, you may want to consider upgrading the system to Windows 10 or Windows 8.1 as soon as possible.
Microsoft .NET Framework Remote Code Execution Vulnerability
The vulnerability allows attackers to crash the targeted system if they send a specially-crafted HTTP request. This vulnerability is identified as CVE-2022-24464 and was discovered by security researcher Eric Romang.
Microsoft has released a patch for this vulnerability, which allows users to protect their systems from this exploit. However, it is suggested that users apply the patch as soon as possible
How to Check if I am Vulnerable?
If you are using Windows Server 2008 or an earlier version, you may want to consider upgrading the system to either Windows 10, Windows 8.1, or Windows 7 as soon as possible.
If your system is running a later version of the .NET Framework and you believe that it is not vulnerable to this vulnerability, then it may be best for you to wait until Microsoft releases updated software that addresses this issue. If your system meets these requirements but is still hosting older versions of the .NET Framework, then it is advised that you apply a patch.
For more information on how to do so, please visit Microsoft's advisory page for CVE-2022-24464.
Check if you are affected by CVE-2022-24464
To check if your system is affected by the vulnerability, use the following steps:
1. Open Windows PowerShell as an administrator and enter "Get-Help *Denial of Service*" to retrieve a list of commands.
2. Enter "Get-WmiObject Win32_OperatingSystem - filters oSVersion, osServicePack" to retrieve a list of compatible operating systems.
3. Enter "cpwsfpruntime missing 0x80070005" on your command prompt to check for the presence of RtlVerifyVersionInfoW in the system's registry. If it does not exist or is missing from the registry, your system may be vulnerable to exploitation.
4. To verify whether you are vulnerable or not, enter "try { New-Object Net.WebClient } catch { throw }" on your command prompt and press enter to initiate a denial-of-service attack against yourself. If you see that it did not work, then you are not vulnerable to this vulnerability and should continue with other tasks as normal.
Timeline
Published on: 03/09/2022 17:15:00 UTC
Last modified on: 05/12/2022 16:26:00 UTC
References
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2022-24464
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/MRGSPXMZY4RM2L35FYHCXBFROLC23B2V/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/OS2Q4NPRSARP7GHLKFLIYHFOPSYDO6MK/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/ZXEQ3GQVELA2T4HNZG7VPMS2HDVXMJRG/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/CIJGCVKLHVNLFBTEYJGWS43QG5DYJFBL/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/MQLM7ABVCYJLF6JRPF3M3EBXW63GNC27/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/4TOGTZ2ZWDH662ZNFFSZVL3M5AJXV6JF/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-24464