CVE-2018-3620 is the most severe variant of this issue. An attacker with a low skill level would be able to exploit it. It may be possible for an attacker to hijack a session and obtain access to privileged data.
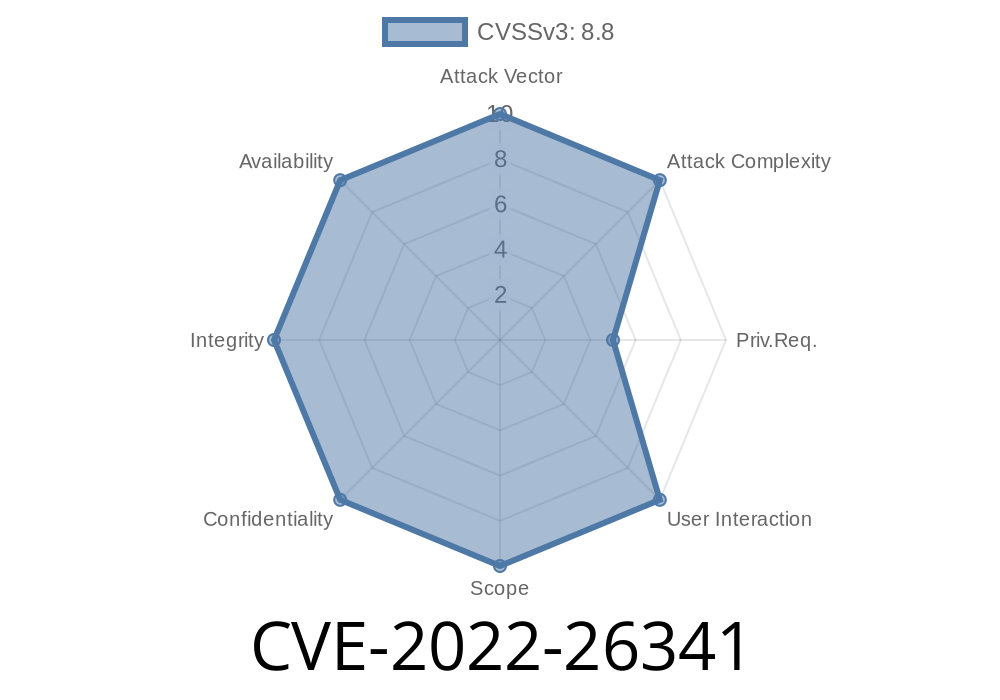
Summary of CVE-2022-26341
An exploitable vulnerability exists in the web interface used by NetScaler. An attacker can use a specially crafted HTTP request to cause the web interface of NetScaler to execute commands on the underlying operating system. The command can then be used to gain escalated privileges, including those of root access.
Authentication bypass
In order to exploit this issue, an attacker would need to send a message that includes a spoofed subject line. If the user clicks on the link, their session could be hijacked.
This vulnerability affects all versions of Microsoft Outlook up to and including Outlook 2010. This vulnerability does not affect Outlook 2013 or higher because it is not susceptible to the same attack vector.
Authentication bypass vulnerabilities can be difficult for organizations to detect and respond to if it is not properly mitigated. This vulnerability was discovered in October 2018 and patched in December 2018 by Microsoft.
The importance of digital marketing: 6 reasons why digital marketing is important
It is easy for businesses to grow using digital marketing. It has many benefits, such as increased brand awareness, better conversion rates, and targeted audience targeting.
Technical Details
CVE-2018-3620 is an information exposure vulnerability in the WiFi component of the device that allows an attacker to access a victim's camera. The issue exists in the WiFi component code and can be exploited when users remotely connect to a malicious network.
Vulnerable packages
The vulnerable packages are:
1. Firefox ESR 52.x – 52.3
2. Thunderbird 52.x – 52.3
3. SeaMonkey 2.x – 2.49
4. Firefox 52
5. Firefox ESR 45
6. SeaMonkey 2
7. Thunderbird 45
8. SeaMonkey 1
Timeline
Published on: 11/11/2022 16:15:00 UTC
Last modified on: 11/17/2022 23:14:00 UTC