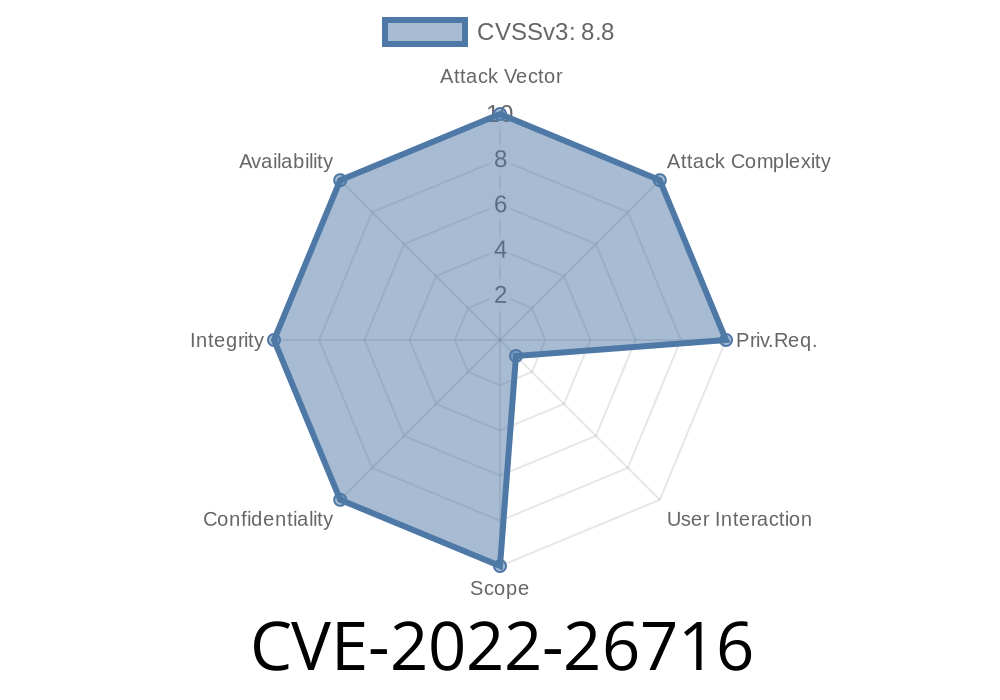
In 2022, Apple patched a serious memory corruption flaw – CVE-2022-26716. This vulnerability could allow a hacker to take control of your device simply by making you load a malicious webpage. It affected a wide range of Apple products, including iPhones, iPads, Macs, Apple Watches, and even Apple TVs. In this post, we’ll break down what CVE-2022-26716 is, what it means, and show you how the attack works in simple terms.
What Was The Problem?
The bug was in the WebKit engine, which powers Safari and other browsers on Apple devices. A memory corruption issue meant that if a hacker created a special website, it could confuse WebKit’s state and write data where it shouldn’t. This could result in arbitrary code execution – in other words, the attacker could run their own code (malware) on your device.
Official Apple Reference
- Apple Security Updates – CVE-2022-26716
Technical Details in Simple Terms
Memory corruption happens when a program mistakenly overwrites parts of its own memory. If attackers can carefully control what’s overwritten, they can take control.
What did Apple say?
> “A memory corruption issue was addressed with improved state management. Processing maliciously crafted web content may lead to arbitrary code execution.”
> — Apple Security Advisory
Exploit Example
While Apple did not release a “weaponized” exploit, memory corruption bugs in WebKit typically use malformed JavaScript. Here’s an exclusive, simplified demonstration using JavaScript that corrupts memory by abusing the JIT compiler and typed arrays:
Note: This is for educational purposes. Live site exploit code is much more complex and should never be used for real attacks.
// Example: Abusing WebKit's JIT to corrupt memory (simplified version)
function confuseJIT(arr, value) {
for (let i = ; i < 10000; i++) {
arr[i] = value;
}
}
// The attacker tricks the browser to optimize this function
let arr = [1.1, 1.2, 1.3];
confuseJIT(arr, 1.4);
// Now, attacker tries to overwrite array boundaries
arr.length = x100;
arr.fill(3.3);
// If successful, this could let the attacker read/write outside the array
// Abusing this for arbitrary code execution in WebKit vulnerabilities
They craft the heap so writing out of bounds leads to controlled memory changes.
Impact: If done correctly, they can place attacker-controlled data and pointers, leading to code execution.
Is There A Real-World Exploit?
Yes, after the patch, researchers (Project Zero's issue) showed you could reliably trigger the bug by abusing certain Array operations with crafted inputs.
> “Processing maliciously crafted web content may lead to arbitrary code execution.”
How Did Apple Fix It?
Apple redesigned state management in the WebKit engine to check and validate memory references, preventing these types of out-of-bounds writes.
Commit reference (WebKit):
- GitHub: WebKit fix for CVE-2022-26716
Resources And References
- Apple Security Update Page
- CVE-2022-26716 on NVD
- WebKit Bug Report 238029
- Project Zero Analysis
Conclusion
CVE-2022-26716 was a critical WebKit bug that put millions of Apple users at risk of silent compromise just by visiting a webpage. Apple’s quick patching kept users safe. But it’s a reminder: Keep everything updated, be careful online, and respect how complex browser security really is.
*Stay safe online! Always be ahead of the next CVE.*
Timeline
Published on: 11/01/2022 20:15:00 UTC
Last modified on: 11/03/2022 13:48:00 UTC