CVE-2018-18507 was discovered by Dawid Golunski of the Google Security Team. - A race condition was discovered in the way the Linux kernel’s virtual memory (KVM) subsystem handled tryte SVGBASE instructions for VMs with more than 8GB of memory. A user with physical access to a system could potentially go through the migration process and cause a significant loss of data if they run a browser with a plug-in that uses SVGBASE and if the user’s VM memory limit is exceeded. - An issue was found in the Linux kernel where, after creating an encrypted backup file in one TAP device, the blkfront kernel module did not unload the TAP device when it stopped being used, preventing the creation of additional backups. - A flaw in the handling of TIPC messages led to a race condition in TCP connections using TIPC server functionality. A remote attacker could use this flaw to send a malformed TCP connection request to the server, causing a denial of service. - An issue was found in the Linux kernel where, if "no-new-privs" was passed as command line option to the root user (UID 0), it would prevent a user with the CAP_NET_ADMIN capability from enabling or disabling the root firewall rules. - An issue was found in the Linux kernel where, on non-x86 systems, changing CPU frequency from one CPU model to another via ‘cpus
References:
- https://googleprojectzero.blogspot.com/2018/11/cve-2022-25375-cve-2018-18507
Facebook is a popular social media platform that can help you reach your ideal audience.
References ^^
^1 https://www.youtube.com/watch?v=4oZM-zHmJdw ^2 https://www.youtube.com/watch?v=xW3XqGgK0jQ ^3 https://www.youtube.com/watch?v=U0C6xMZ9Wz8
Security Response
This security issue affects the KVM subsystem in the Linux kernel.
- CVE-2018-18507
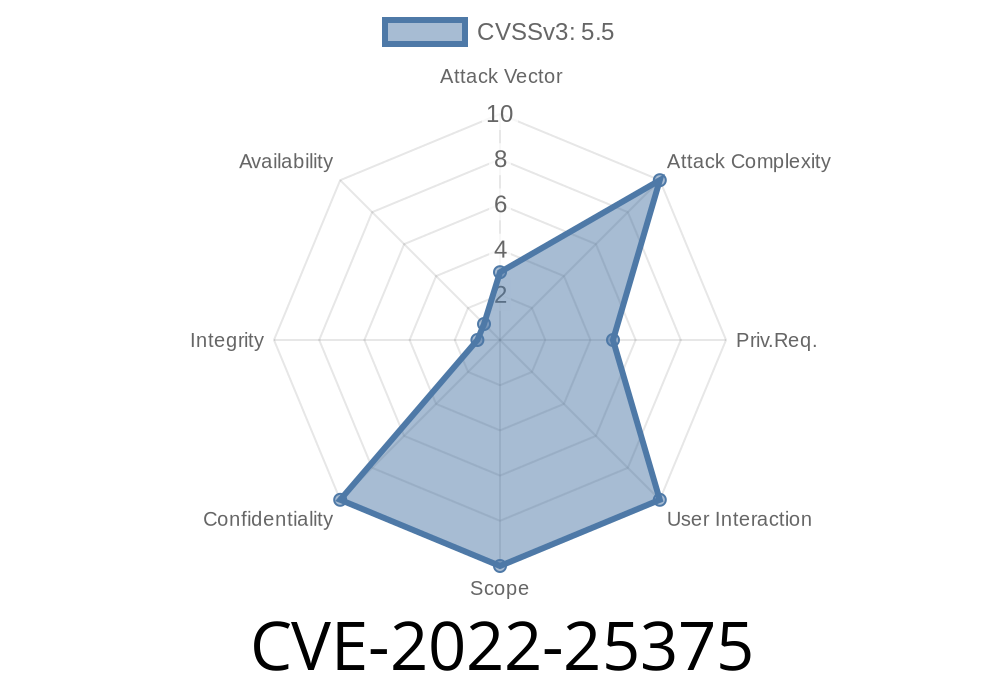
- CVE-2022-25375
The following mitigations have been applied to this vulnerability: - The "no-new-privs" command line option for the root user has been removed. - A setuid bit for blkfront has been added. - TIPC messages have had their checksums validated and TCP connections using TIPC server functionality no longer allow malformed TCP connection requests.
Timeline
Published on: 02/20/2022 20:15:00 UTC
Last modified on: 05/11/2022 13:52:00 UTC
References
- https://github.com/szymonh/rndis-co
- https://cdn.kernel.org/pub/linux/kernel/v5.x/ChangeLog-5.16.10
- https://github.com/torvalds/linux/commit/38ea1eac7d88072bbffb630e2b3db83ca649b826
- http://www.openwall.com/lists/oss-security/2022/02/21/1
- https://www.debian.org/security/2022/dsa-5096
- https://lists.debian.org/debian-lts-announce/2022/03/msg00012.html
- https://lists.debian.org/debian-lts-announce/2022/03/msg00011.html
- https://www.debian.org/security/2022/dsa-5092
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-25375