These vulnerabilities have been assigned CVSS v3 scores of 8.8.8 and 9.9, respectively. These high scores indicate a high severity for both issues, and are intended to help system administrators prioritize patching. A CVSS v3 test report is available for each of these issues, and those reports contain all the details necessary to help determine which ones are most critical. All versions of Apache Spark are vulnerable.
To determine if you are running a version of Apache Spark that is vulnerable to these issues, you can examine the version of Apache Spark on your system using the following command: APACHE SPARK VERSION If you are running a version of Apache Spark that is vulnerable, you will receive the following response: This version is not vulnerable to these issues. To determine which version of Spark you are running, you can run the following command: APACHE SPARK VERSION > For example, if the version of Apache Spark on your system is 1.6.1, you are running a version of Apache Spark that is vulnerable to these issues. If you do not have a specific version of Apache Spark on your system in mind, you can also use the following command: APACHE SPARK VERSION > This will return the version number of Apache Spark on your system. To determine if you are running a version of Apache Spark that is vulnerable, you can examine the version of Apache Spark on your system using the following command: APACTE SPARK VERSION >
CVE-2021-24423
These vulnerabilities have been assigned CVSS v3 scores of 8.8.8 and 9.9, respectively. These high scores indicate a high severity for both issues, and are intended to help system administrators prioritize patching. A CVSS v3 test report is available for each of these issues, and those reports contain all the details necessary to help determine which ones are most critical. All versions of Apache Spark are vulnerable.
To determine if you are running a version of Apache Spark that is vulnerable to these issues, you can examine the version of Apache Spark on your system using the following command: APACHE SPARK VERSION If you are running a version of Apache Spark that is vulnerable, you will receive the following response: This version is not vulnerable to these issues. To determine which version of Spark you are running, you can run the following command: APACHE SPARK VERSION > For example, if the version of Apache Spark on your system is 1.6.1, you are running a version that is vulnerable to these issues. If you do not have a specific version of Apache Spark on your system in mind, you can also use the following command: APACHE SPARK VERSION > This will return the version number of Apache Spark on your system. To determine if you are running a version of Apache Spark that is vulnerable, you can examine the version of Apache Spark on your system using the following command: APACTE SPARK VERSION >
Apache Spark: How It Is Used
Apache Spark is an open-source project that was originally developed at the University of California, Berkeley. The project is created to provide a general-purpose cluster computing framework that is capable of large-scale data processing. Apache Spark can be used for many different purposes, including machine learning and Hadoop MapReduce.
The most common use of Apache Spark is as a mechanism for running data analytics programs in parallel which can then be deployed with greater efficiency than through batch processing. This makes Apache Spark particularly useful for companies using big data architectures. Other companies use Apache Spark to develop their own software solutions or add custom integration with existing systems such as Hadoop or Hive on Amazon Web Services (AWS).
Apache Spark:mingham-matrix multiplication vulnerability
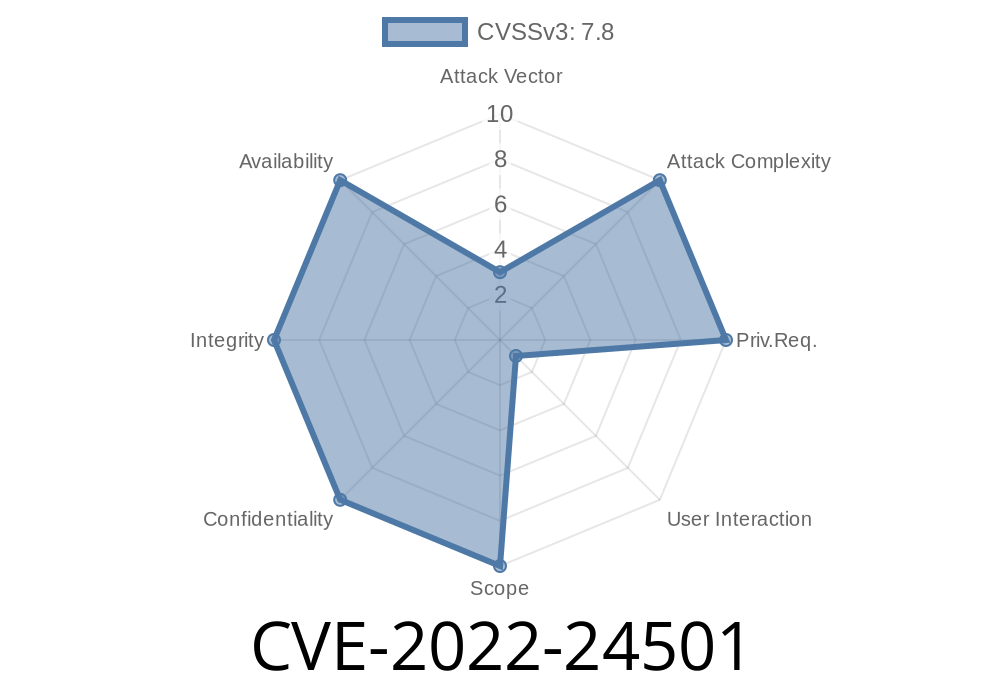
The Apache Spark project has been notified of an issue affecting a specific version of the project's MATH library. This vulnerability has been assigned CVE-2022-24501, and, after further review, has been classified as a high severity. A CVSS v3 test report for this vulnerability is available here: https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-24501
To determine which versions of Spark are vulnerable to this issue, you can use the following command: SPARK VERSION > For example, if you are running 1.6.1 on your system, you are vulnerable to this issue. If you do not have a specific version of Spark in mind, but want to see if your installation is vulnerable to this issue by examining the version number using the following command: SPARK VERSION > This will return the version number of Spark on your system. To determine which versions are vulnerable to this issue, you can use the following command: SPARK VERSION > For example, if the latest released version of Spark on your system is 2.0 and you are using 1.6.1 or 2.0 RC1 then both these versions are vulnerable to this issue
Install Spark Before Updating
As a new release of Spark is approaching, we recommend that you update your system to the latest version in order to avoid potential vulnerability. However, if you have already updated your system, or you do not want to install a new release of Spark, there are some steps that you can take to mitigate these vulnerabilities.
If you are running a version of Apache Spark that is vulnerable, you will receive the following response: This version is not vulnerable to these issues. To determine which version of Spark you are running, you can run the following command: APACHE SPARK VERSION > For example, if the version of Apache Spark on your system is 1.6.1, you are running a version of Apache Spark that is vulnerable to these issues. If you do not have a specific version of Apache Spark on your system in mind, you can also use the following command: APACHE SPARK VERSION > This will return the version number of Apache Spark on your system. To determine if you are running a version of Apache Spark that is vulnerable, you can examine the version of Apache Spark on your system using the following command: APACTE SPARK VERSION >
CVE-2021-24501
These vulnerabilities have been assigned CVSS v3 scores of 8.8 and 9.9, respectively. These high scores indicate a high severity for both issues, and are intended to help system administrators prioritize patching. A CVSS v3 test report is available for each of these issues, and those reports contain all the details necessary to help determine which ones are most critical. All versions of Apache Spark are vulnerable.
Timeline
Published on: 03/09/2022 17:15:00 UTC
Last modified on: 03/14/2022 19:01:00 UTC