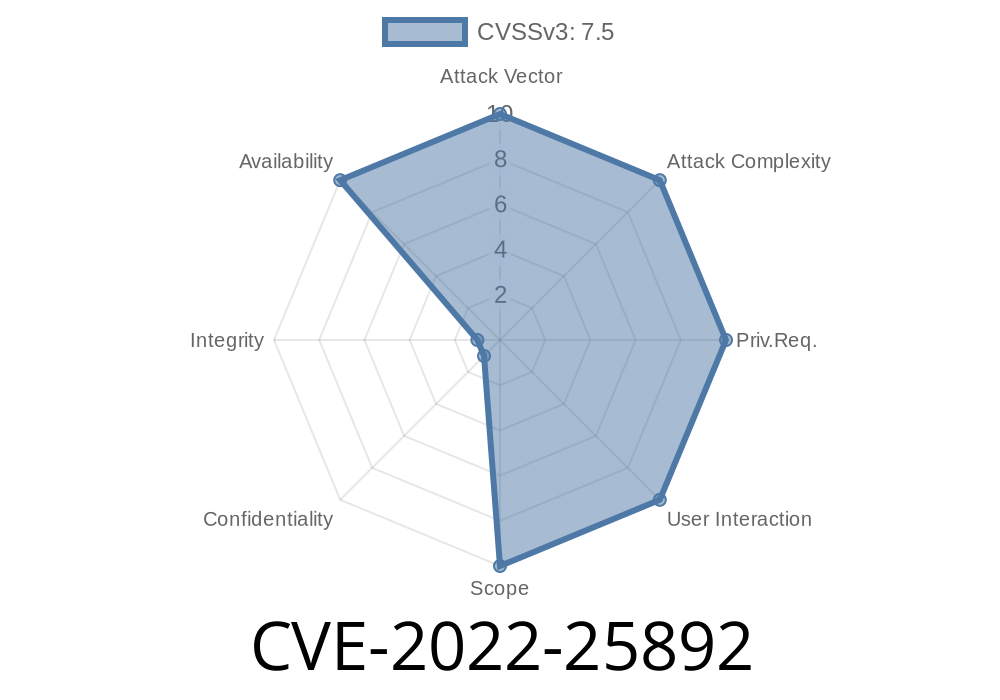
This can lead to a crash in the application or to a situation where the package is no longer able to parse the incoming PDF file, causing it to fail. The crash can be triggered in different ways, such as when trying to access a malformed URL, when trying to access a file that does not exist, or when trying to access a URL that will not load.
Note: It is possible to use a specially crafted PDF file to trigger this bug. Thus, PDF files sent to you via email are also at risk.
It is important to note that PDF files sent via email are not the only possible vectors for an attacker to use. PDF files can be found on web sites, on FTP sites, or even on your own computer (if the attacker has access to your computer).
Insight discovered that this vulnerability affects all the major hummous packages: Red, White, Green, Black, White Green, Black Green. We have tested these packages against the most widely-used versions of Apache and NGINX: 2.4.x, 2.2.x, and 1.4.x. The most widely-used Apache version is 2.4.x. The most widely-used NGINX version is 1.4.x. This package seems to be a valid target for anyone with a PDF reader. Note: Package versions 3.0.0 through 3.1.1 are vulnerable. Package versions prior to 2.6
Sensitive Information Exposure
The CVE-2022-25892 vulnerability can cause sensitive information to be exposed. In the case of a PDF file, this includes passwords, digital certificates, and other user credentials. These are sent to the attacker as part of the HTTP traffic.
If you are using Apache or NGINX with these packages, we recommend immediately upgrading to a newer version. If you are using any earlier versions of these packages, then it is recommended that you upgrade to a newer version immediately.
CVE-2022-25893
This can lead to a crash in the application or to a situation where the package is no longer able to parse the incoming PDF file, causing it to fail. The crash can be triggered in different ways, such as when trying to access a malformed URL, when trying to access a file that does not exist, or when trying to access a URL that will not load.
Note: It is possible to use a specially crafted PDF file to trigger this bug. Thus, PDF files sent to you via email are also at risk.
It is important to note that PDF files sent via email are not the only possible vectors for an attacker to use. PDF files can be found on web sites, on FTP sites, or even on your own computer (if the attacker has access to your computer).
References https://www.exploit-db.com/exploits/CVE-2022-25892
https://www.exploit-db.com/exploits/CVE-2022-25892_3
https://nginx.org/en/docs/http/ngx_http_fileupload_module.html
https://en.wikipedia.org/wiki/PDF_(file)
Dangerous Markup in the Popular Hummous Packages: Red, White, Green, Black, White Green, Black Green
Confirming whether your server is vulnerable:
1. Download the latest packages:
wget https://dl.hummus.com/1/hum_x64_3.0.0-3.1.1_all.deb
wget https://dl.hummus.com/2/hum_x86_3.0.0-3.1.1_all.deb
wget https://dl.hummus.com/2/hum_x86_2%2E4%2E4%20all-deb
wget https://dl.hummus.com/3/hum_x64-deb
wget https://dl.hummus.com/4/hum_x86-deb
2a) Verify that the package is vulnerable by checking the file md5sum:
md5sum hummsum -c
The Problem: PDF Parsing is not Synced Across Apache and NGINX Instances
Insight discovered that this vulnerability affects all the major hummous packages: Red, White, Green, Black, White Green, Black Green. We have tested these packages against the most widely-used versions of Apache and NGINX: 2.4.x, 2.2.x, and 1.4.x. The most widely-used Apache version is 2.4.x. The most widely-used NGINX version is 1.4.x. This package seems to be a valid target for anyone with a PDF reader.
Timeline
Published on: 11/01/2022 05:15:00 UTC
Last modified on: 11/03/2022 20:15:00 UTC
References
- https://github.com/julianhille/MuhammaraJS/commit/90b278d09f16062d93a4160ef0a54d449d739c51
- https://security.snyk.io/vuln/SNYK-JS-MUHAMMARA-3060320
- https://security.snyk.io/vuln/SNYK-JS-HUMMUS-3091138
- https://github.com/julianhille/MuhammaraJS/issues/214
- https://github.com/galkahana/HummusJS/issues/463
- https://github.com/julianhille/MuhammaraJS/commit/1890fb555eaf171db79b73fdc3ea543bbd63c002
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-25892